Published
- 4 min read
Let's Defend - PCAP Analysis

Description
We captured this traffic from P13's computer so can you help him?Tools
1- Wireshark
2- OSINT Tools
3- Reverse engineering
4- Python scriptingWriteup
Q1
in this challenge I got a network traffic.

so let’s openit and investigate that traffics.
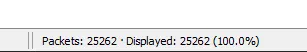
As we can see there are 25,262 packets so let’s filter the streams to TCP protocols and check if there is anything suspicious.
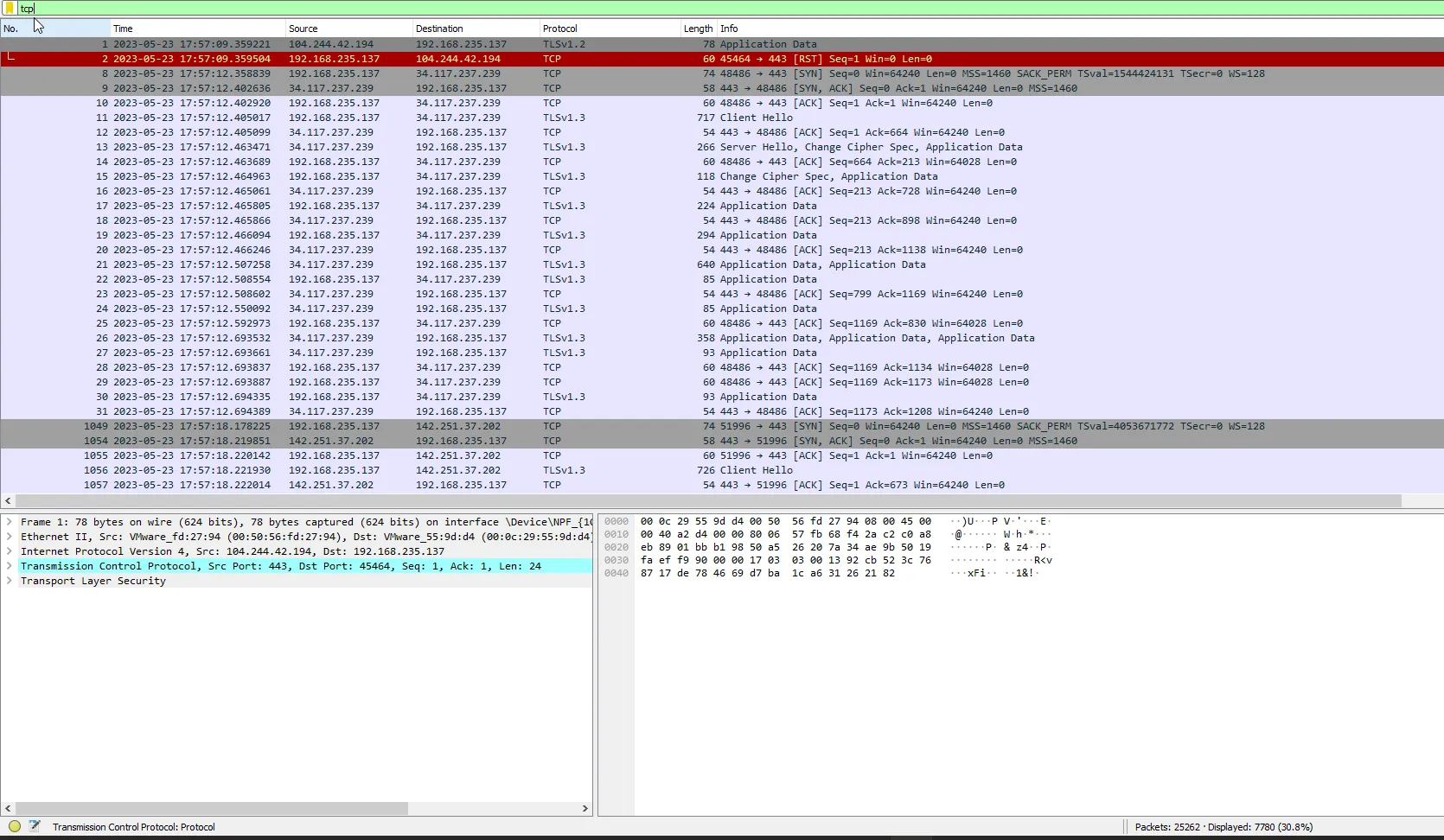
Okay got 7780 stream so let’s check the whole stream and find something interesting.
You can press -> CTRL + ALT + SHIFT + T
Or
Press Right click on any TCP stream -> Follow -> TCP Stream
we got 219 stream so let’s go through it quickly.
