Published
- 12 min read
Jordan InfoSec CTF 2022 Qualifications writeups

Jordan InfoSec CTF 2022 Qualifications
Hello, It’s xElessaway, and this is my writeups for Forensics and misc challenges I’ve solved in Jordan InfoSec CTF2022…
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101 | Forensics | 50 |
| M4LD0C | Forensics | 50 |
| FitShing | Forensics | 100 |
| Strange | Forensics | 100 |
| Filterition-1 | Forensics | 200 |
| Filterition-2 | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — + — — — — — — — -+ — — — — +
1-Easy101 ( Forensics — 50 Points)
Okay in the challenge we got a “pcapng” file so let’s open it and go through streams.
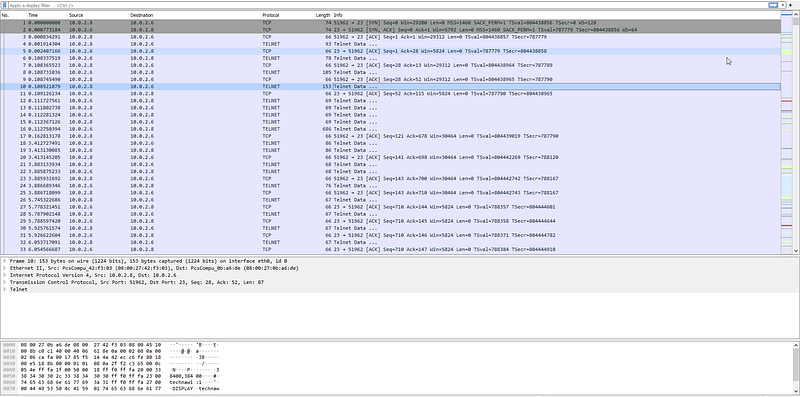 okay it contain a TCP protocol so let’s follow it (“CTRL + SHIFT + ALT + T”) in windows. let’s see if we will get something interesting.
okay it contain a TCP protocol so let’s follow it (“CTRL + SHIFT + ALT + T”) in windows. let’s see if we will get something interesting.
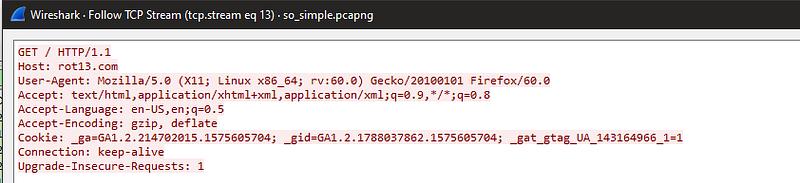 well. I noticed that in TCP Stream 13 contain rot13 encryption so this is interesting. so let’s keep up our search
well. I noticed that in TCP Stream 13 contain rot13 encryption so this is interesting. so let’s keep up our search
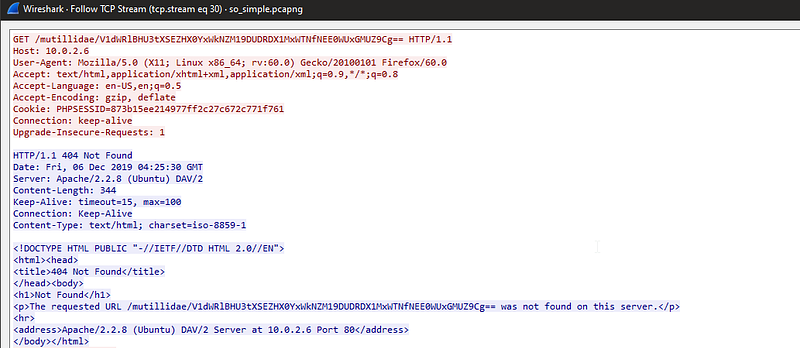 Ohhh. as we can see we found something encoded in headers so let’s try to decode it from base64.
Ohhh. as we can see we found something encoded in headers so let’s try to decode it from base64.
