Published
- 4 min read
ICMTC Finals 2023 Digital Forensics writeups

ICMTC Finals 2023 Forensics writeups
Hello, It’s xElessaway, and we here is my writeups for the digital forensics challenges at Military Technology College in Cairo. I hope you enjoy it.
* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Devil Init Persistence | Digital Forensics | 356 |
| MegaMind | Digital Forensics | 436 |
| Ransomware | Digital Forensics | 500 |
| Invade | Digital Forensics _| 500 |
+ — — — — — — — — + — — — — — — — -+ — — — — +So, let’s head to the first challenge with is “Devil Init Persistence”.
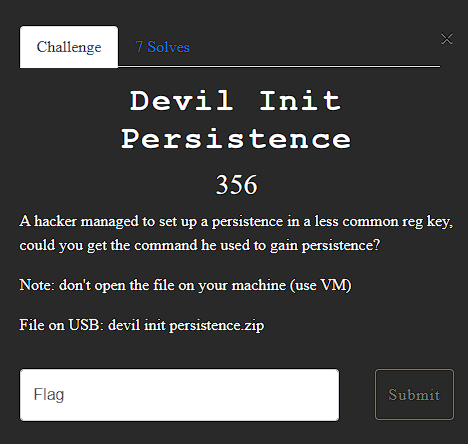
Challenge Description
this one wasn’t that hard to solve. but let’s take a look like it’s our first time and how to think about it. We got a “.reg” file which is windows registry file. we can open it with multiple tools but I’ll use “Registry Workshop”.
We got a “.reg” file which is windows registry file. we can open it with multiple tools but I’ll use “Registry Workshop”.
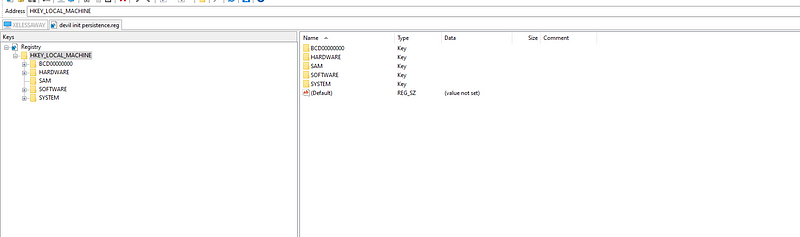 Okay this reg is “LOCAL_MACHINE” so if we checked the common keys “Run”, “RunOnce” we won’t get anything so it’s simple we can google about where is the common places to set up persistence.
Okay this reg is “LOCAL_MACHINE” so if we checked the common keys “Run”, “RunOnce” we won’t get anything so it’s simple we can google about where is the common places to set up persistence.
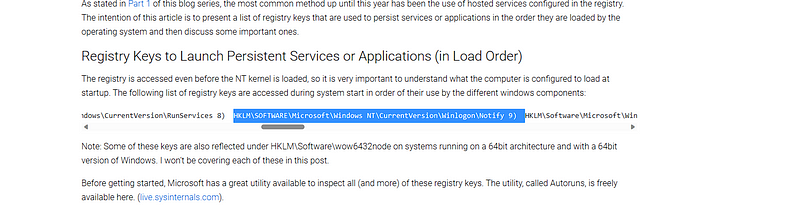 we got this key while googling. so let’s check it in our “reg”.
we got this key while googling. so let’s check it in our “reg”.
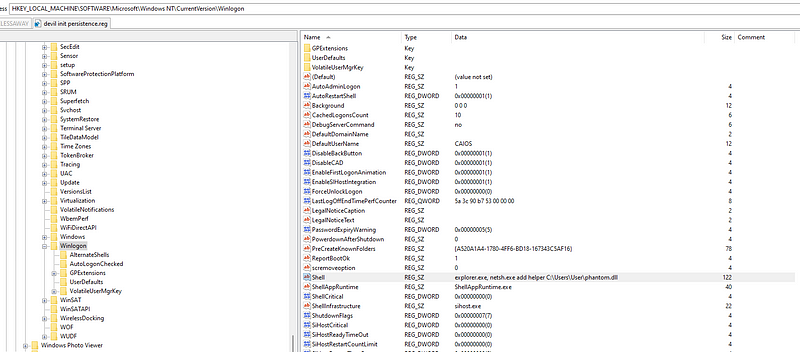 while going there you will notice a shell key with command “netsh” so this is the flag
while going there you will notice a shell key with command “netsh” so this is the flag
EGCERT{netsh.exe add helper C:\\\\Users\\\\User\\\\phantom.dll}Good, Now let’s head to the second Challenge which is MegaMind. actually, I’m not the one who solve it, but it was “Youssef Hegazy” my teammate.