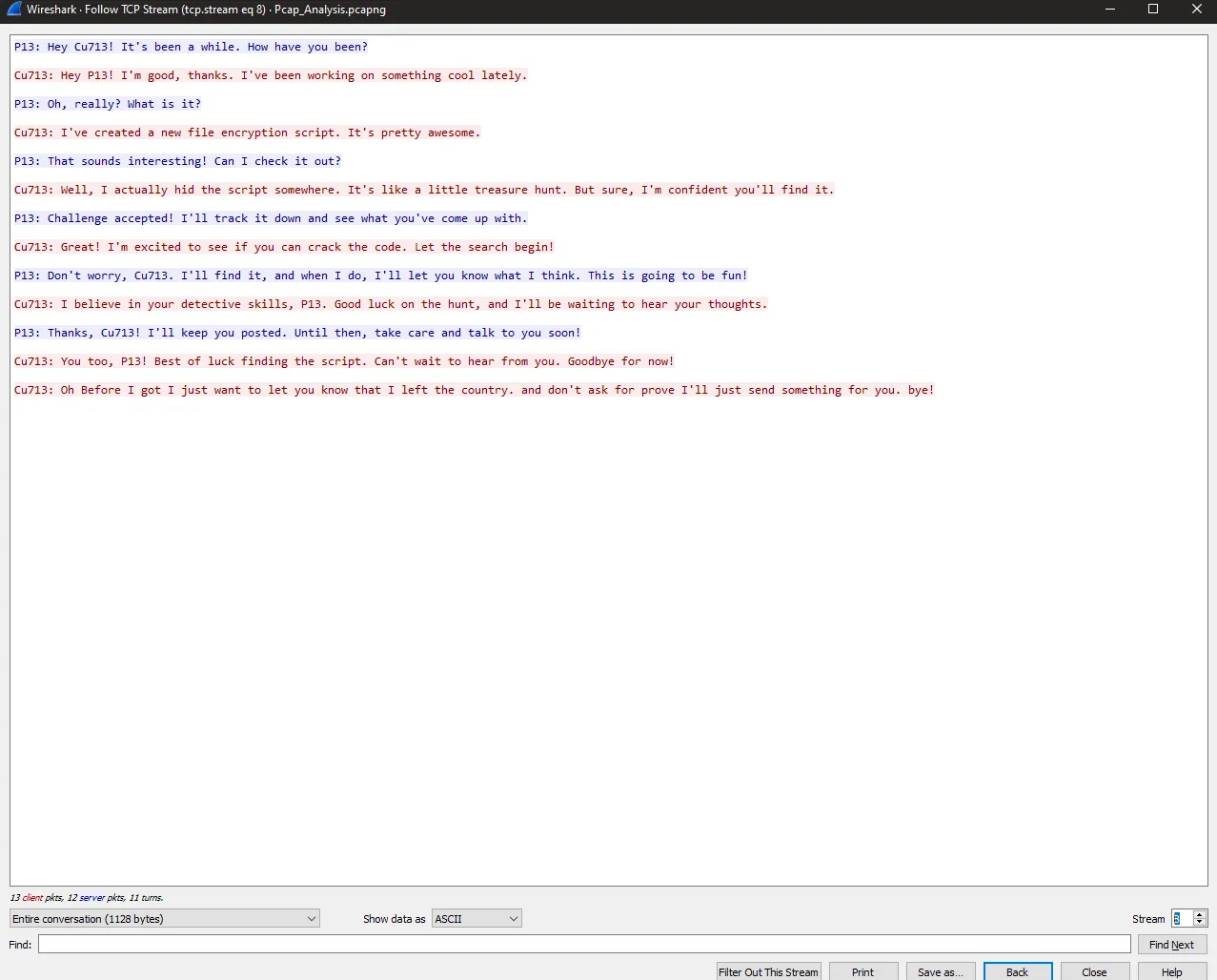
Okay on the 8th stream I got the chat between P13 and Cu713 and its about Cu713’s script and he hided it some where. but first question askes about the IP of sender and IP of the reciever. So
Q1 Answer: 192.168.235.137,192.168.235.131Q2
now Let’s head to the next question which asks about the file name that had sent through the network so let’s keep looking in the TCP streams.
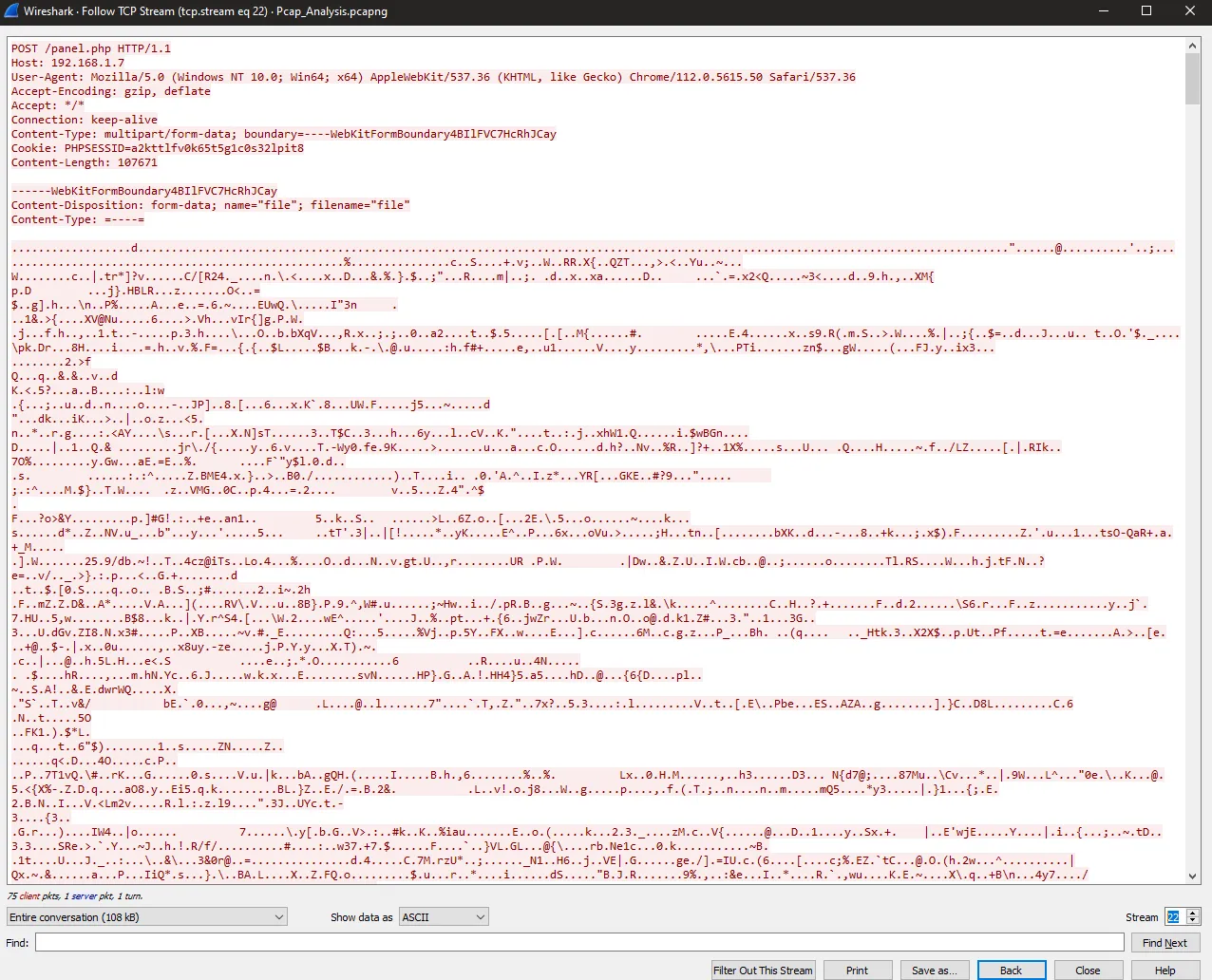
