Published
- 11 min read
AUC- Hotaru Games Writeups

AUC- Hotaru Games Writeups
Hello, It’s xElessaway, first it was my pleasure to create the steganography challenges in this ctf. The second Challenge was easy for some players in ctf but my first aim was for the players who want to start playing CTFs so I thought these challenges would be great for their start. so enough talks and here is the write-up for my challenges. I hope you enjoy it.
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas |_ Steganography _| 25 |
| Witch |_ Steganography _| 25 |
| Chamber |_ Steganography _| 50 |
| MorsE |_ Steganography _| 50 |
| Viktor |_ Steganography _| 100 |
| Artist | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +Okay, Let’s start with Sylas and see how we will go through it.
Description: I have been in the prison for long long long time.in the challenge, we got a “jpg” file. so it’s one image hmmm let’s try some tools on it like
Strings - exiftool - steghide - etc but don’t forget we can’t use “zsteg” here why? Because when you use any tool u need to read the documentation. so zsteg is made only for (PNG, BMP)
but don’t forget we can’t use “zsteg” here why? Because when you use any tool u need to read the documentation. so zsteg is made only for (PNG, BMP)
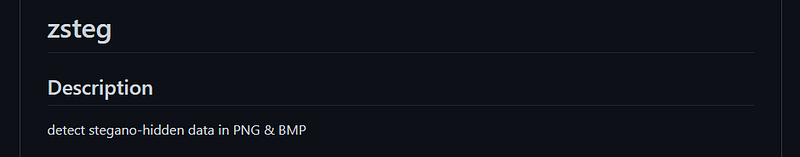 so let’s try to see if there are any hidden data in it using “binwalk”.
so let’s try to see if there are any hidden data in it using “binwalk”.
binwalk filename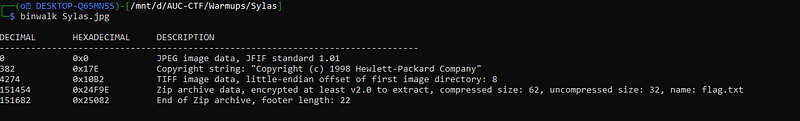 ohohoh something interesting is hidden :D. let’s extract it.
ohohoh something interesting is hidden :D. let’s extract it.
binwalk -e Sylas.jpgwell gg, I got the flag. but !!
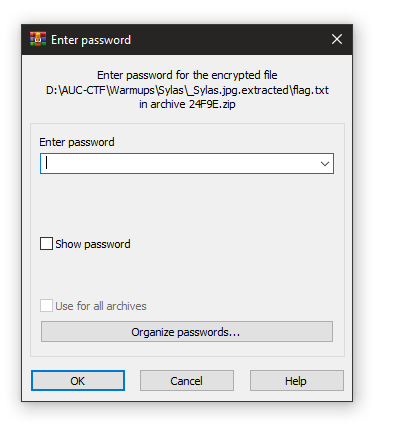 Need password T-T. So let’s google how to crack a zip password using Linux and see what we got.
Need password T-T. So let’s google how to crack a zip password using Linux and see what we got.
 Watitng while finisng my googling
After some googling I found out that I can crack zip password using wordlist “rockyou” with tool called “JohnTheRipper” of course there are other tools like “hashcat” — “fcrackzip” but I prefer John.
so after seeing tutorial about how can I use it. here is the steps.
1st step you need to get the password hash using “zip2john”
Watitng while finisng my googling
After some googling I found out that I can crack zip password using wordlist “rockyou” with tool called “JohnTheRipper” of course there are other tools like “hashcat” — “fcrackzip” but I prefer John.
so after seeing tutorial about how can I use it. here is the steps.
1st step you need to get the password hash using “zip2john”
zip2john 24F9E.zip > hash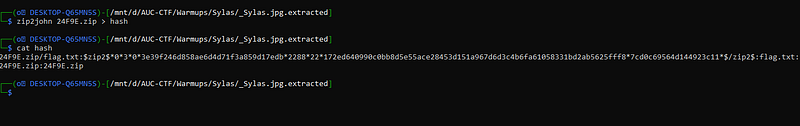 yup we got it. now let’s crack the password using “rockyou”.
yup we got it. now let’s crack the password using “rockyou”.
john --wordlist="/path_to_wordlist/../rockyou.txt" hashwait for sometime and yup you got the password which is “!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!”. sorry for making it at 98.9% in wordlist :D.
yup here is the flag.
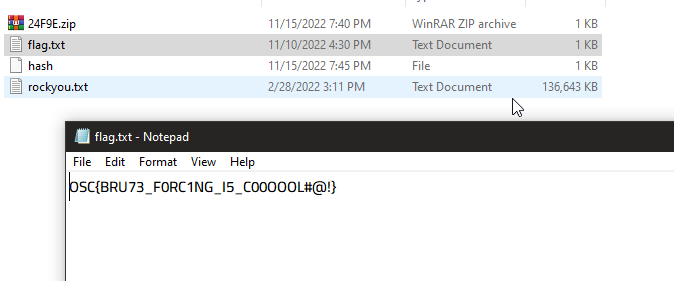
OSC{BRU73_F0RC1NG_I5_C00OOOL#@!}* _— — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas_✔️ _|_ Steganography _| 25 |
| Witch |_ Steganography _| 25 |
| Chamber |_ Steganography _| 50 |
| MorsE |_ Steganography _| 50 |
| Viktor |_ Steganography _| 100 |
| Artist | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Weee now we move to second challenge which is “Witch”
Description: Our Witch used to protect her crystal.can u find where she
keep it?Oh another “jpg” image let’s try our tools again.
String - steghide - exiftool - etcyou will notice that “binwalk” contain a “PNG” ohohoh let’s extract it.