 So, in this challenge. we got an “APK” file, so we need to investigate this application and get the file name.
So, in this challenge. we got an “APK” file, so we need to investigate this application and get the file name.
 We got also the databases of the apk. so, we can open them on “SQLite Browser”.
We got also the databases of the apk. so, we can open them on “SQLite Browser”.
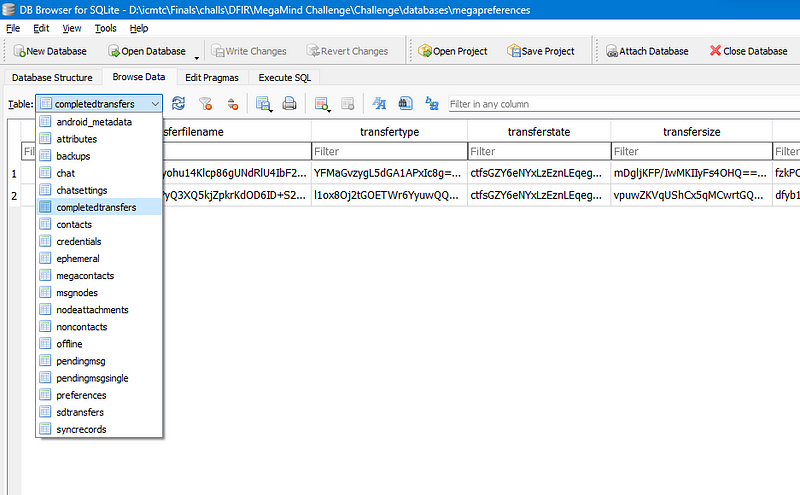 in megapreferences database file we got completed transferes but it was encoded with base64. so let’s try to decode it.
in megapreferences database file we got completed transferes but it was encoded with base64. so let’s try to decode it.
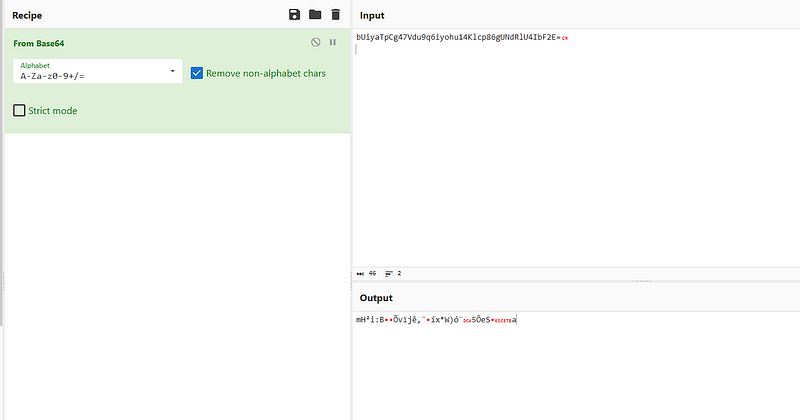 but nothing. well, this makes a sense because why application like mega would save the database in just base64 encoding. so, let’s keep googling for more information.
but nothing. well, this makes a sense because why application like mega would save the database in just base64 encoding. so, let’s keep googling for more information.
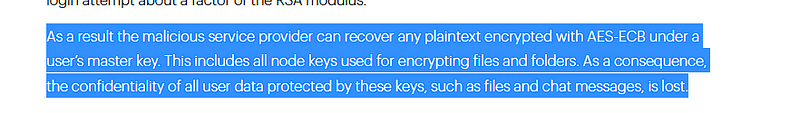 I got a good one which is talking about AES-ECB and this encryption methods takes only one key and no need for IV so let’s investigate it and try to find the key.
I got a good one which is talking about AES-ECB and this encryption methods takes only one key and no need for IV so let’s investigate it and try to find the key.