Okay on the 22th stream I found interesting file and got the filename
Q2 Answer: fileQ3
Now let’s head to the third question which is asking about where is the place that Cu713’s script hide.
Hint: Try To use OSINT on Cu713?So I used Cu713 as username and used instant username checker.
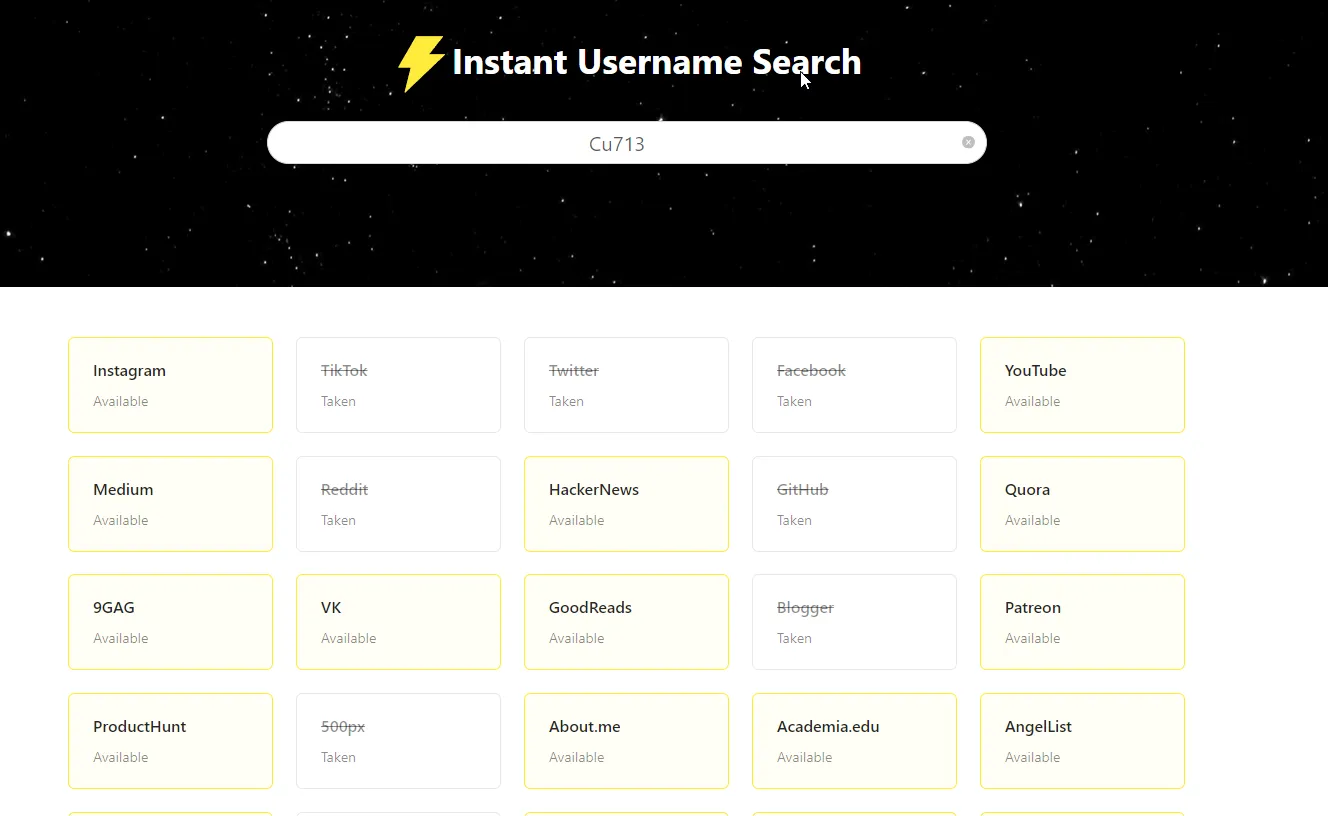
And yes found some interesting stuffs and I noticed that there is a github account so I opened it.
