Published
- 3 min read
Let's Defend - Cl0p

Description
Our friend fell victim to a ransomware attack and reached out to seek your expertise in analyzing the system to uncover the cause of the breach. We have provided you with a memory dump of his computer as the starting point for your investigation.Tools
Tools Required
1- Volatility
2- Notepad++
3- VirusTotal or VM.Writeup
Q1
What is the dump profile?Well by checking the file we got it’s a memory dump so we are going to use volatility in this case for our investigations.
so we need to get the profile. there are two ways to get it in volatility2 by using imageinfo or kdbgscan but I prefer kdbgscan cause it’s faster.
python2 /mnt/d/volatility/vol.py -f Ransom-Snapshot14.vmem kdbgscanwe will notice it’s a linux distribution so we can get the version by visiting ‘etc/lsb-release’
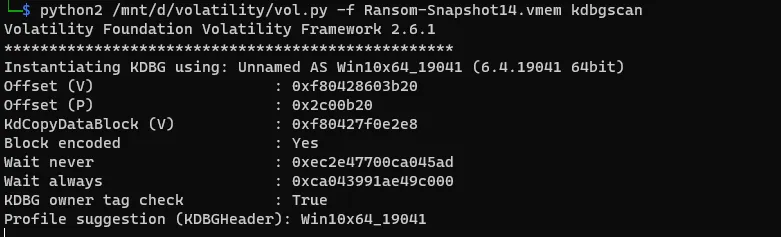
the answer is
Win10x64_19041
Q2
What is the parent process of the ransomware?if you tried to do psscan you will see the list of the process but to make it more clear for us we will use the command like in hint pstree
python2 /mnt/d/volatility/vol.py -f Ransom-Snapshot14.vmem --profile=Win10x64_19041 pstree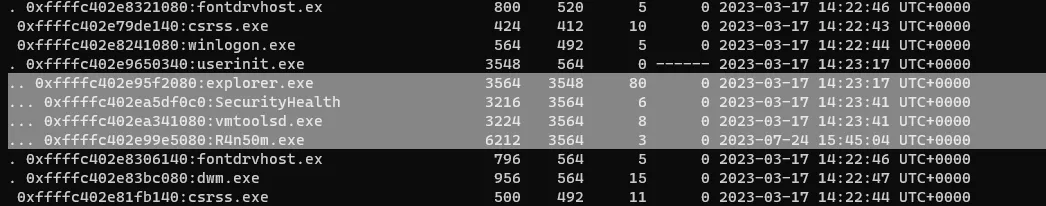
we will see the R4n50m.exe but we need the parent process so the answer is
explorer.exe
Q3
The ransomware encrypted data with specific extension. what is the extension?if we check the hint it says check desktop directory. so we can run filescan first and check the desktop then.
python2 /mnt/d/volatility/vol.py -f Ransom-Snapshot14.vmem --profile=Win10x64_19041 filescan > files.txt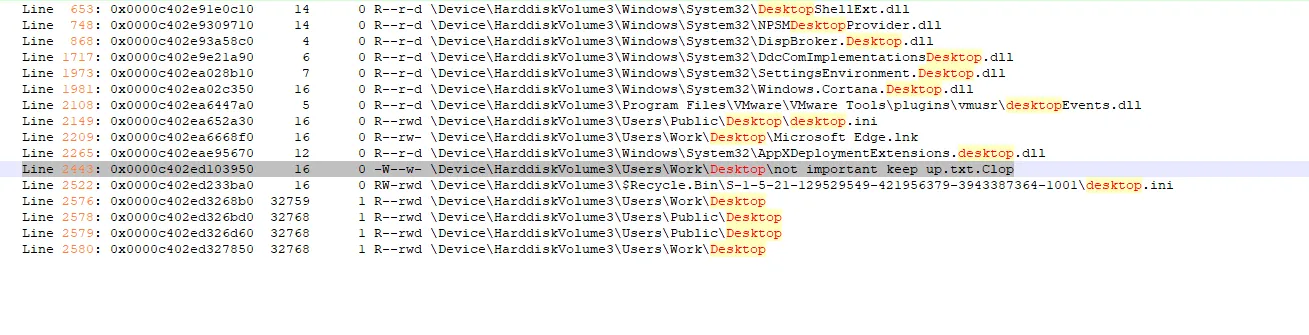 it’s interesting now we found txt file encrypted on the desktop so the answer
it’s interesting now we found txt file encrypted on the desktop so the answer
.Clop
Q4
The ransomware was hidden in windows so can you find the full path.if we check the hint it says the Temp folder. so let’s grep the Temp folder from the files.txt we got.
