Published
- 12 min read
0xL4ughCTF 2023 DF Writeups

0xL4ugh CTF 2023
Hello, It’s xElessaway, first it was my pleasure to create the Forensics, Steganography challenges in 0xL4ugh CTF 2023. Second Challenges were made for players to learn something new in CTF but my first aim was to the players who want to start playing CTFs so I thought these challenges would be significant for their start. so enough talks and here is the write-up for my challenges. I hope you enjoy it.
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody|_ Steganography _| 25 |
| Weirdoooo|_ Steganography _| 25 |
| Uraa |_ Steganography _| 50 |
| Zar |_ Steganography _| 50 |
| Colorful |_ Steganography _| 100 |
| Deep | Forensics | 200 |
| PVE | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +Okay, Let’s start with Bloody and see how we will go.
Description: just line ? but it contain a lot of infoooooooosin the challenge, we got a “png” file. so it’s one image hmmm let’s try some tools on it like
Strings - exiftool - zsteg- etc so let’s try to see if there are any hidden data in it using “binwalk”.
so let’s try to see if there are any hidden data in it using “binwalk”.
binwalk filename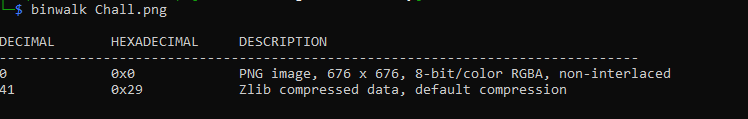 BRUH… There is nothing. but why this “PNG” contains just one line ???
what about extracting pixels values? let’s write down a script for it
BRUH… There is nothing. but why this “PNG” contains just one line ???
what about extracting pixels values? let’s write down a script for it
import numpy as np
from PIL import Image
import random
img = Image.open('Chall.png')
pix = img.load()
w, h = img.size
flag = ''
for i in range(w):
for c in range(h):
r,g,b,a = img.getpixel((i,c))
if r == 255 and g == 255 and b == 255:
pass
else:
print(r,g,b,a)
print(flag) Okay if we removed the white spaces we find some interesting pixels of the line. but if we notice that only red changes oohhhh now I understand why the challenge is called Bloody -> Red. so let’s try to decode only the red channel
Okay if we removed the white spaces we find some interesting pixels of the line. but if we notice that only red changes oohhhh now I understand why the challenge is called Bloody -> Red. so let’s try to decode only the red channel
import numpy as np
from PIL import Image
import random
img = Image.open('Chall.png')
pix = img.load()
w, h = img.size
flag = ''
for i in range(w):
for c in range(h):
r,g,b,a = img.getpixel((i,c))
if r == 255 and g == 255 and b == 255:
pass
else:
if flag.endswith("}"):
break
else:
flag += chr(r)
print(flag)OKAYYY LET’S GOO.
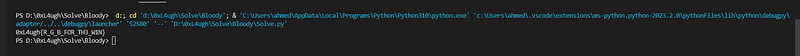
FLAG: 0xL4ugh{R_G_B_FOR_TH3_W1N}+ — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| 25 |
| Weirdoooo |_ Steganography _| 25 |
| Uraa |_ Steganography _| 50 |
| Zar |_ Steganography _| 50 |
| Colorful |_ Steganography _| 100 |
| Deep | Forensics | 200 |
| PVE | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now let’s move to the second challenge “Weirdooo” and see what you need from me this time :)))
Description: Too many numbers but i guess you know what you should do.We got a “ZIP” File containing a text file
 good xElessaway didn’t give me an image but this time gave something I can rea.. man ??? wtf is dis
good xElessaway didn’t give me an image but this time gave something I can rea.. man ??? wtf is dis
 AHHH now what is this let me zoom out so if I can see anything suspicious