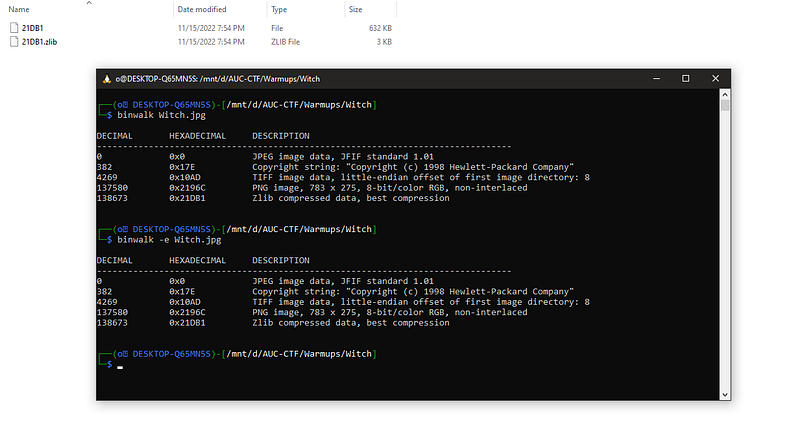
binwalk -e Witch.jpg where is the png ???? lol why binwalk is not working with me.
so I’ll start check this issue on google why binwalk didn’t extract the file.
where is the png ???? lol why binwalk is not working with me.
so I’ll start check this issue on google why binwalk didn’t extract the file.
 Watitng while finisng my googling
I found that I can use it in another way. using (- - dd=”.*”) instead of “-e”. to force binwalk to extract them. we use “.*” because “*” Star means select all in linux.
Watitng while finisng my googling
I found that I can use it in another way. using (- - dd=”.*”) instead of “-e”. to force binwalk to extract them. we use “.*” because “*” Star means select all in linux.
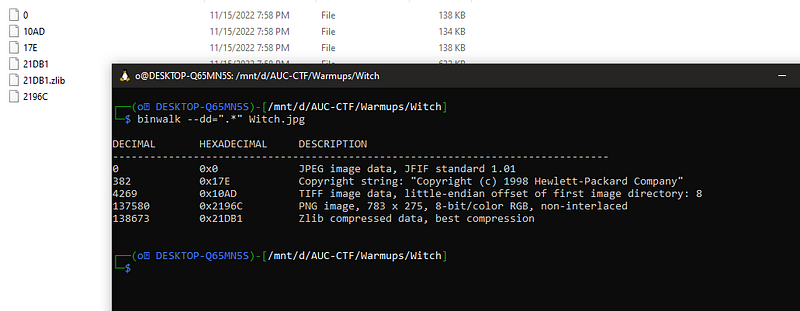 wee we got the file but extension-less. so all I need to put the extension back.
wee we got the file but extension-less. so all I need to put the extension back.
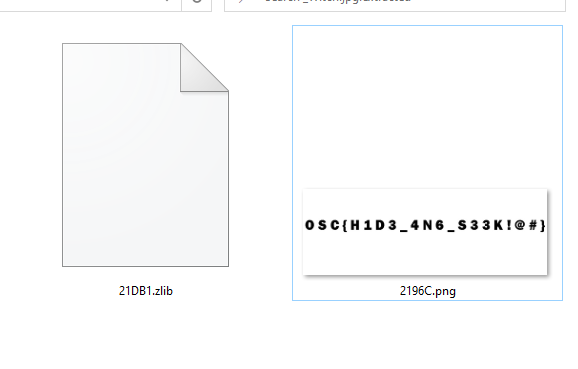 and yup here is the flag :DD.
and yup here is the flag :DD.
OSC{H1D3_4N6_S33K!@#}* _— — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas_✔️ _|_ Steganography _| 25 |
| Witch_✔️ _|_ Steganography _| 25 |
| Chamber |_ Steganography _| 50 |
| MorsE |_ Steganography _| 50 |
| Viktor |_ Steganography _| 100 |
| Artist | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Let’s move to the french guy “Chamber”.
Description: Go for it my friend.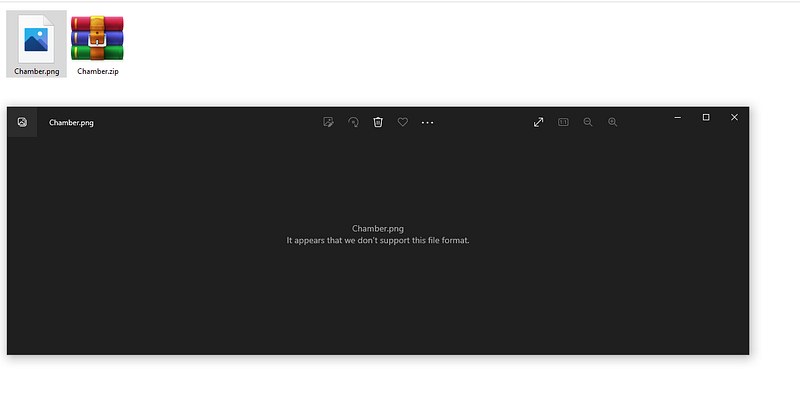 Okay in this challenge I got a “PNG” but it’s not working!!!. first I thought the challenge was broken. but I knew that it’s broken image and we need to fix it. so Let’s google about “ how to fix corrupted png “. so I found that every file has its own magic bytes so I found a great wikipedia page for this one
List of file signatures - Wikipedia
Okay in this challenge I got a “PNG” but it’s not working!!!. first I thought the challenge was broken. but I knew that it’s broken image and we need to fix it. so Let’s google about “ how to fix corrupted png “. so I found that every file has its own magic bytes so I found a great wikipedia page for this one
List of file signatures - Wikipedia
needs additional citations for verification .improve this article by (Learn how and when to remove this template…_en.wikipedia.org
that really helped me to understand more about files structure. so let’s see the png magic bytes and compare to mine using any hex editor.