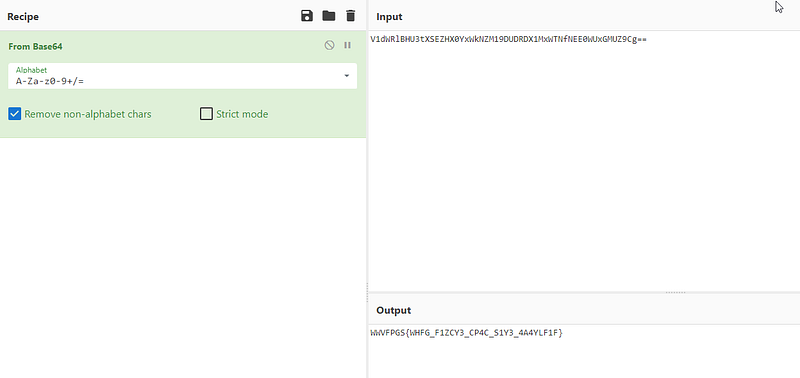 hmmm. it seems the flag but it’s not readable so let’s go back our hint!! ROT13 and try it.
hmmm. it seems the flag but it’s not readable so let’s go back our hint!! ROT13 and try it.
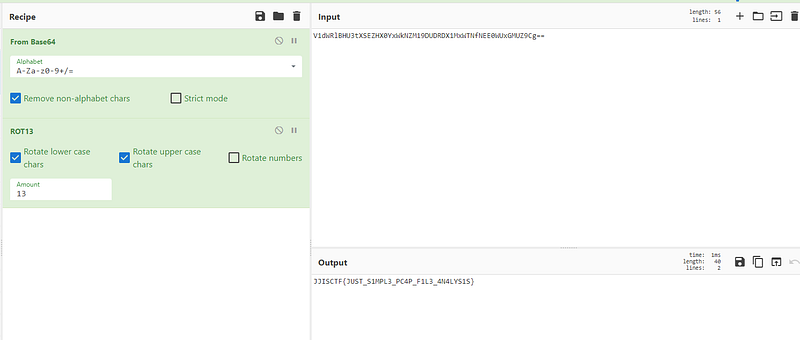 and Yes it was it. and here is the Flag
and Yes it was it. and here is the Flag
JISCTF{JUST_S1MPL3_PC4P_F1L3_4N4LYS1S}+ — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C | Forensics | 50 |
| FitShing | Forensics | 100 |
| Strange | Forensics | 100 |
| Filterition-1 | Forensics | 200 |
| Filterition-2 | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — + — — — — — — — -+ — — — — +2- M4LD0C ( Forensics — 50 Point )
okay let’s move to the second challenge and see what we get. and we get a (“docx”) File so what can should I try on a word file I’ve tried strings and some tools but the only thing I noticed that it contain some images. so let’s extract them. using binwalk
binwalk -e attachment.docx this is interesting. I know it’s a bar code so I’ll just decode it.
this is interesting. I know it’s a bar code so I’ll just decode it.
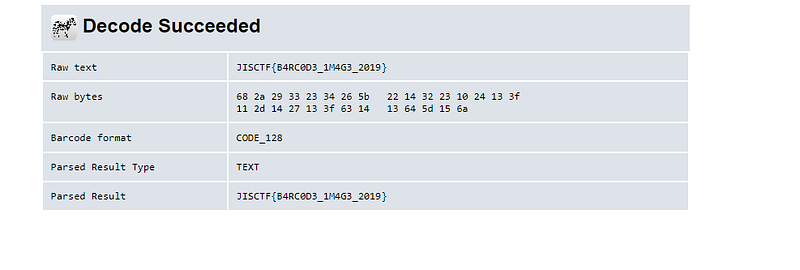 and yes that wasn’t hard we got the flag :DDDD
and yes that wasn’t hard we got the flag :DDDD
JISCTF{B4RC0D3_1M4G3_2019}* — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing | Forensics | 100 |
| Strange | Forensics | 100 |
| Filterition-1 | Forensics | 200 |
| Filterition-2 | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — + — — — — — — — -+ — — — — +3-FitShing( Forensics — 100 Point )
this challenge really killed me xDDD. I tried so many times but there was a problem in it. so let’s go into it. in this challenge we got a (“.pf”) file so I don’t know what is this file type so I tried use file command on it to check.