AHHH now what is this let me zoom out so if I can see anything suspicious
 Okay my eyes hurt now but luckily I got something HAHA
Okay my eyes hurt now but luckily I got something HAHA

The Flag is “0xL4ugh{BJHGUIFJGUIJF}Yes here is my flag boiz. but submission said
 so I had to go again and see what is this??? so let’s zoom in on this part I found useful
so I had to go again and see what is this??? so let’s zoom in on this part I found useful
 ohohoh it’s 255 and some numbers beside zeros so it might be pixel values so let’s make a script to put every pixel in his place but wait a minute!! where are the dimensions? Okay I’m a genius now so let’s check how many rows and columns
ohohoh it’s 255 and some numbers beside zeros so it might be pixel values so let’s make a script to put every pixel in his place but wait a minute!! where are the dimensions? Okay I’m a genius now so let’s check how many rows and columns
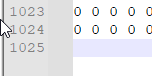 Columns
But let’s think there are spaces between each value so 2048/2 = 1024
so our dimensions are “1024 x 1024” now let’s write down our cute script ❤
Columns
But let’s think there are spaces between each value so 2048/2 = 1024
so our dimensions are “1024 x 1024” now let’s write down our cute script ❤
import numpy as np
from PIL import Image as im
import cv2
with open('weirdoooo.txt', 'r') as f:
data = f.read().split('\\n')
data2 = \[\]
\# create empty img 1024\*1024
img = np.zeros((1024,1024))
for i in range(len(data)):
data2.append(data\[i\].split(' '))
for i in range(len(data2)):
for j in range(len(data2\[i\])):
if data2\[i\]\[j\] == '':
pass
else:
img\[i\]\[j\]=data2\[i\]\[j\]
print(img.shape)
out=img.astype(np.uint8)
out = im.fromarray(out)
#out.convert()
out.save('flag.png')
flag = cv2.imread('flag.png')
cv2.imshow('flag',flag)
cv2.waitKey(0)and yes this works now :”DDD
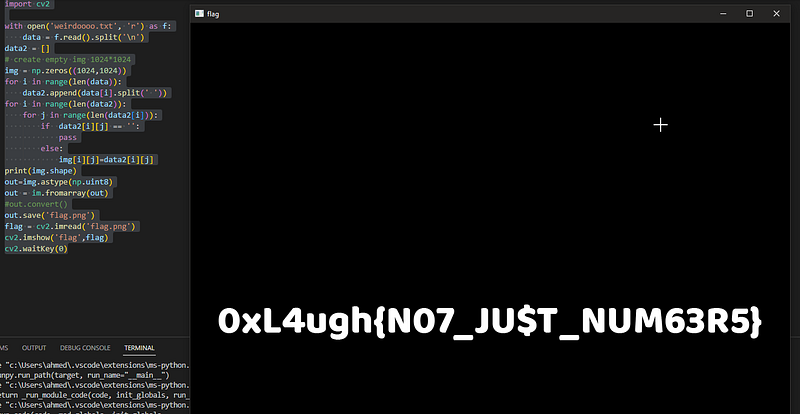
FLAG: 0xL4ugh{N07_JU$T_NUM63R5}* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| 25 |
| Weirdoooo_ ✔️_|_ Steganography _| 25 |
| Uraa |_ Steganography _| 50 |
| Zar |_ Steganography _| 50 |
| Colorful |_ Steganography _| 100 |
| Deep | Forensics | 200 |
| PVE | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Weee let’s jump into the 3rd challenge my friend “URAA”
Description: I love Urahara. he keeps hiding the secrets.We got a “ZIP” File containing a “JPG” image
 so let’s try our tools
so let’s try our tools
Strings - binwalk - exiftool - etcbut nothing is useful so if we notice in the description it said hiding the secrets. so let’s try to brute-force the image I’m lucky I know tools like “stegseek” so let’s try and see our luck :”D
stegseek image.jpg wordlistI’ll use my favorite wordlist “ rockyou.txt “
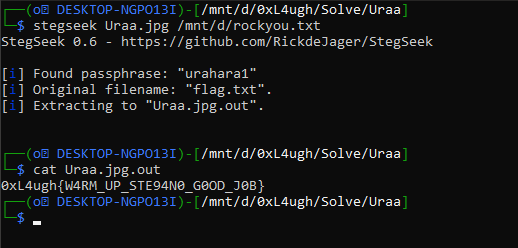 BRUH ?? that was easy lol.
BRUH ?? that was easy lol.
FLAG: 0xL4ugh{W4RM_UP_STE94N0_G0OD_J0B}* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| 25 |
| Weirdoooo_ ✔️_|_ Steganography _| 25 |
| Uraa_ ✔️_|_ Steganography _| 50 |
| Zar |_ Steganography _| 50 |
| Colorful |_ Steganography _| 100 |
| Deep | Forensics | 200 |
| PVE | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now we are moving to the 4th challenge “Zar” let’s see what we get
Description: Fast as zaraki boi. try to find him.We got a “ZIP” File containing a “JPG” image
 so let’s try our tools
so let’s try our tools
binwalk - exiftool - stegseek etcthis time stegseek is not working so it’s somewhere else. hmmm what about strings ???