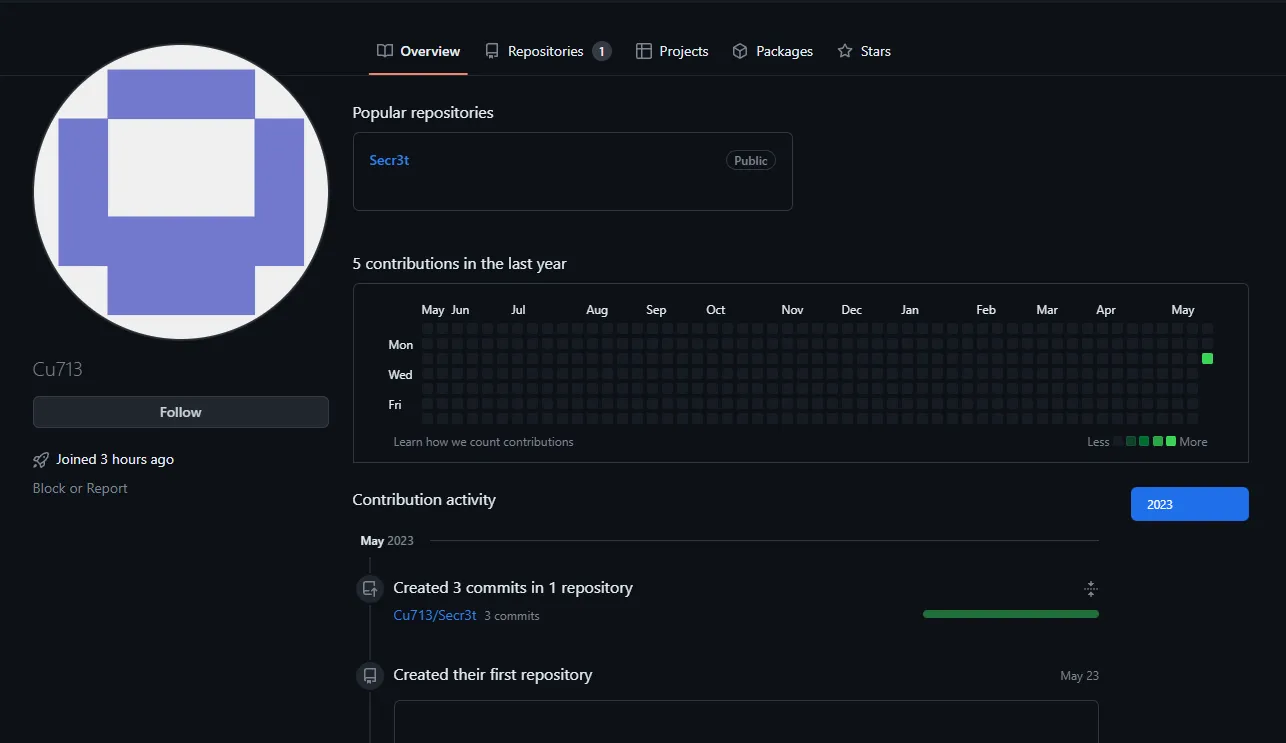
and yes now we got the answer for the question 3 which is
Q3 Answer : GithubQ4
Now let’s head to the 4th question which asks for the full url of that script. after going the repo on that account on github first you won’t find anything suspicious.