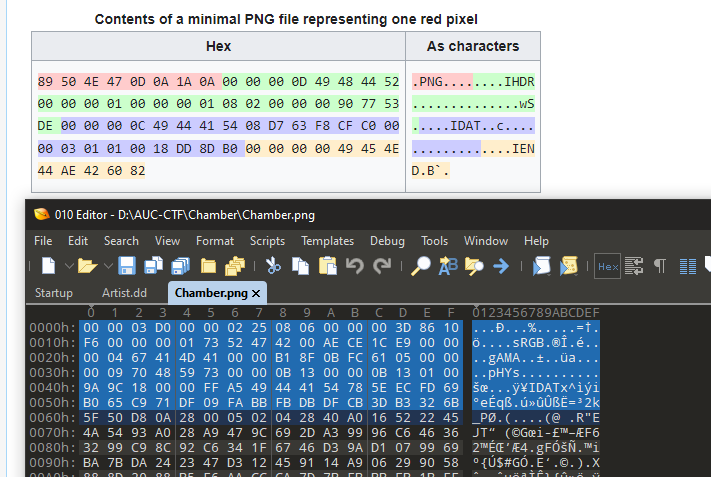 hmmm. yup it’s the same but the first 16 bytes are missing !! so I’ll try to add them.
hmmm. yup it’s the same but the first 16 bytes are missing !! so I’ll try to add them.
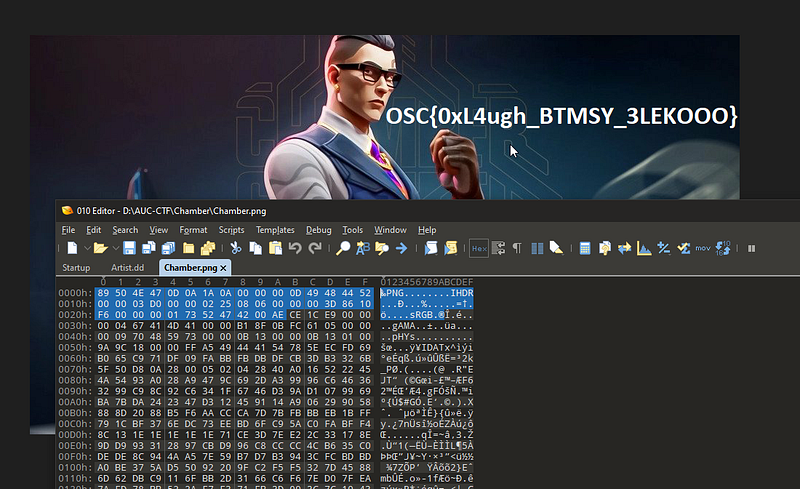 Weeee I fixed it and we got the flag now :D
Weeee I fixed it and we got the flag now :D
OSC{0xL4ugh_BTMSY_3LEKOOO}* _— — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas_✔️ _|_ Steganography _| 25 |
| Witch_✔️ _|_ Steganography _| 25 |
| Chamber_✔️ _|_ Steganography _| 50 |
| MorsE |_ Steganography _| 50 |
| Viktor |_ Steganography _| 100 |
| Artist | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now let’s move to “MorsE”
Description: Hello Solider, we have sent a message to the base but seems
the road is full of traps, so we need to go back from that roadin this challenge we got a “MP3” audio file so let’s try to listen to it and see what we get.
 well I didn’t undersand any single letter :’) so I was like baby yoda below :). so you know what should I do ? yes it’s googling time about beeb beeb encoding methods.
well I didn’t undersand any single letter :’) so I was like baby yoda below :). so you know what should I do ? yes it’s googling time about beeb beeb encoding methods.
 Watitng while finisng my googling
Watitng while finisng my googling
 wee google told me it might be “Morse” but lol it’s the same of the challenge name !. okay let’s find a decoder online.
wee google told me it might be “Morse” but lol it’s the same of the challenge name !. okay let’s find a decoder online.
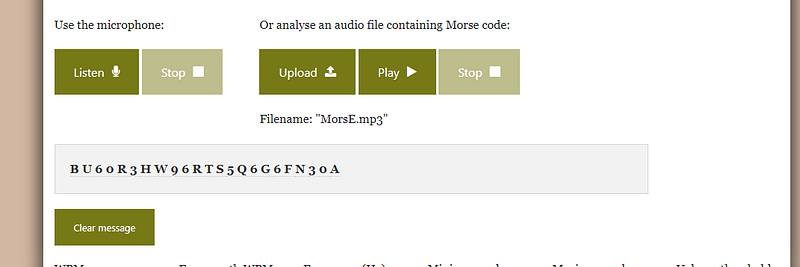 lol it’s not the correct flag!! cause flag is readable. so let me thing again hmmm. but I noticed in description “we need to go back from that road”
and “ E “ in challenge name is capital hmm so maybe we need to go backward let’s try it using audio reverse online
lol it’s not the correct flag!! cause flag is readable. so let me thing again hmmm. but I noticed in description “we need to go back from that road”
and “ E “ in challenge name is capital hmm so maybe we need to go backward let’s try it using audio reverse online
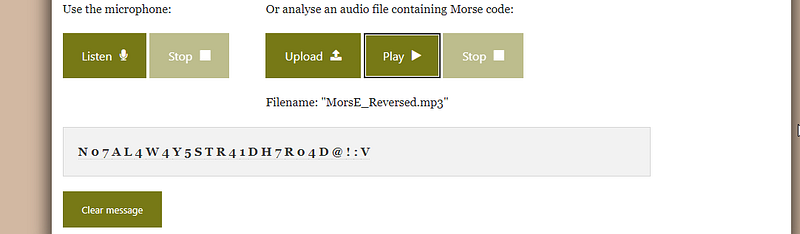 okay I can understand some of it but we need to split words Like this
okay I can understand some of it but we need to split words Like this
NO7_AL4W4Y5_STR41DGH7_ROAD@!:Vyup it’s clear now so this the flag :D
OSC{N07_AL4W4Y5_STR41GH7_R04D@!:V}* _— — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas_✔️ _|_ Steganography _| 25 |
| Witch_✔️ _|_ Steganography _| 25 |
| Chamber_✔️ _|_ Steganography _| 50 |
| MorsE_✔️ _|_ Steganography _| 50 |
| Viktor |_ Steganography _| 100 |
| Artist | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_Now its time for the crazy scientist “ Viktor “. let’s see what we got in this challenge.