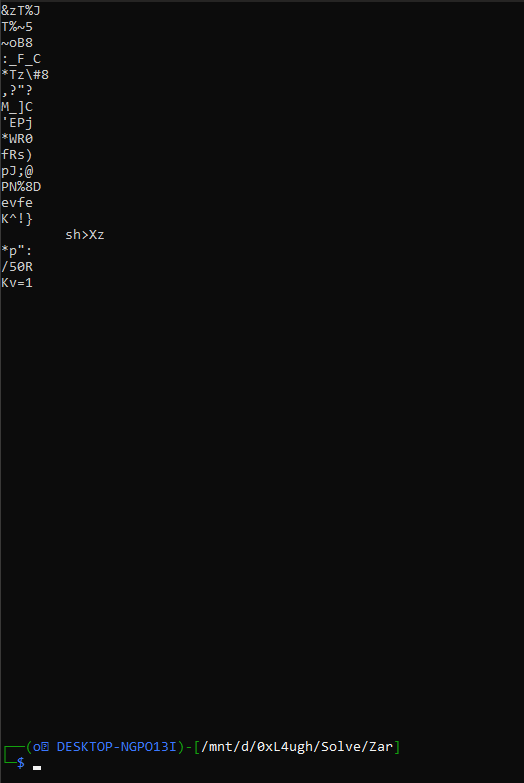 in the description said to try to find him maybe he meant that spaces? so let’s check the hex editor or “xxd”
in the description said to try to find him maybe he meant that spaces? so let’s check the hex editor or “xxd”
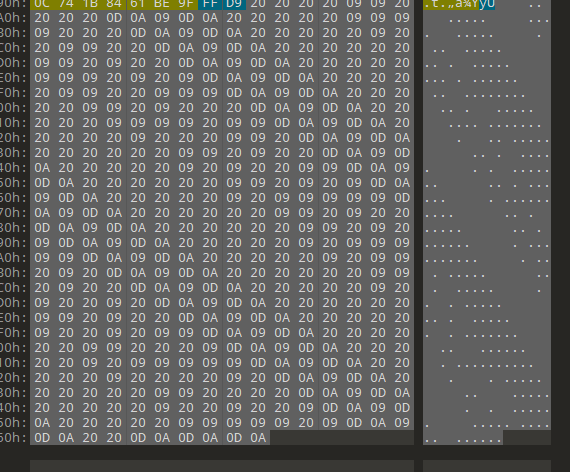 Okay now, this is interesting. but what is this? maybe morse? but no it’s not so let’s google if we can encode it into spaces and dots.
Okay now, this is interesting. but what is this? maybe morse? but no it’s not so let’s google if we can encode it into spaces and dots.
 AAA. and I found something called “WHITESPACES LANGUAGE” so Let’s try it.
AAA. and I found something called “WHITESPACES LANGUAGE” so Let’s try it.
 and yup we got the flag :””DDDD
and yup we got the flag :””DDDD
website: https://www.dcode.fr/whitespace-language
FLAG: 0xL4ugh{F4S5_45_Z4R4K1_B0I}* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| 25 |
| Weirdoooo_ ✔️_|_ Steganography _| 25 |
| Uraa_ ✔️_|_ Steganography _| 50 |
| Zar_ ✔️_|_ Steganography _| 50 |
| Colorful |_ Steganography _| 100 |
| Deep | Forensics | 200 |
| PVE | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now we are moving to the 5th challenge “Colorful” let’s see what we get
Description: This is really colorful but what does that mean ?
Flag Format: 0xL4ugh{word1_word2}We got a “ZIP” File containing a “PNG” image
 that’s a lot of colors Mr.xElessaway
that’s a lot of colors Mr.xElessaway
 but I’ll do my super ultra genius way to solve this challenge
but I’ll do my super ultra genius way to solve this challenge
 no no, I meant to put the whole image in google image but nothing useful so I’ll ask google directly.
no no, I meant to put the whole image in google image but nothing useful so I’ll ask google directly.
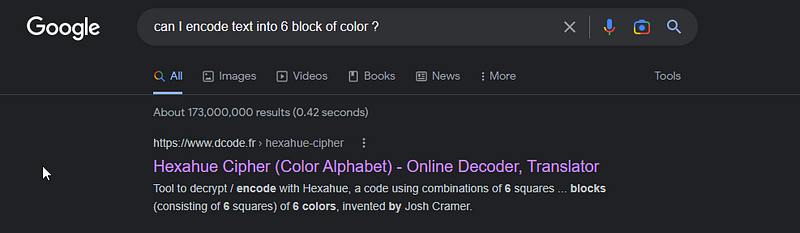 lol first search I’ll open it and see what it contains
lol first search I’ll open it and see what it contains
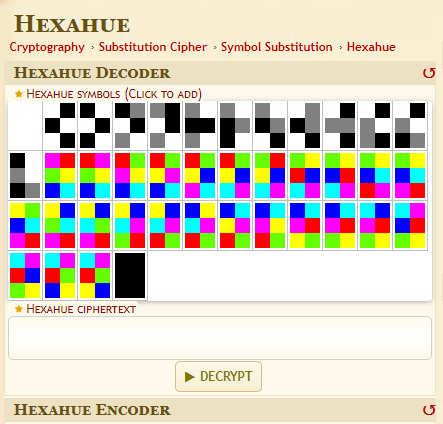 well well well we reach our way to the solution. so the flag is
well well well we reach our way to the solution. so the flag is
FLAG: 0xL4ugh{TH1S_15_H3X4HU3_C0D3}* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| 25 |
| Weirdoooo_ ✔️_|_ Steganography _| 25 |
| Uraa_ ✔️_|_ Steganography _| 50 |
| Zar_ ✔️_|_ Steganography _| 50 |
| Colorful_ ✔️_|_ Steganography _| 100 |
| Deep | Forensics | 200 |
| PVE | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now Steganography is over. let’s move to the Forensics boiz and start with “DEEP”.
