Published
- 3 min read
Let's Defend - HackerMan

Description
An ex-employee, who appears to hold a grudge against their former boss, is displaying concerning behavior. We seek assistance in uncovering their intentions or plans.Tools
Tools Required
1- FTKimger
2- DB Browser
3- notepad++Writeup
Q1
What is the md5sum of the img?by unzipping challenge 7z we got a disk image to verify the img integrity Q1 is there so let’s run this command:
md5sum hackerman.imgthe answer is
6be42bac99e0fff42ca9467b035859a3
Q2
What is the sha256 hash of the file in the "hackerman" desktop?this is also easy question all u need to do is to dump the image in the Desktop of the user in the question and run sha256sum "FileName"
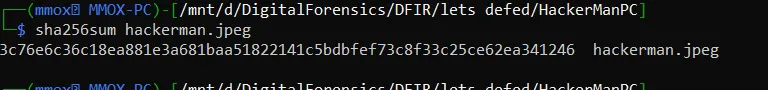
3c76e6c36c18ea881e3a681baa51822141c5bdbfef73c8f33c25ce62ea341246
Q3
What command did the user used to install Google chrome?for this question all u need to do is to chech the last command in the .bash_history file
sudo dpkg -i google-chrome-stable_current_amd64.deb
Q4
When was the Gimp app installed ?as we saw in the bash history it’s installed using apt so check the /var/log/apt/history.log
u will have the date and time
2023-05-06 10:49:42
Q5
What is the hidden secret that the attacker believes they have successfully concealed in a secret file?in the user directory there is a hidden file called .secrets
I_want_to_hack_my_Boss
Q6
What was the UUID of the main root volume?we will need to find the dmesg file in the /var/log
29153a2e-48a7-4e89-a844-dfa637a5d461
Q7