Description: Oh Hello Mate. My Friend jayce wanted to send me a secret file
that contain the secerct material of our great Hextech S. but sadly he did
something wrong this time so can u help me to find the secrect material.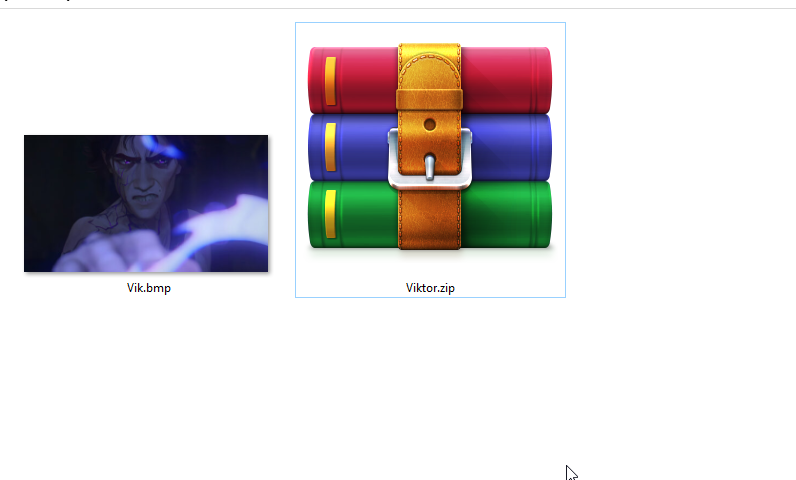 We got a “ bmp “ file in this challenge. so let’s try the basic tools.
We got a “ bmp “ file in this challenge. so let’s try the basic tools.
exiftool - zsteg ( it's bmp ) - stegsolverbut this time strings gave us some useful info.
strings Vik.bmp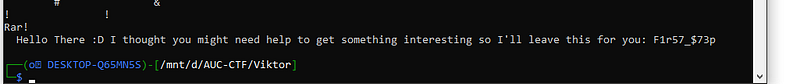 you will notice binwalk too gave us a rar file but it has a password.
you will notice binwalk too gave us a rar file but it has a password.
binwalk -e Vik.bmp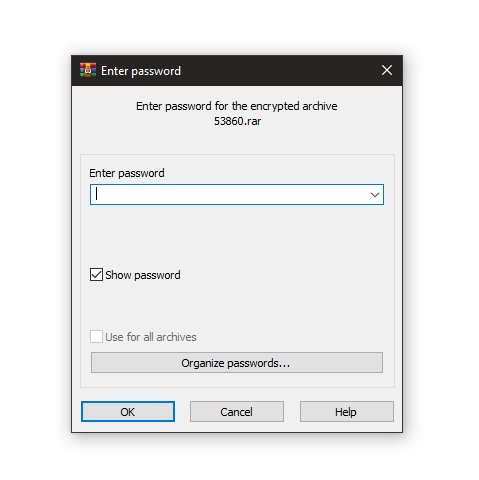 so I tried “ F1r57_$73p “ as a password, but it didn’t work so I tried to use john with rockyou to brute-force the password but it’s not working. so it’s time to! yes google xD
so I tried “ F1r57_$73p “ as a password, but it didn’t work so I tried to use john with rockyou to brute-force the password but it’s not working. so it’s time to! yes google xD
 Watitng while finisng my googling
and I found a medium article on bmp files to hide data.
Steganography technique with S-Tools
Watitng while finisng my googling
and I found a medium article on bmp files to hide data.
Steganography technique with S-Tools
_S-Tools is a program composed by Andy Brown. It is maybe the most broadly perceived steganography instrument accessible…_medium.com
and I found S-Tools so I downloaded it and opened it.
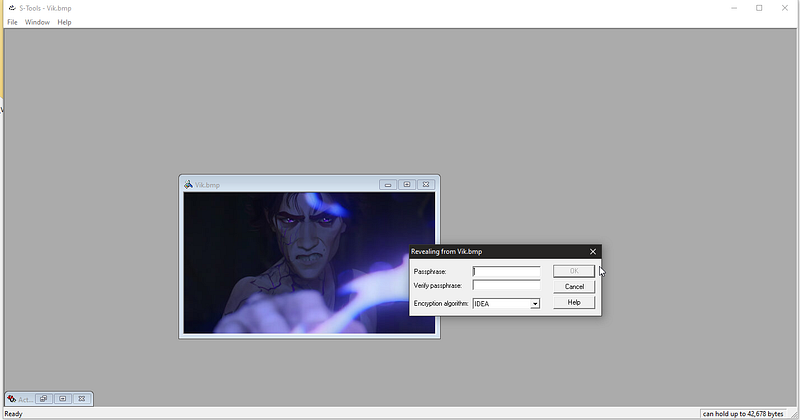 woah it needs a passphrase so let’s try “ F1r57_$73p “ as password.
woah it needs a passphrase so let’s try “ F1r57_$73p “ as password.
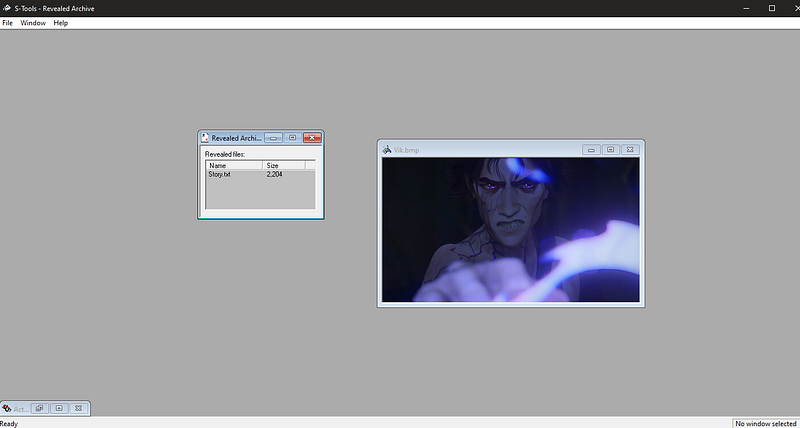 Yup it works. we got Story.txt let’s extract it and see what is this.