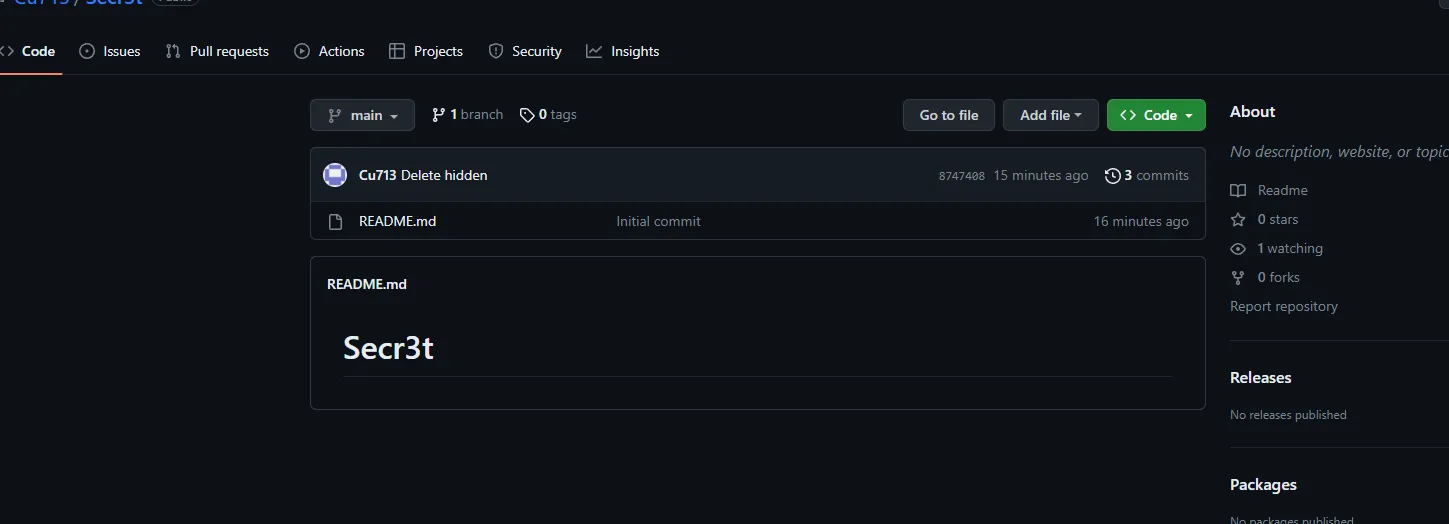
but if you foucsed you will find that Cu713 Deletes hidden!! so let’s go to commits.
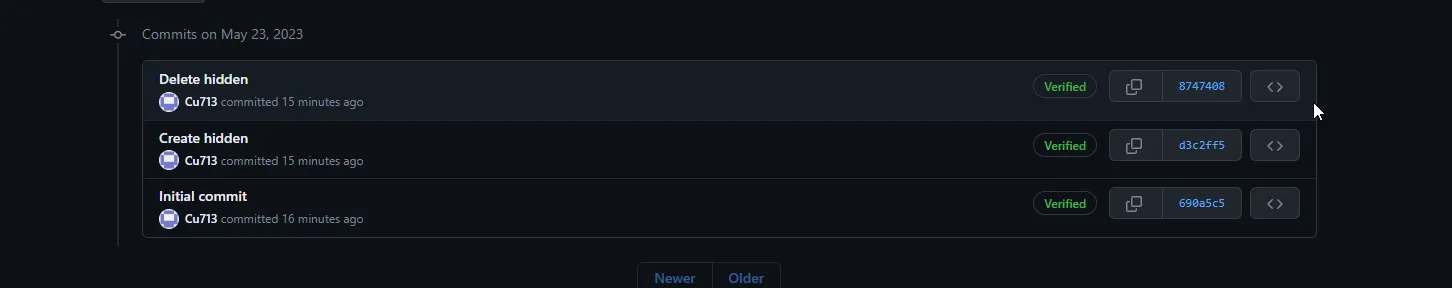
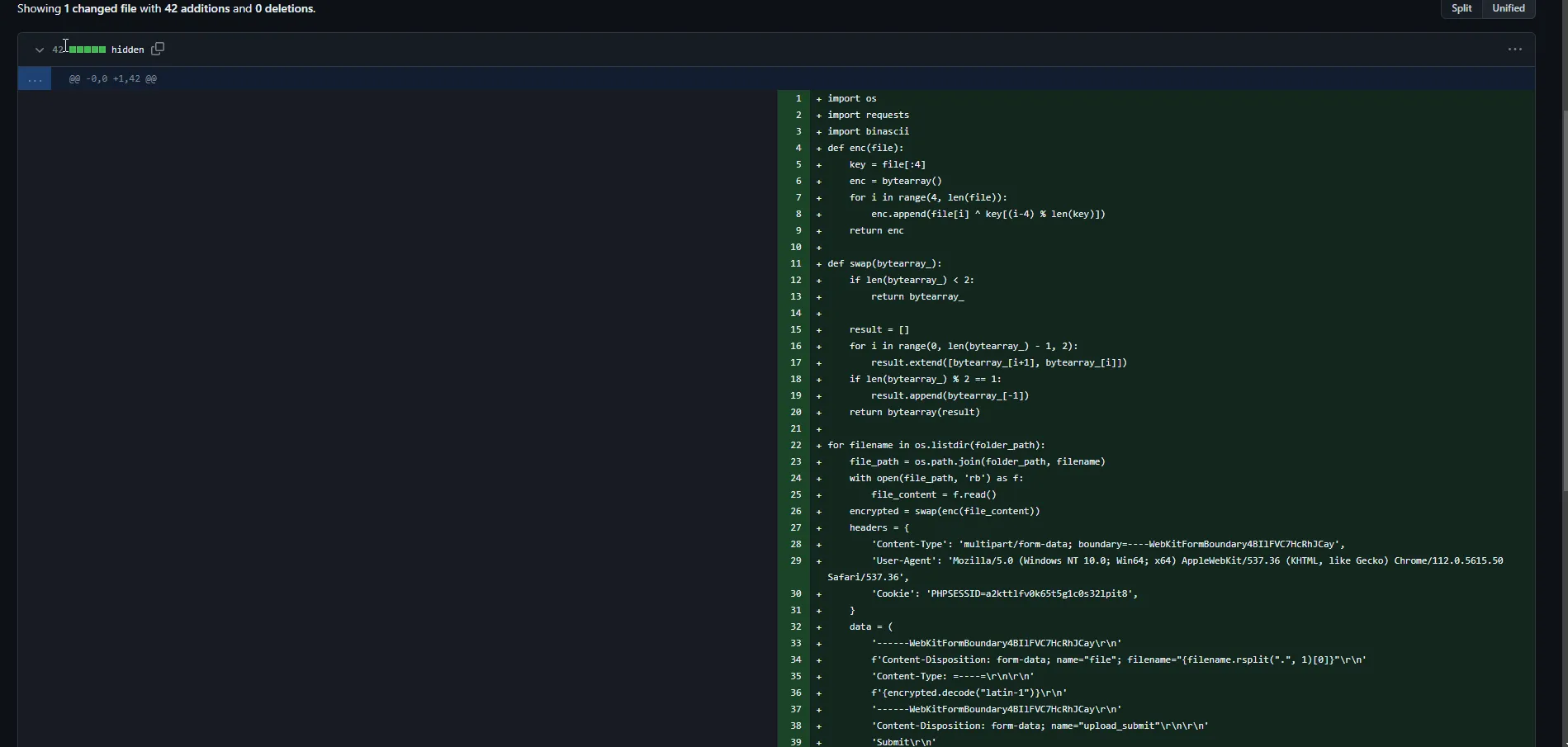
and yes we got the scipt now so answer for the 4th question is
Q4 Answer: https://github.com/Cu713/Secr3t/commit/d3c2ff53863d0fcc6f55c79d0d6799d40ca92820Q5
Let’s head to the 5th question which talk about reverse the file and reterive it.