Description: One of the companies called you to investigate a suspicious
computer system. You need to use your skills to find out what
happened.they tried to get you a part of the partition so can
you find out the secret behind that attack?in this challenge seems we got a part of the C drive partition.
 So we need to think first about what we should look for maybe a registry? but we are looking in the registry I can’t go random and check there. so what about checking the event viewer if anything is executed?
time to google where are the windows event located.
and after some googling
So we need to think first about what we should look for maybe a registry? but we are looking in the registry I can’t go random and check there. so what about checking the event viewer if anything is executed?
time to google where are the windows event located.
and after some googling
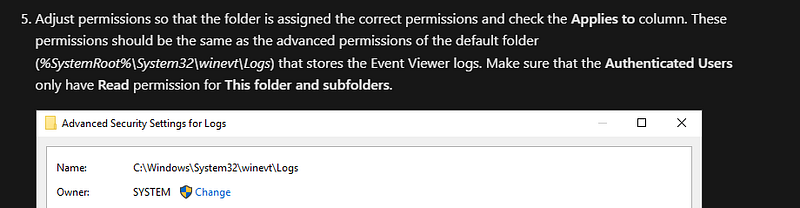 I found out that it saved into
I found out that it saved into
%SystemRoot%\\System32\\winevt\\Logsso let’s visit this directory and see if something interested
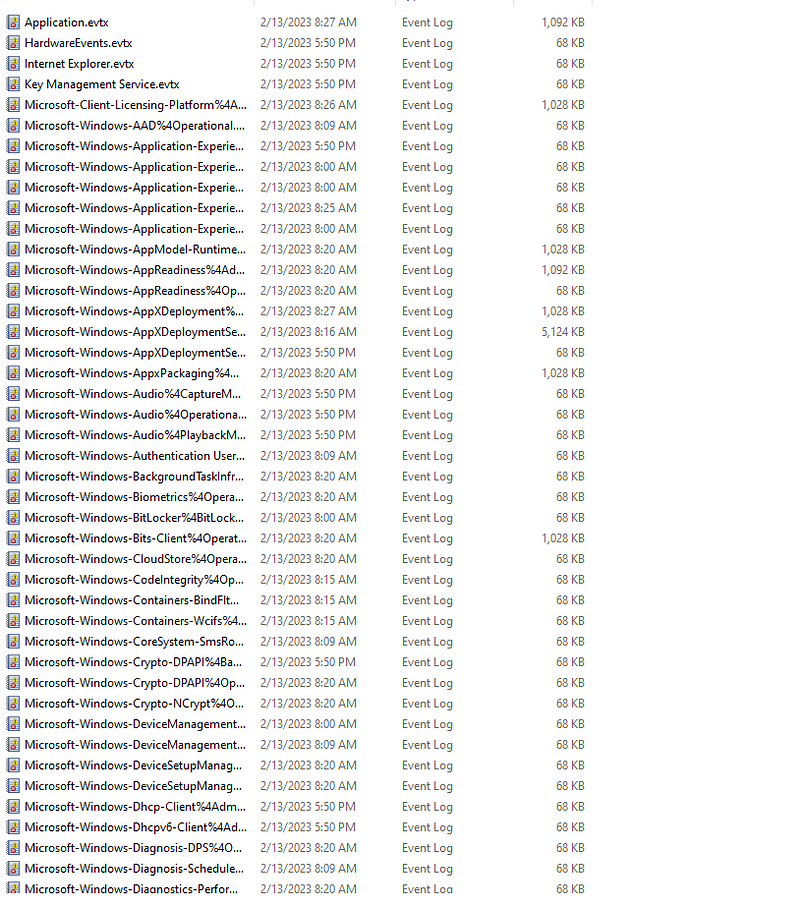 cool, we found all the event viewers. but BRUH that’s a lot of files xD
cool, we found all the event viewers. but BRUH that’s a lot of files xD
 so let’s put it on the right side so we can back later cause this is scary and I don’t want to feel bad I can solve it. so let’s think about what the attacker might use. Hmm maybe Powershell? but how?
so let’s put it on the right side so we can back later cause this is scary and I don’t want to feel bad I can solve it. so let’s think about what the attacker might use. Hmm maybe Powershell? but how?