Yup it works. we got Story.txt let’s extract it and see what is this.
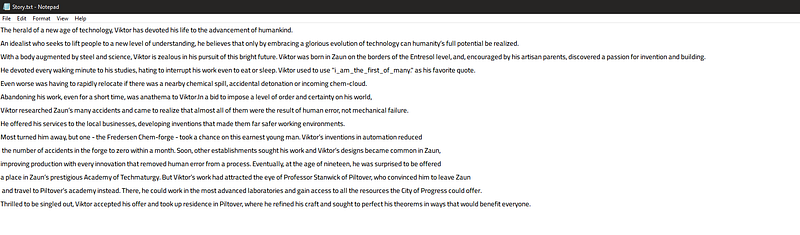 a long long story but I noticed that there is a sentence between double quotes “ I_am_the_first_of_many. ” so maybe it’s the password of the rar file ! let’s try it.
a long long story but I noticed that there is a sentence between double quotes “ I_am_the_first_of_many. ” so maybe it’s the password of the rar file ! let’s try it.
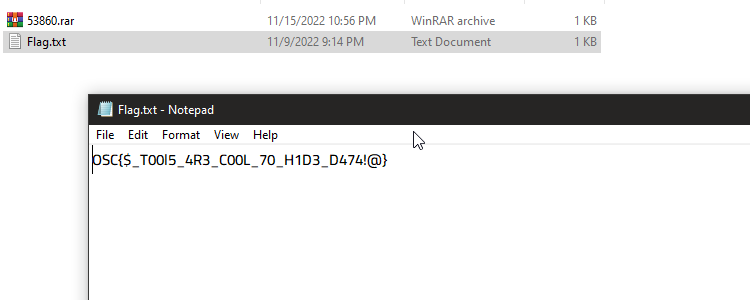 weee got the flag :D
weee got the flag :D
OSC{$_T00l5_4R3_C00L_70_H1D3_D474!@}* _— — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas_✔️ _|_ Steganography _| 25 |
| Witch_✔️ _|_ Steganography _| 25 |
| Chamber_✔️ _|_ Steganography _| 50 |
| MorsE_✔️ _|_ Steganography _| 50 |
| Viktor_✔️ _|_ Steganography _| 100 |
| Artist | Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_head to the hard one forensics :3.
Describtion: Hello Mr.X we really need your help we visited our friend today
but there is no one in house and didn't left any messages but we think he
got kidnapped so we got a some of his files. can you go deep into it and
help us to know where is he ???so first of all we got a zip file, let’s extract the content.
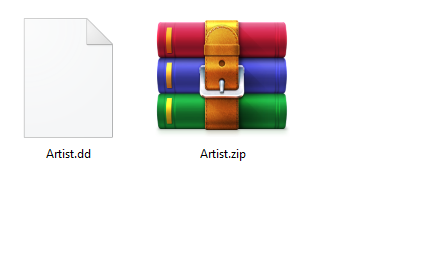 Okay seems interesting this time we got a file in “.dd” extenstion so let’s check what type of files is that.
Okay seems interesting this time we got a file in “.dd” extenstion so let’s check what type of files is that.
file "filename"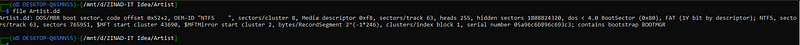 well well well, seems it’s a part of disk. so let’s start analysis it using our favorite tool “FTK Imger”.
well well well, seems it’s a part of disk. so let’s start analysis it using our favorite tool “FTK Imger”.
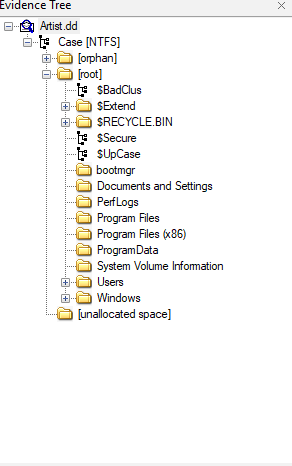 I noticed that there is “Program Files” and “Windows”. so it’s a System parition (“C:/”).
I noticed that there is “Program Files” and “Windows”. so it’s a System parition (“C:/”).
so let’s visit the Users and see if something interesting in it.
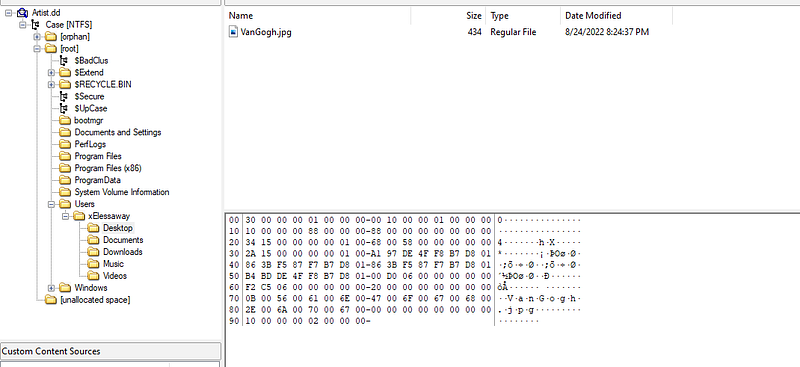 okay after checking Users. we got a “jpg” at Desktop in “xElessaway” User.
okay after checking Users. we got a “jpg” at Desktop in “xElessaway” User.
so Let’s extract it and check what does it contain.
 seems a normal art. so let’s check it using our tools
seems a normal art. so let’s check it using our tools
Exiftool, steghide, binwalk, etcafter using them. I noticed that there is a string at the end of the file
strings "filename"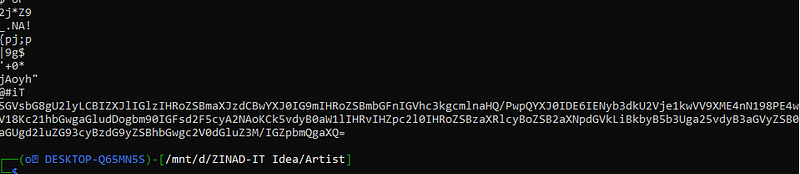 oh seems base64. so let’s decode it and see what it say.
oh seems base64. so let’s decode it and see what it say.