Hint: You have the script maybe you need to use some reverse engineeing.First I extracted the data from the wireshark in these steps:-
1- I converted the stream of the file into raw and filtered it on cyberchef and extracted it so I can work on it.
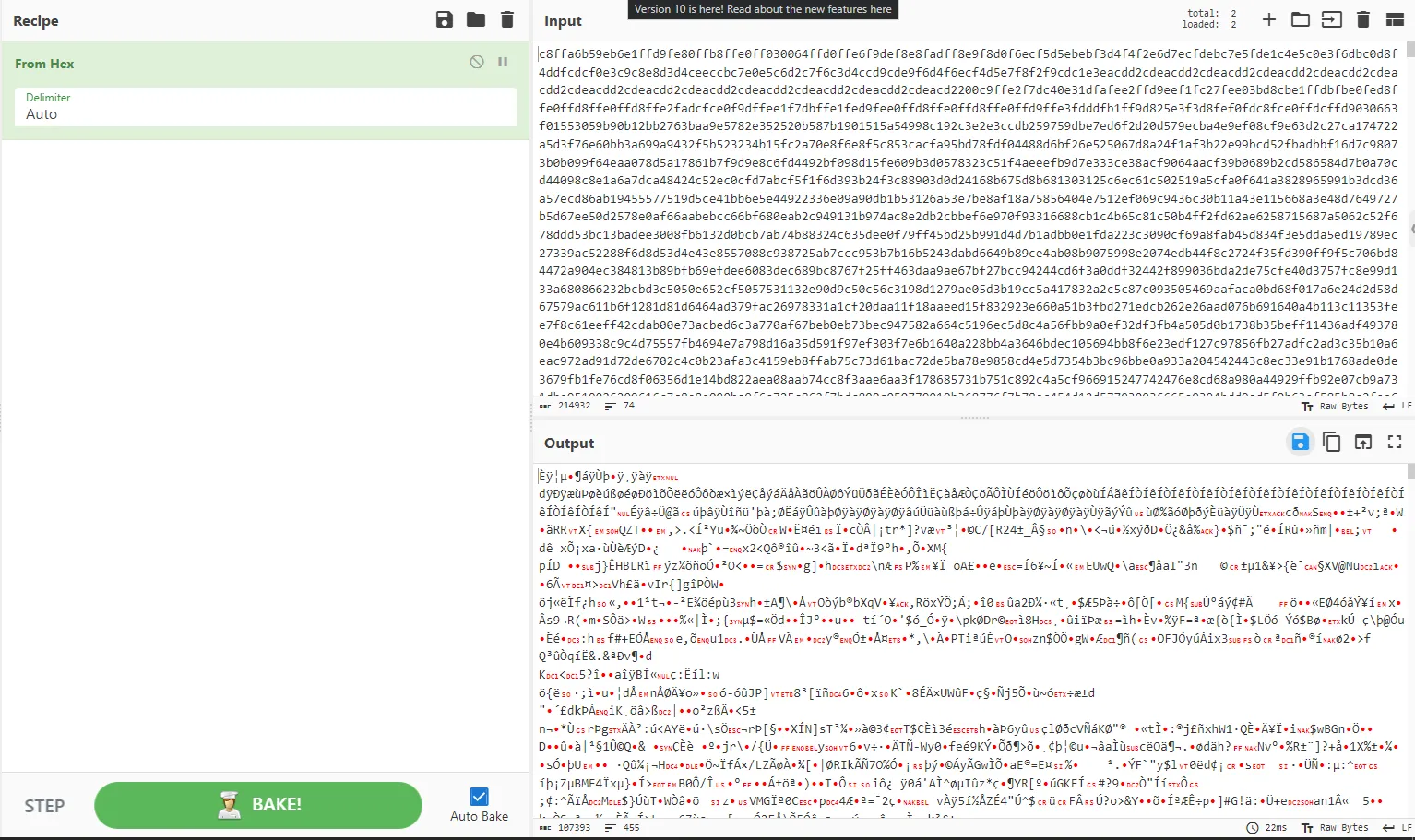
first I understood that script does 2 things. First he xor the bytes of the files with the first 4 bytes of the files which are Magic Signatures so I got the list of file signatures of the files for google. then it swaps every 2 bytes. so let’s first check the swap if it will work then do the decrypt.