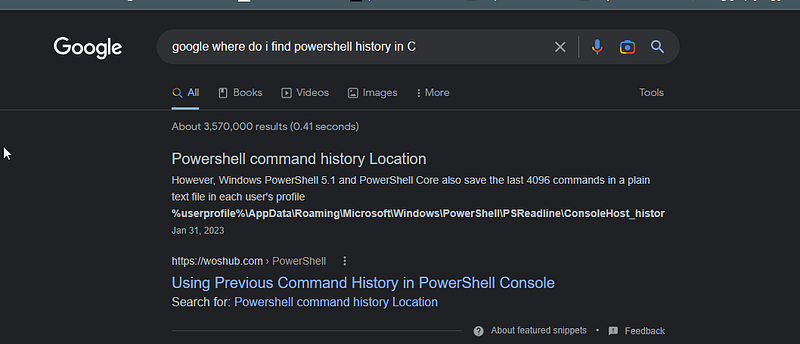 cool another piece of evidence we can check now.
cool another piece of evidence we can check now.
%userprofile%\\AppData\\Roaming\\Microsoft\\Windows\\PowerShell\\PSReadline\\ConsoleHost_history.txtlet’s go and check.
 cool. we find the history of the PowerShell so let’s check what it contain.
cool. we find the history of the PowerShell so let’s check what it contain.
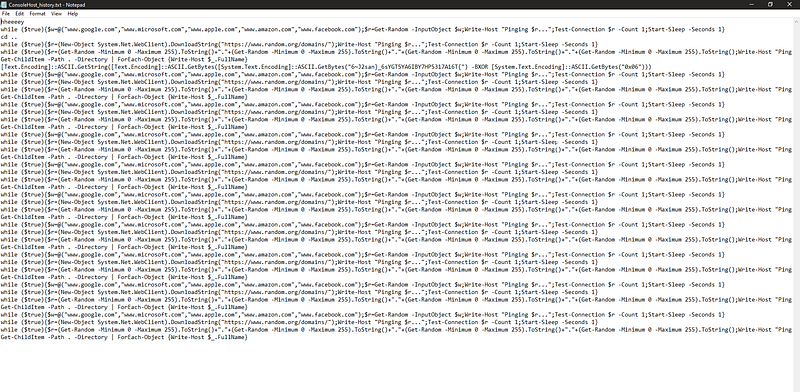 starts with heeey so I guess we are on the right path. and I noticed something hidden
starts with heeey so I guess we are on the right path. and I noticed something hidden
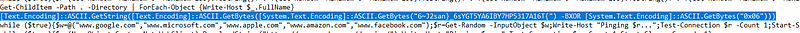 a simple xor operator with a string so let’s try to reverse the string.
a simple xor operator with a string so let’s try to reverse the string.
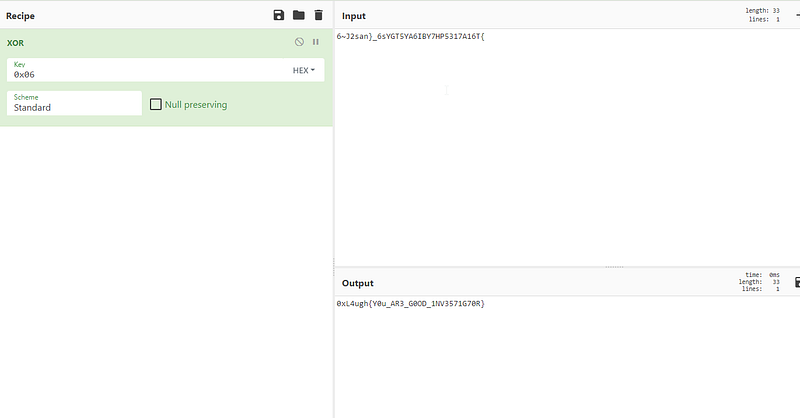 weee, now we got the flag
weee, now we got the flag
FLAG: 0xL4ugh{Y0u_AR3_G0OD_1NV3571G70R}* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| Medium |
| Weirdoooo_ ✔️_|_ Steganography _| Medium |
| Uraa_ ✔️_|_ Steganography _| Easy |
| Zar_ ✔️_|_ Steganography _| Easy |
| Colorful_ ✔️_|_ Steganography _| Medium |
| Deep_ ✔️_| Forensics | Medium |
| PVE | Forensics | Hard |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now we are moving to the 2nd challenge “PVE” let’s see what we get
Description: An attacker attacked our server. we got a dump so can you
investigate it for us?in this challenge, we got a “VMEM” file so we need to use volatility to go through this challenge
 first, we need to know what is the profile of the image for the Q1
so let’s run image info on it
first, we need to know what is the profile of the image for the Q1
so let’s run image info on it
python2 vol.py -f PVE.vmem imageinfo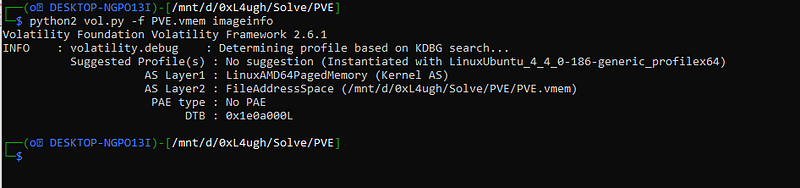 after a long time you will notice that no profile suggestion
after a long time you will notice that no profile suggestion
note: you won’t see this part (“Instantiated with LinuxUbuntu_4_4_0–186-generic_profilex64”) because I already got the profile.