How many privileged commands did the user run?it’s an easy question all u need to do is to dump the auth.log file then run this command
cat auth.log | grep -i command | wc -l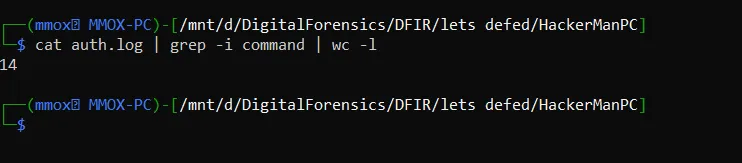
Q8
What is the last thing the user searches for in the installed browser?we only have 2 browsers installed over the machine so it’s logical to chech the browser that the user installed not the defualt one
so u need to dump the History database fromt the /home/hackerman/.config/google-chrome/Default using sqllite browser to open the history u will get the answer
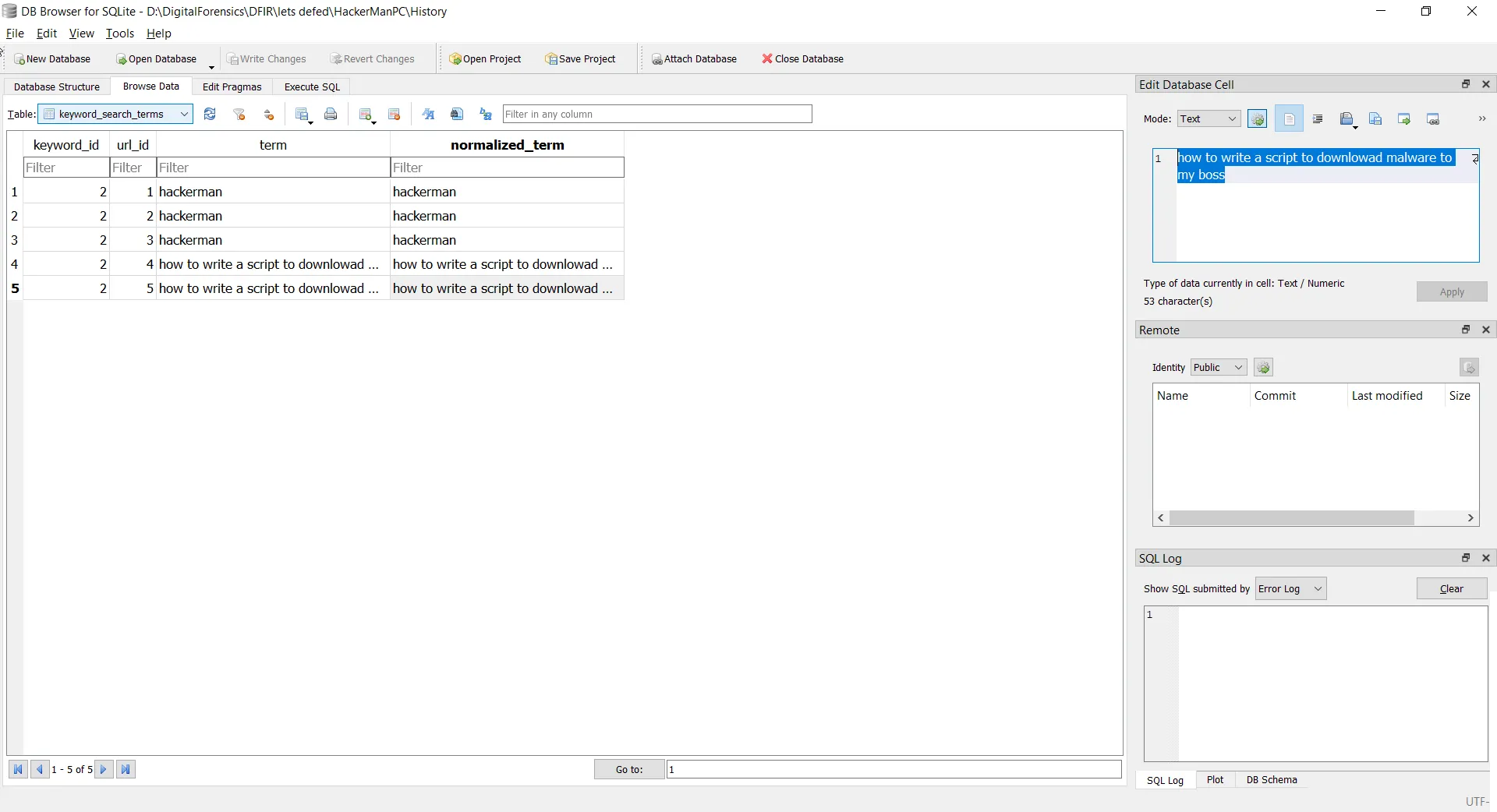
how to write a script to downlowad malware to my boss
Q9
From Q8 we know that the user tried to write a script, what is the script name that the user wrote?by checking the bash history u will find the script name but u will need to search the directories to get it but the hint guieded u to the tmp
superhackingscript.sh
Q10
what is the url that the user uses to download the malware? by opening the script from Q9 u will find the url
Q11
What is the name of the malware that the user tried to download?using virus total with the hash in the script it will gave u the malware name
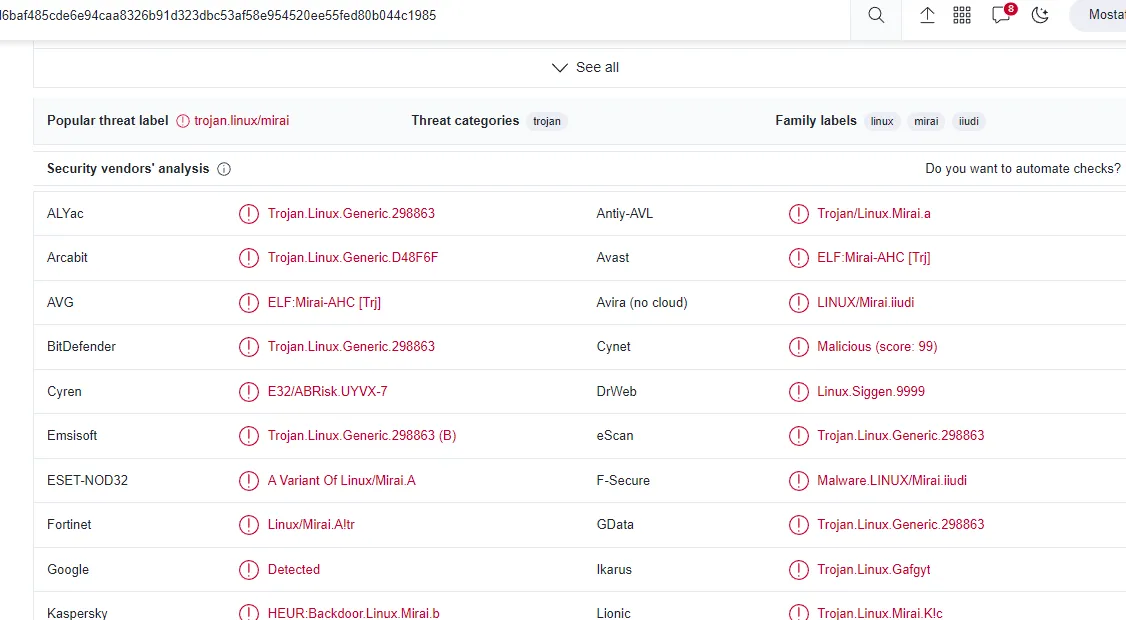
Miria
Q12
What is the IP address associated with the domain that the user pinged?by checking the /etc/hosts file u will get the answer
185.199.111.153
Q13
What is the password hash of the ‘hackerman’ user? by dumping the /etc/shadow and /etc/passwd then running
unshadow passwd shadow > output.txtby opening the output.txt u will have the hash
$y$j9T$71dGsUtM2UGuXod7Z2SME/$NvWYKVfU9fSpnbbQNbTXcxCdGz4skq.CvJUqRxyKGx6