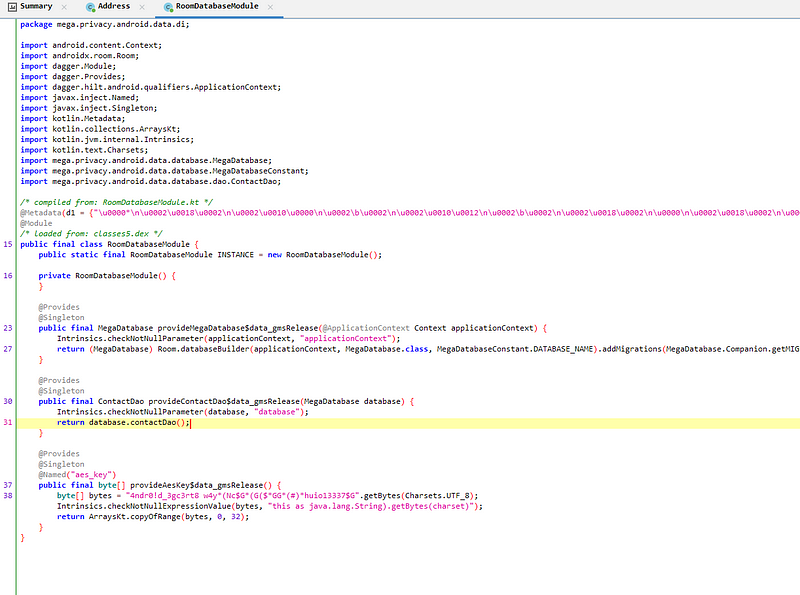 I used JADx to decompile the APK so everything could be clear for me to read. as I said my teammate who solved it found a string “4ndr0!d_3gc3rt8 w4y*(Nc$G*(G($*GG*(#)*huio13337$G” and above it there is a key called “aes_key” so I think now we are close to get the flag. so, this part says we take only first 32 bytes of that string so let’s take it as a key and decode it.
I used JADx to decompile the APK so everything could be clear for me to read. as I said my teammate who solved it found a string “4ndr0!d_3gc3rt8 w4y*(Nc$G*(G($*GG*(#)*huio13337$G” and above it there is a key called “aes_key” so I think now we are close to get the flag. so, this part says we take only first 32 bytes of that string so let’s take it as a key and decode it.
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
import base64
\# Define the key and the encrypted data
key\_string = "4ndr0!d\_3gc3rt8 w4y\*(Nc$G\*(G($\*GG\*(#)\*huio13337$G"
key\_bytes = key\_string.encode('utf-8')
key\_32\_bytes = key\_bytes\[:32\]
encrypted\_data = base64.b64decode('bDYn7kAniulcMw5N9PyQ3XQ5kjZpkrKdOD6ID+S2Mdo=')
cipher = Cipher(algorithms.AES(key\_32\_bytes), modes.ECB())
decryptor = cipher.decryptor()
decrypted\_data = decryptor.update(encrypted\_data) + decryptor.finalize()
print(decrypted\_data)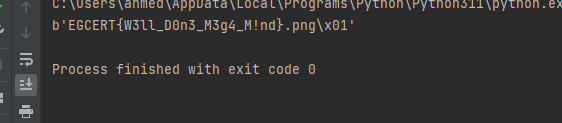
EGCERT{W3ll\_D0n3\_M3g4\_M!nd}and for the most saddest challenge in my life xDD I got no internet to submit the flag in the last 2mins in the competetion. so let’s stop talking and solve this challenge.
 This challenge is really good one.
This challenge is really good one.
 We got event logs, registry and the MFT. so as usual the description says A ransomware infected the machine. so, we need to open the logs and check the suspicious behavior or any interesting logs.
We got event logs, registry and the MFT. so as usual the description says A ransomware infected the machine. so, we need to open the logs and check the suspicious behavior or any interesting logs.
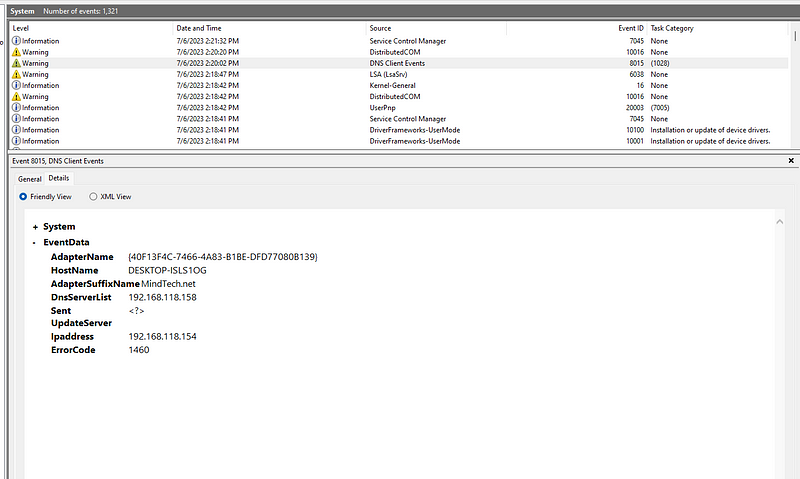 in logs the only interesting thing is the connection that happened between the machine and server. so that let us ask why this connection happened ?