so first let’s think how can we get the operating system or kernel version hmmm let’s do “grep” with “strings”
strings PVE.vmem | grep -i "Linux version"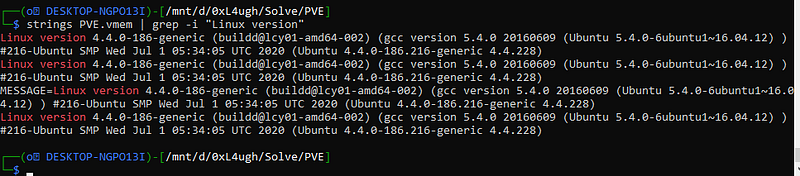 as we all can see we got the first Question “PVE 1”
as we all can see we got the first Question “PVE 1”
Q1: What is the operating system and kernal version of the dump
Flag format: 0xL4ugh{OsName_theFullKernalVersion}so the first flag would be
Q1 Flag: 0xL4ugh{Ubuntu_4.4.0-186-generic}now we need to get the profile of this memory so after I googled I found this useful article that helped me so much to build a profile to volatility. article: https://www.synacktiv.com/en/publications/sharkyctf-ezdump-writeups-linux-forensics-introduction.html so after following it I got the profile and installed it in
volatility\\plugins\\overlays\\linux so now let’s check if it works for us or not by running info
so now let’s check if it works for us or not by running info
python2 vol.py --info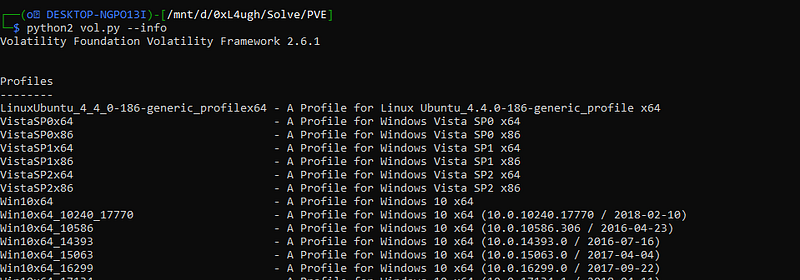 well as you can see the profile works now so let’s use it and check for the next questions.
well as you can see the profile works now so let’s use it and check for the next questions.
python2 vol.py -f PVE.vmem \--profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_psscan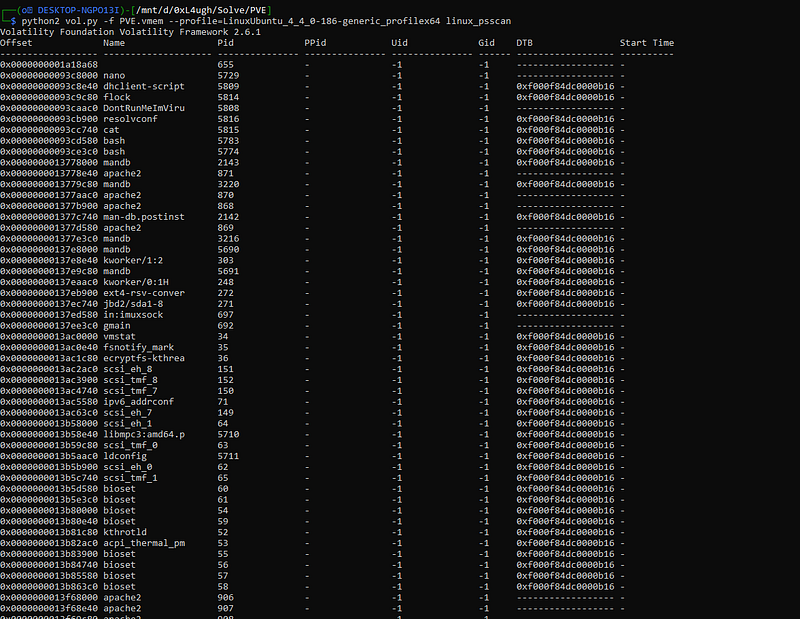 yup, it works. so the 2nd question “PVE 2” says
yup, it works. so the 2nd question “PVE 2” says
Q2: What is the version of the apache server?so let’s see the history if he installed it or something
python2 vol.py -f PVE.vmem \--profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_bash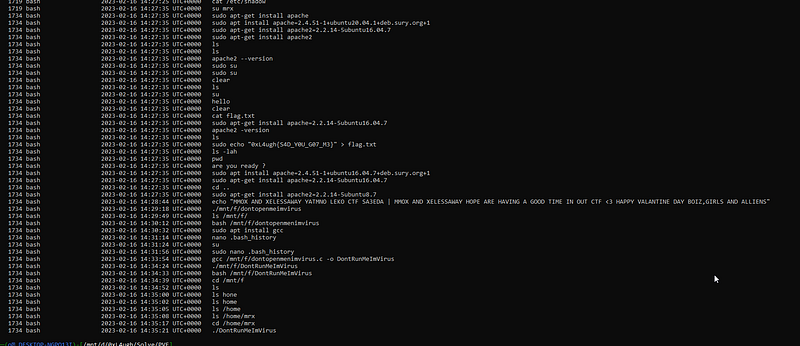 well well well seems interesting for us there is a flag here 2. seems we hit 2 birds with one rock :”