Hint: it's an image filethe hint says its image file. so we have some types like (“PNG”, “JPG”,“GIF”,“BMP”) that made it more easier so after trying I noticed it’s a jpg. using this script
import binascii
with open('download.dat','rb') as f:
data = f.read()
def decrypt(message):
key = binascii.unhexlify("FFD8FFE0")
enc = bytearray()
for i in range(4, len(message)):
enc.append(message[i] ^ key[(i - 4) % len(key)])
return enc
def unswap_bytes(bytearray_):
if len(bytearray_) < 2:
return bytearray_
result = []
for i in range(0, len(bytearray_)-1, 2):
result.extend([bytearray_[i + 1], bytearray_[i]])
if len(bytearray_) % 2 == 1:
result.append(bytearray_[-1])
return bytearray(result)
dec = unswap_bytes(bytearray(data))
decrypted_message = decrypt(dec)
print(decrypted_message.decode('latin-1'))
there are IF like in the JPG.
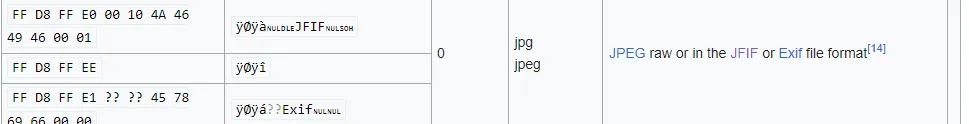 So the answer for the 5th question is
So the answer for the 5th question is
Q5 Answer: JPG/JPEGQ6
Let’s head to the 6th question which asks about where is Cu713’s location now after he left the country.
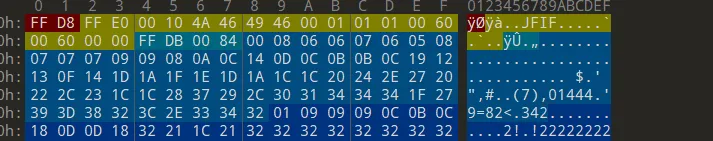
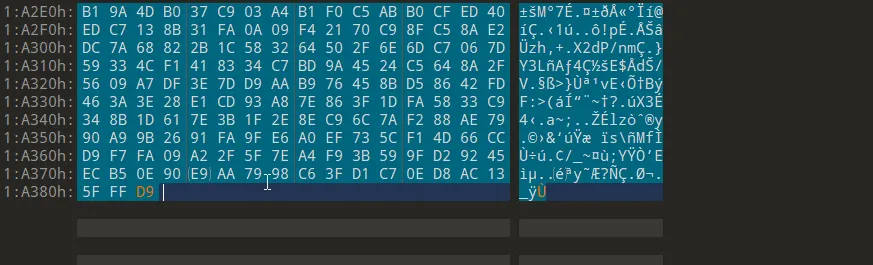
after fixing the footer and header of course no we got the image of his location.
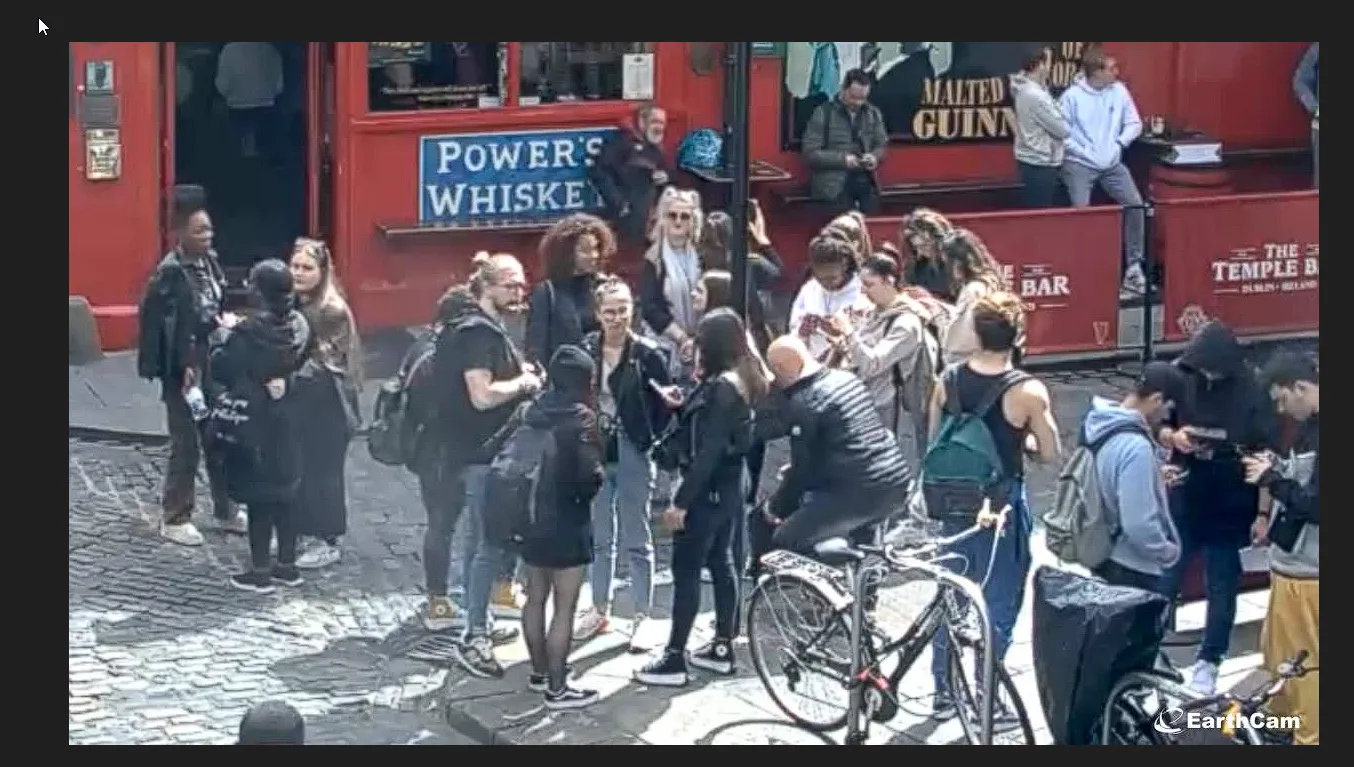
so the key of this image is ”the Temple Bar” on the right and ”Power’s Whiskey” on the center. so let’s google these two keywords.