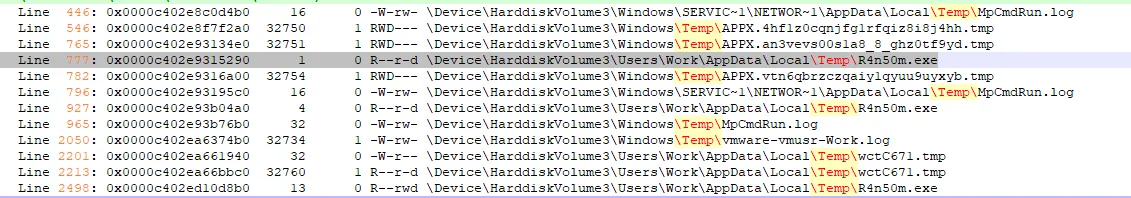
and yes found it and the answer is
\Users\Work\AppData\Local\Temp\R4n50m.exe
Q5
What is DTB of the ransomware?this could take time of searching but after checking the hint it says “volshell is good for this”. so let’s run volshell and investigate.
python2 /mnt/d/volatility/vol.py -f Ransom-Snapshot14.vmem --profile=Win10x64_19041 volshell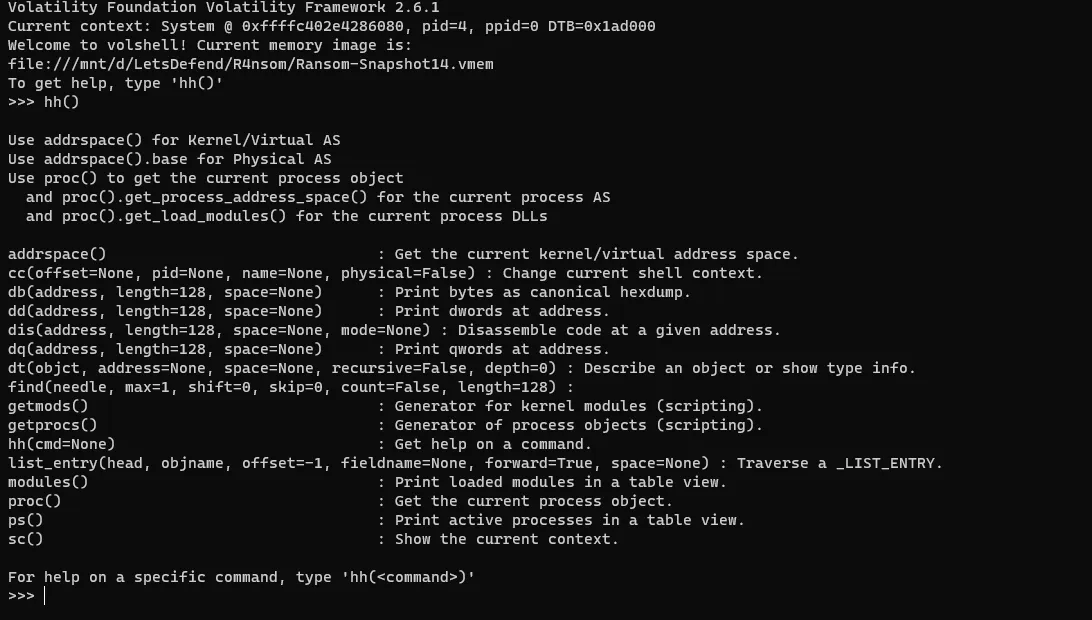
if we pressed hh() we will get all the help list. so let’s list the process first and get the offset of the ransomware ps().