well maybe to drop the ransomware !!! good. but still, we need to get the ransomware. so, we won’t find any interesting information in registry expect if we checked Run and RunOnce. but it’s empty. so, let’s parse the MFT using “MFTECmd.exe” but I don’t recommend this one it’s really good but it will hurt your eyes like this
in logs the only interesting thing is the connection that happened between the machine and server. so that let us ask why this connection happened ?
well maybe to drop the ransomware !!! good. but still, we need to get the ransomware. so, we won’t find any interesting information in registry expect if we checked Run and RunOnce. but it’s empty. so, let’s parse the MFT using “MFTECmd.exe” but I don’t recommend this one it’s really good but it will hurt your eyes like this
 it’s like 302562 rows so we can’t focus looking like this. but we can use something interesting to make everything clear for us like “MFTExplorer.exe”. this one is a GUI MFT parser.
so, we have only one user “Workstation_1” so we need to investigate all interesting possibilities to locate the ransomware. so, after searching you will find interesting executable file called “KYZFK5CTI5DDEWSTGFBEYVTEOBRG2NLMMNTT2PI.exe” in Documents folder.
it’s like 302562 rows so we can’t focus looking like this. but we can use something interesting to make everything clear for us like “MFTExplorer.exe”. this one is a GUI MFT parser.
so, we have only one user “Workstation_1” so we need to investigate all interesting possibilities to locate the ransomware. so, after searching you will find interesting executable file called “KYZFK5CTI5DDEWSTGFBEYVTEOBRG2NLMMNTT2PI.exe” in Documents folder.
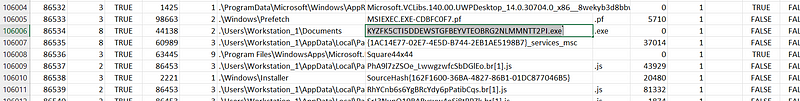 MFT Parser CMD
let’s try to decrypt this weird string.
MFT Parser CMD
let’s try to decrypt this weird string.
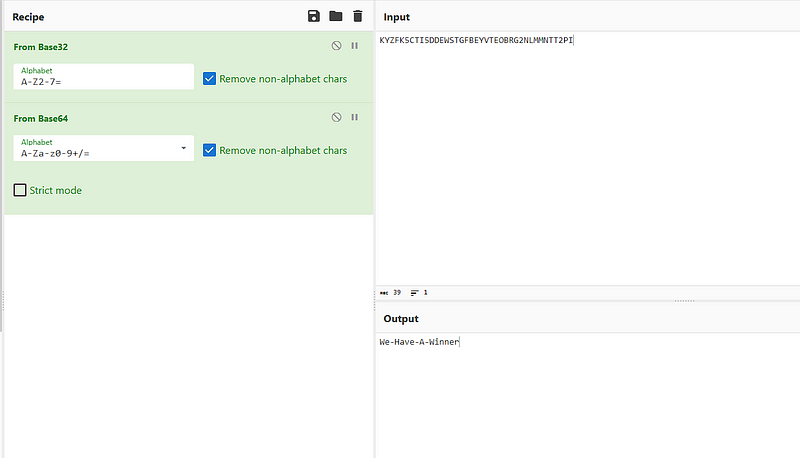 and sadly, I wasn’t that winner :( but Alhamdulillah’s and congratz for all the winners ❤.
and sadly, I wasn’t that winner :( but Alhamdulillah’s and congratz for all the winners ❤.
EGCERT{We-Have-A-Winner}and for the last one. it’s about building volatility profile.
 I got no time sadly but I’m sure I could solve it.
all you need to find the correct volatility profile there are many ways to find it. you can check this write up for how I can find the correct profile and build it.
I got no time sadly but I’m sure I could solve it.
all you need to find the correct volatility profile there are many ways to find it. you can check this write up for how I can find the correct profile and build it.
CTFtime.org / HTB Business CTF 2021 / Compromised / Writeup
after getting the profile you can go through the challenge and solve it.
and I hope you enjoyed my write up. and see you in the next competitions ❤.
By Ahmed Elessaway on July 18, 2023.