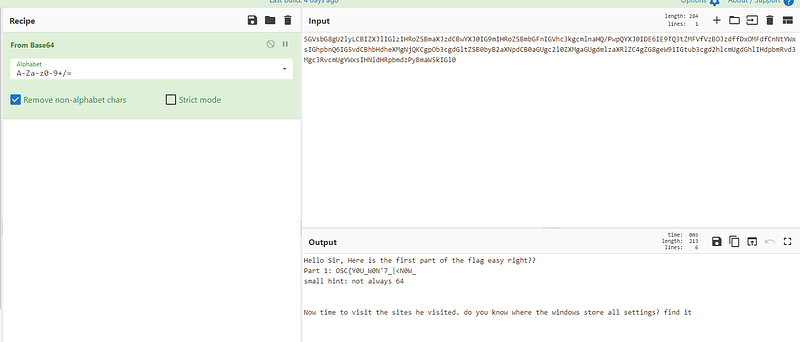 okayy. we got first part of the flag
okayy. we got first part of the flag
Part 1: OSC{Y0U_W0N’7_|<N0W_\`\`\`and said
Now time to visit the sites he visited. do you know where the windows store
all settings? find it
hmmmm I started to google about where does the windows store all settings. and Yes I got it now he was talking about “Registers”. so let’s google where do I find registers in the system directories. and found that the registers stored in “%SystemRoot%/System32/Config”.
So let’s visit that location in our “FTK imager” .
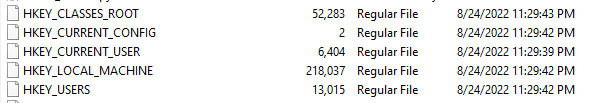 oh we got the registers now let’s start to find out what it need. I started to put the registers on “Registery Workshop”.
oh we got the registers now let’s start to find out what it need. I started to put the registers on “Registery Workshop”.
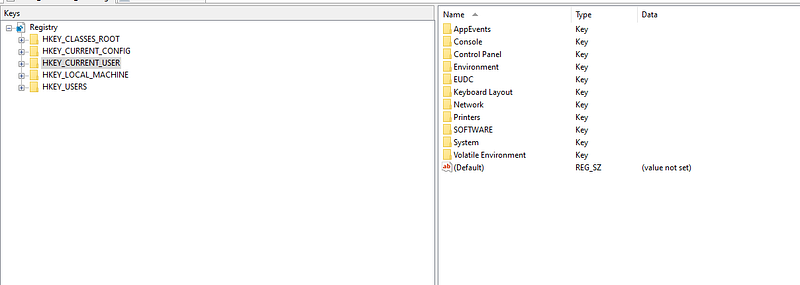 so what do u want now from registry ??. oh I forgot he said “Now time to visit the sites he visited”. I start googling about “where do I find the visited sites in registers”. and got this while googling.
so what do u want now from registry ??. oh I forgot he said “Now time to visit the sites he visited”. I start googling about “where do I find the visited sites in registers”. and got this while googling.
 so let’s see if “TypedURLs” key has anything for me :3.
so let’s see if “TypedURLs” key has anything for me :3.
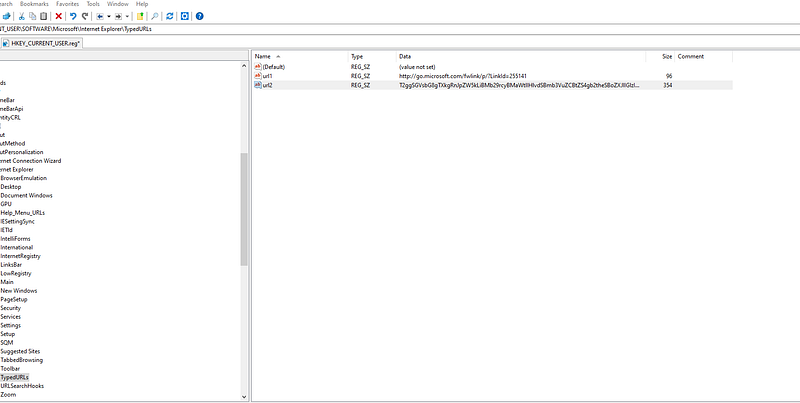 oh now seems we got something interesting now. looks like it’s base64 so let’s decode it.
oh now seems we got something interesting now. looks like it’s base64 so let’s decode it.