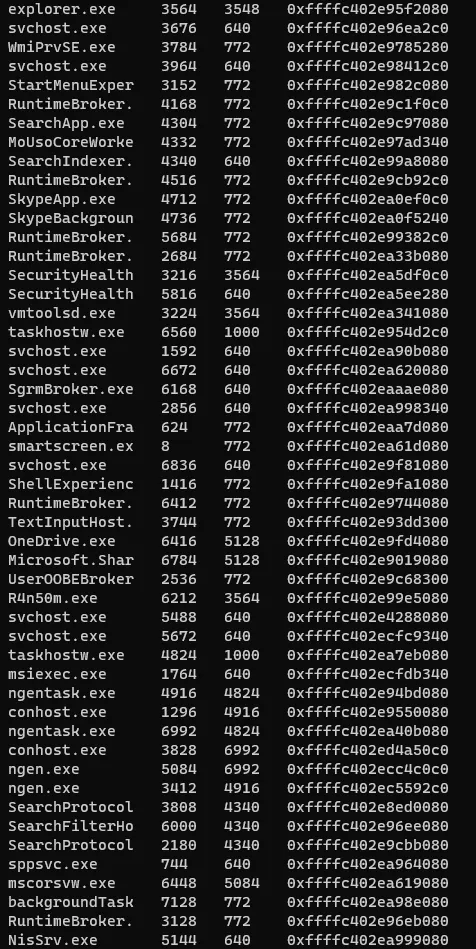
now we got the offset of the ransom so let’s run the cc(0xffffc402e99e5080) and see what we will get.
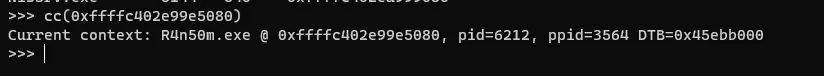 and yes we got the DTB
and yes we got the DTB
0x45ebb000
Q6
What is the Mitre ID of the Obfuscated Files or Information?this would take a little bit of time. but if we check the hint it says ‘You know the ransomware then check his mitre attack report.’ so let’s google for Clop ransomware mitre report.
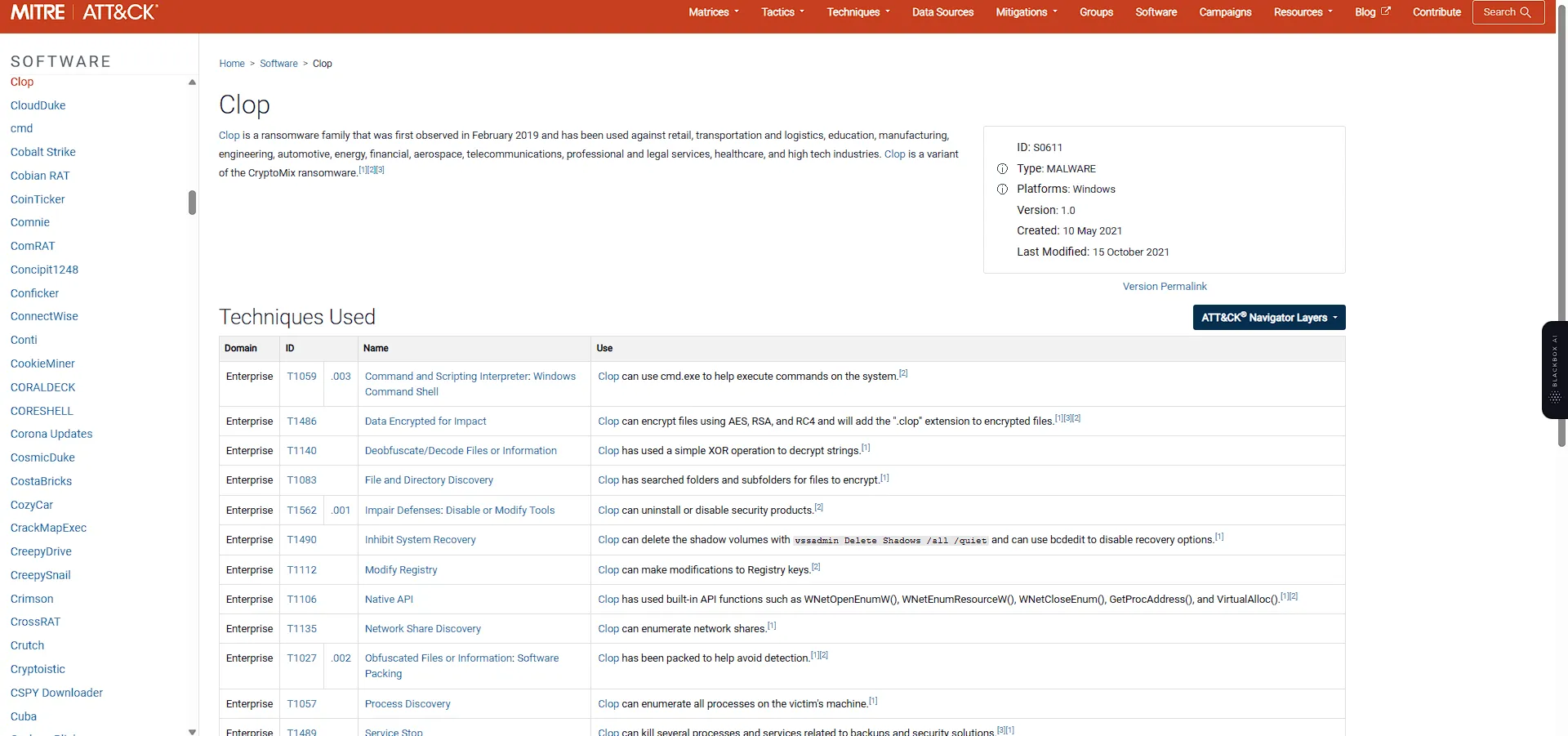 and yes this is really interesting. I found the correct Mitre ID.