well well well seems interesting for us there is a flag here 2. seems we hit 2 birds with one rock :”
so Q2 answer is
Q2 Flag: 0xL4ugh{2.2.14}let’s move to Question 3 which is “PVE 3”
Q3: We think that there was a suspicious process can you look what is it and reterive the flag ?so we need to go back and check the process if there is any thing suspicious.
python2 vol.py -f PVE.vmem \--profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_psscan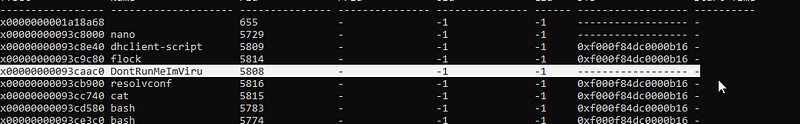
This is a suspicious process we are lucky the hacker is stupid he didn’t hide it. so let’s dump this process and retrieve the flag.
python2 vol.py -f PVE.vmem \--profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_procdump -p 5808 -D output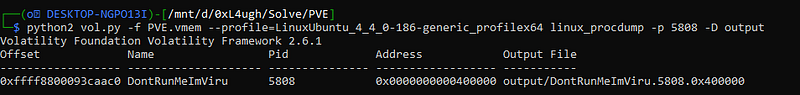 now we got the dumped process we can just string it and see what we get.
now we got the dumped process we can just string it and see what we get.
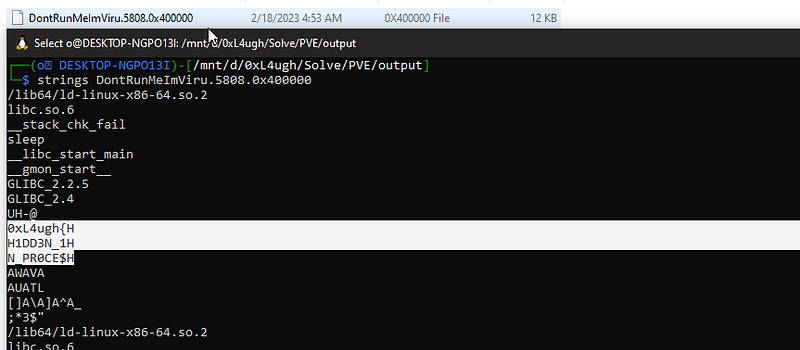 well its almost clear to us so the answer is
well its almost clear to us so the answer is
Q3 Flag: 0xL4ugh{H1DD3N_1N_PR0CE$$}let’s move to the 4th question “PVE 4” Q4: There is something hidden in somewhere but can you find where ? I guess we already got that flag from the bash so let’s try it and yup it will work
Q4 Flag: 0xL4ugh{S4D_Y0U_G07_M3}now let’s move into the 5th question “PVE 5”
Q5: The attack got the password of the user but can you?hmmmmm let’s ask google
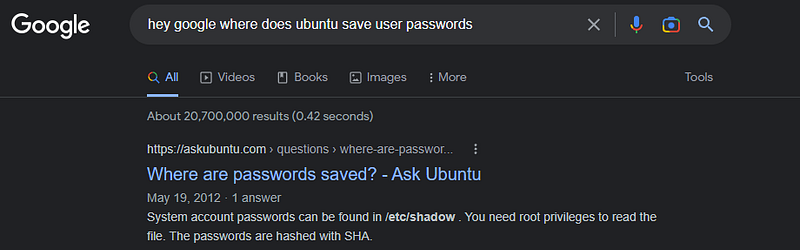 well its “etc/shadow”
so let’s dump both shadow and passwd.