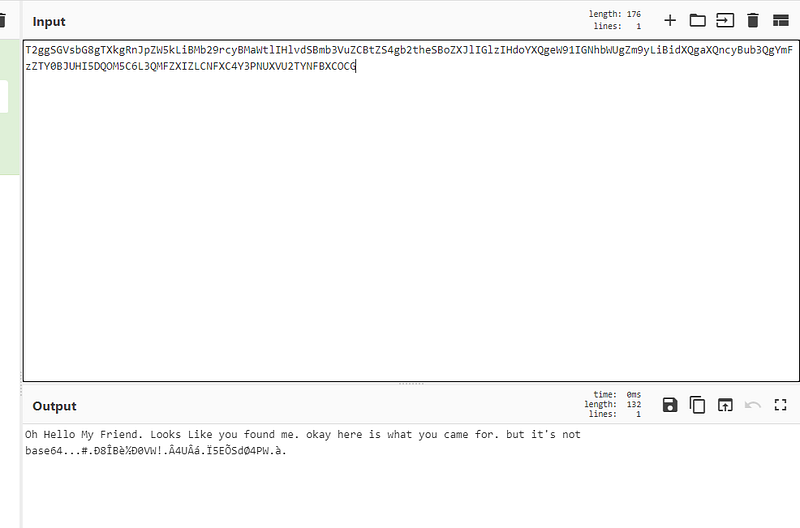 yes it’s base64 but last part of it seems corrupted or missed something. but I noticed “ it’s not base64 ”. so hmmm let’s try another base type. let’s try base32.
yes it’s base64 but last part of it seems corrupted or missed something. but I noticed “ it’s not base64 ”. so hmmm let’s try another base type. let’s try base32.
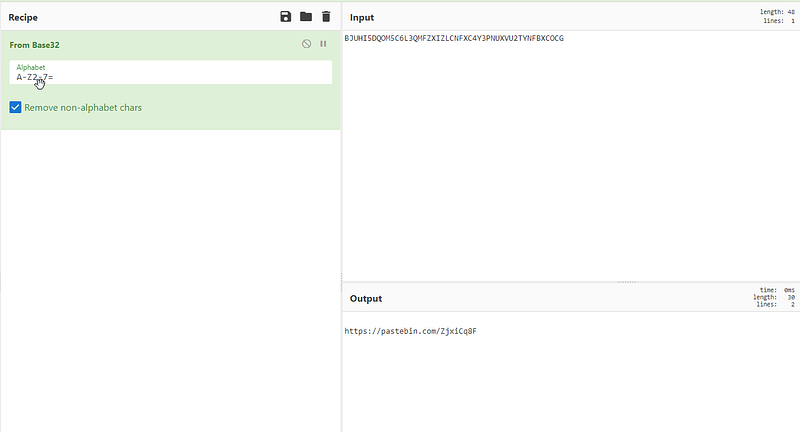 and yup we got the pastebin link nice.
and yup we got the pastebin link nice.
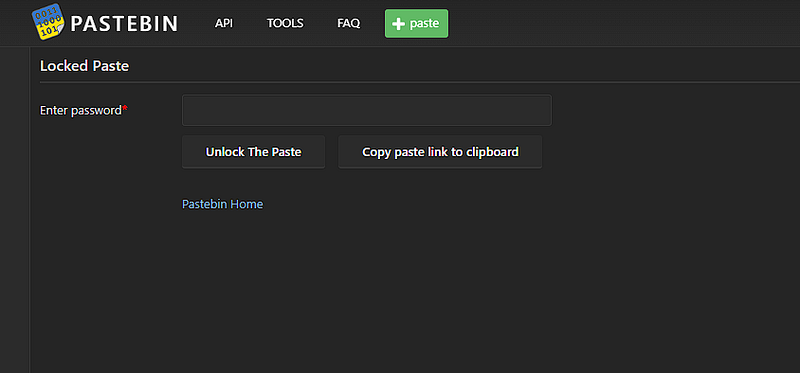 hmmm it has password. so how do I get the password ? I tried to google too much so I think about going in history using “WAYBACKMACHINE”. it’s important tool in OSINT challenges.
hmmm it has password. so how do I get the password ? I tried to google too much so I think about going in history using “WAYBACKMACHINE”. it’s important tool in OSINT challenges.
so let’s try the pastebin link on it. oh I found a snapshot so let’s open it!
 ohohoh now we got password now. let’s open the pastebin and see what he hide.
cool now we got part 2 of the flag
ohohoh now we got password now. let’s open the pastebin and see what he hide.
cool now we got part 2 of the flag
here is the part you want: H0W_MUCH_1_L0v3_H hmm note seems interesting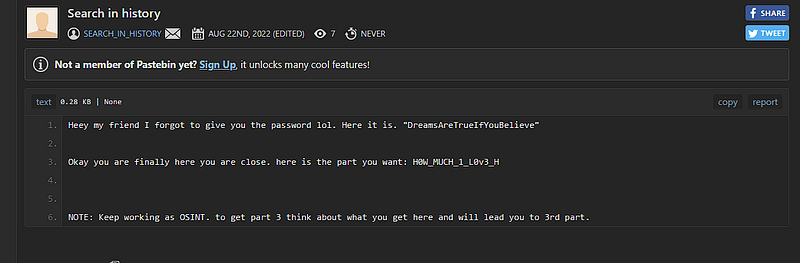
NOTE: Keep working as OSINT. to get part 3 think about what you get here
and will lead you to 3rd part.keep osint hmmm. let’s try our osint tools and see if we will get something or not. after searching and using so many tools while using “instant username”. putting Part2 of the flag.
I noticed that there is “About.me” Link. let’s open it and see.
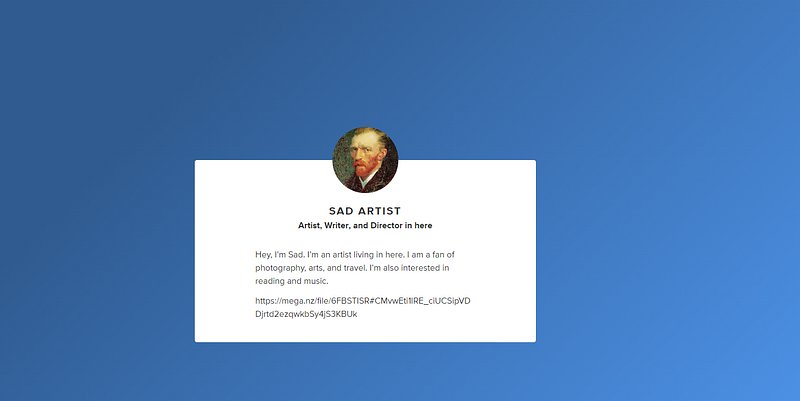 Boooom. we got it the way to 3rd part. a MEGA link so let’s download the files and see.