and yes this is really interesting. I found the correct Mitre ID.
T1027
Q7
The ransom dropped a readme message but it seems we couldn't dump it. we need to find the email of the managethis would take a little bit of time. it says we couldn’t dump it and yes I couldn’t find the readme in the files.txt we got. so the hint says ‘Online analyzer or maybe use VM ?’. so I tried to dump process of the ransomware.
python2 /mnt/d/volatility/vol.py -f Ransom-Snapshot14.vmem --profile=Win10x64_19041 procdump -p 6212 -D out/and upload it to virus total and hybird analysis. and yes I found it drops file called ClopReadMe.txt
 but I still need to open it. so I cut the way to the half. and created a windows virtual machine. and run the ransomware on it. instead of open it on IDA. and yes that works.
but I still need to open it. so I cut the way to the half. and created a windows virtual machine. and run the ransomware on it. instead of open it on IDA. and yes that works.
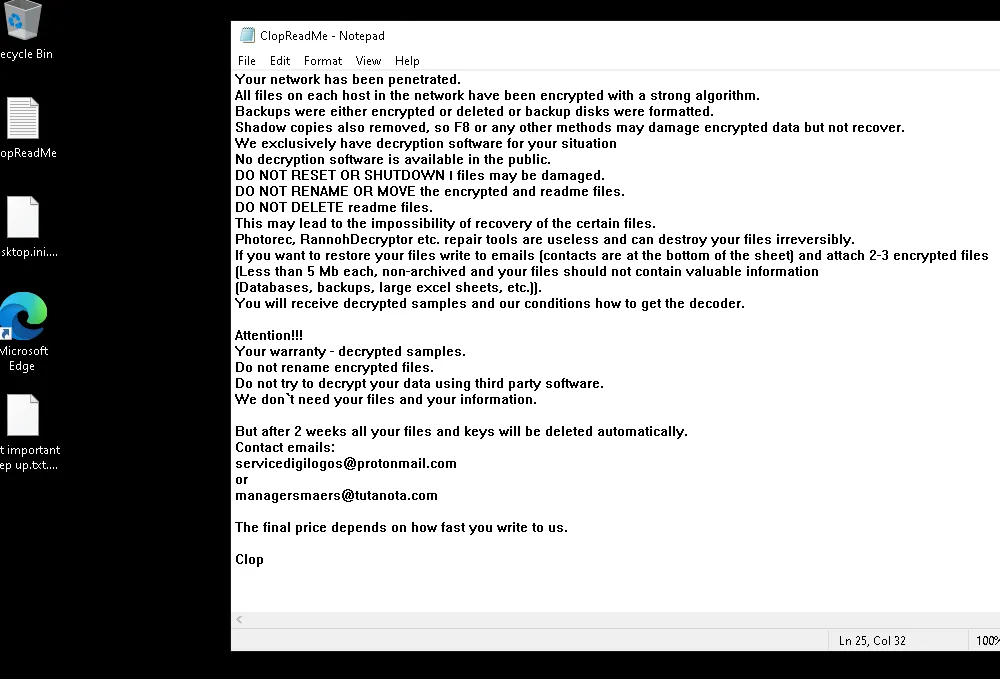
So we got the answer now.