well its “etc/shadow”
so let’s dump both shadow and passwd.
python2 vol.py -f PVE.vmem --profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_find_file -F /etc/shadow
python2 vol.py -f PVE.vmem --profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_find_file -F /etc/passwd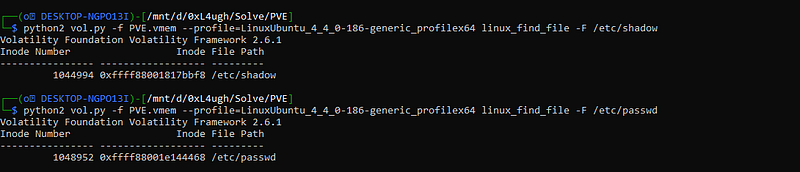 good, we find them and now we have the offsets “0xffff88001817bbf8” and “0xffff88001e144468”. so let’s dump now
NOTE: you need to create an empty file with the same name first
good, we find them and now we have the offsets “0xffff88001817bbf8” and “0xffff88001e144468”. so let’s dump now
NOTE: you need to create an empty file with the same name first
 Now let’s continue dumping the files
Now let’s continue dumping the files
python2 vol.py -f PVE.vmem --profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_find_file -i 0xffff88001817bbf8 -O output/shadow
python2 vol.py -f PVE.vmem --profile=LinuxUbuntu_4_4_0-186-generic_profilex64 linux_find_file -i 0xffff88001e144468 -O output/passwd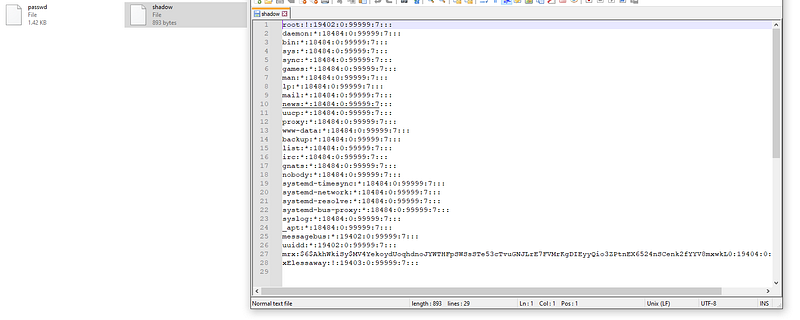 cool works for now so let’s unshadow the files
cool works for now so let’s unshadow the files
unshadow passwd shadow > hashafter getting the unshadow file let’s run john the ripper to crack the password.
john --wordlist='/mnt/d/rockyou.txt' hashafter a long long long long long long time

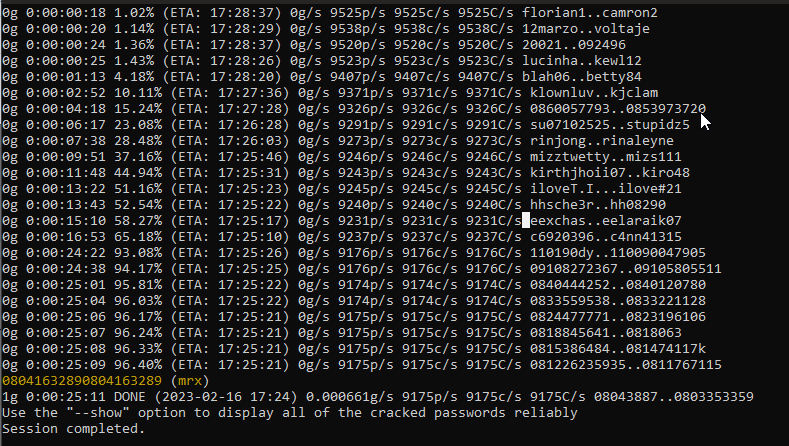 oh finally we got the password now the flag is
oh finally we got the password now the flag is
Q5 Flag: 0xL4ugh{08041632890804163289}* + — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Bloody_ ✔️_|_ Steganography _| Medium |
| Weirdoooo_ ✔️_|_ Steganography _| Medium |
| Uraa_ ✔️_|_ Steganography _| Easy |
| Zar_ ✔️_|_ Steganography _| Easy |
| Colorful_ ✔️_|_ Steganography _| Medium |
| Deep_ ✔️_| Forensics | Medium |
| PVE_ ✔️ _| Forensics | Hard |
+ — — — — — — — — + — — — — — — — -+ — — — — +_For now, we are done and I hope you really enjoyed my challenges guys and hope to see you soon in other writeups ^_^ ❤. good luck.
By Ahmed Elessaway on February 18, 2023.