Boooom. we got it the way to 3rd part. a MEGA link so let’s download the files and see.
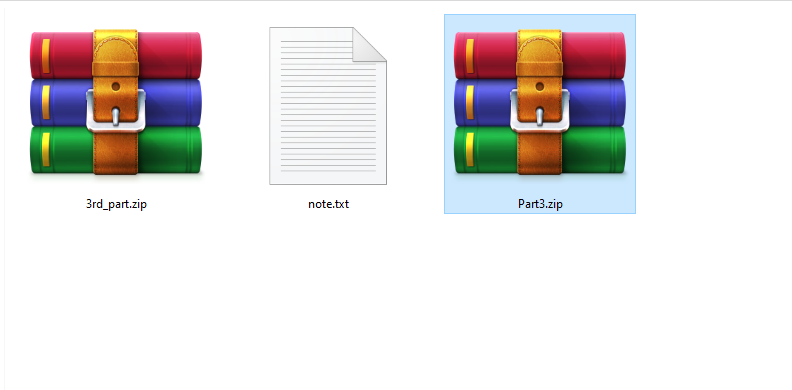 we got a zip file after extracting it. we got another zip and a note !! it says
where did he find the password of my pc???? go back and check where can
we got a zip file after extracting it. we got another zip and a note !! it says
where did he find the password of my pc???? go back and check where can
I find the password of my pc
hmmmm. I tried to brute-force the “3rd_part.zip” using “JohnTheRipper” and “rockyou” wordlist. but I got nothing. so I think the note will help me to find the password. so let’s google if we can find pc password in the registres. and I got this after some googling.
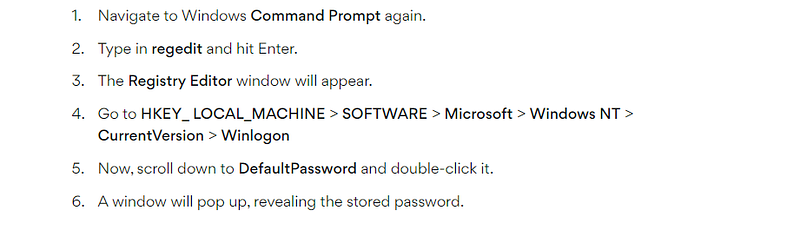 so let’s check this key in our registry we got.
so let’s check this key in our registry we got.
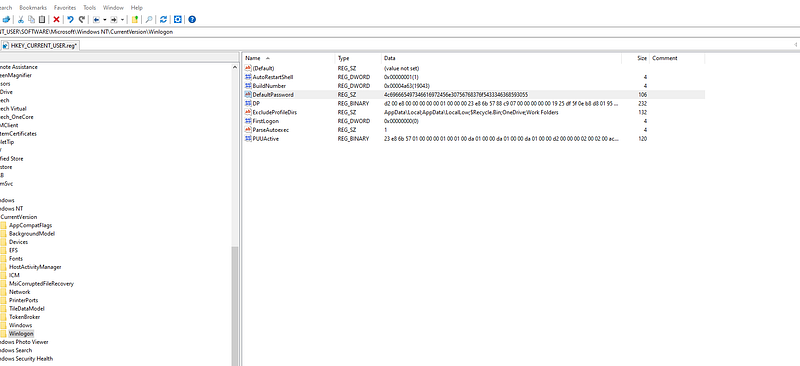 cool we found the “DefaultPassword” key. and seems sus so let’s unhex it.
cool we found the “DefaultPassword” key. and seems sus so let’s unhex it.
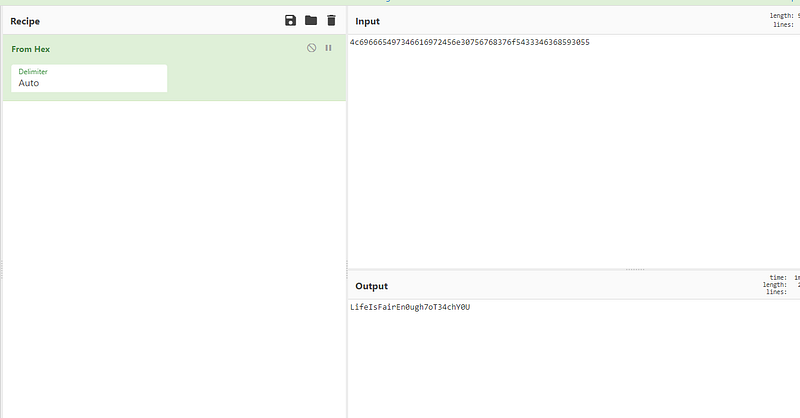 okay now we got the zip password of the “3rd_part.zip”. let’s extract it and get the 3rd part of the flag.
okay now we got the zip password of the “3rd_part.zip”. let’s extract it and get the 3rd part of the flag.
3rd Part : 3R_N0W_I_W1LL_L34V3_F0R_7H3_$PR1N6.}and we got now the full flag which is.
FLAG: OSC{Y0U_W0N'7_|<N0W_H0W_MUCH_1_L0v3_H3R_N0W_I_W1LL_L34V3_F0R_7H3_$PR1N6.}* _— — — — — — — — + — — — — — — — -+ — — — — +
| Challenge ===| Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Sylas_✔️ _|_ Steganography _| 25 |
| Witch_✔️ _|_ Steganography _| 25 |
| Chamber_✔️ _|_ Steganography _| 50 |
| MorsE_✔️ _|_ Steganography _| 50 |
| Viktor_✔️ _|_ Steganography _| 100 |
| Artist_✔️ _| Forensics | 200 |
+ — — — — — — — — + — — — — — — — -+ — — — — +_This is the end and I hope you enjoyed my challenges and writeups ^_^ have a nice day ❤ if u enjoyed follow me on social media.
By Ahmed Elessaway on November 15, 2022.