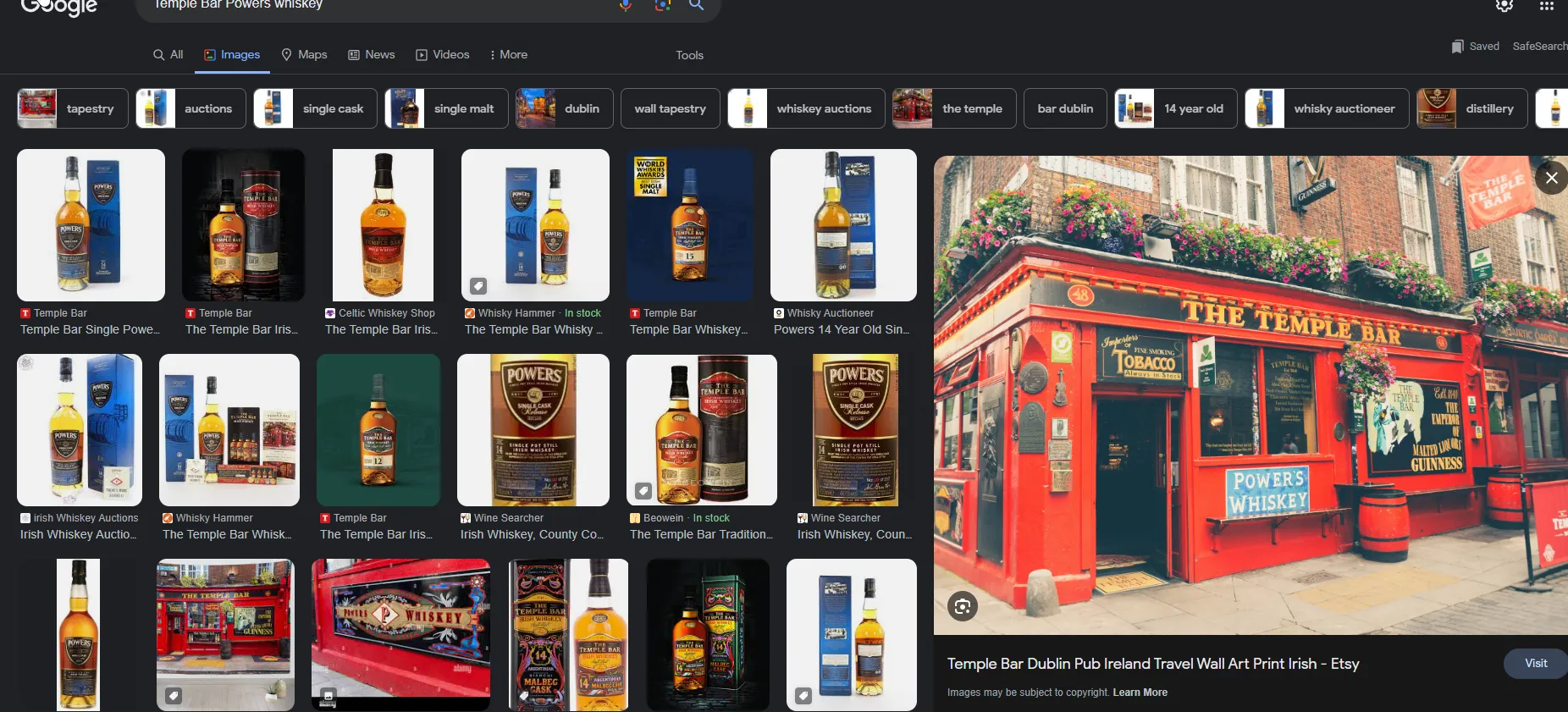
okay this interesting I found the same place. so let’s check where is this place exactly.

the answer for 6th question is
Q6 Answer: Dublin