file FIREFOX.EXE-18ACFCFF.pf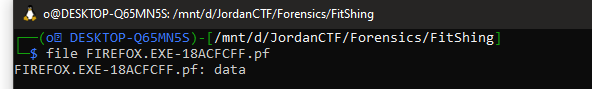 but nothing useful so I tried something maybe it works. I uploaded the file into cyberchef and it will auto detect. ( not working everytime I was just lucky xD )
but nothing useful so I tried something maybe it works. I uploaded the file into cyberchef and it will auto detect. ( not working everytime I was just lucky xD )
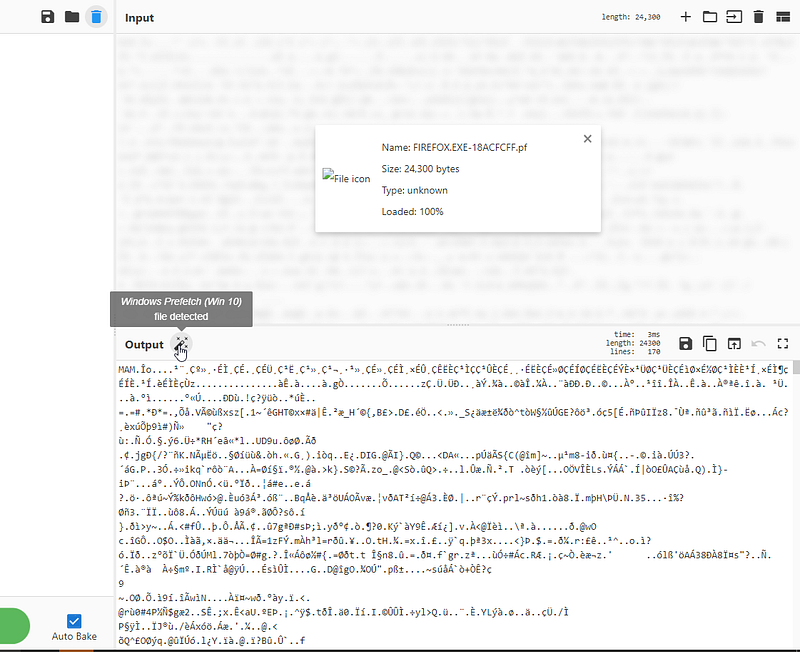
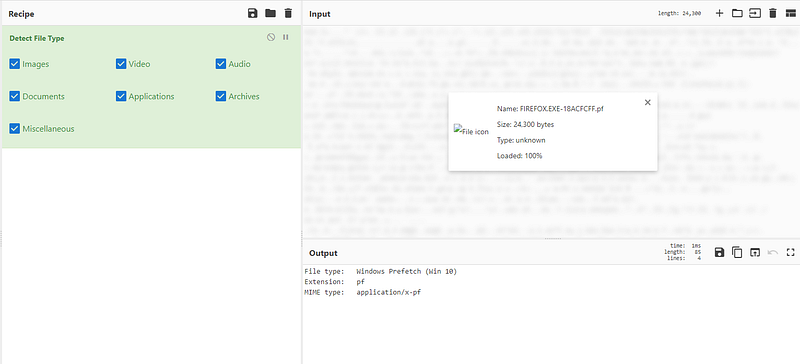 so yeah now we know it’s Windows Prefetch file so I did some googling about tools I can use and I got many tools but I used (“PEcmd.exe”). so yeah let’s try it on our cutie file :3
so yeah now we know it’s Windows Prefetch file so I did some googling about tools I can use and I got many tools but I used (“PEcmd.exe”). so yeah let’s try it on our cutie file :3
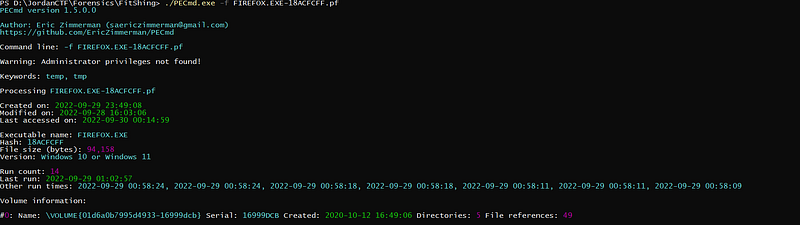 okay the tool solved the challenge without any unclear thoughts xD.
so the flag is
okay the tool solved the challenge without any unclear thoughts xD.
so the flag is
JISCTF{14_29–09–2022_04:02:57}* — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange | Forensics | 100 |
| Filterition-1 | Forensics | 200 |
| Filterition-2 | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — + — — — — — — — -+ — — — — +4- Strange ( Forensics — 100 Point )
this challenge is funny but really boring for me but I like it. so we got a (“pcapng”) so let’s do our analysis as we did before. but this time we notice something in UDP Protocol.
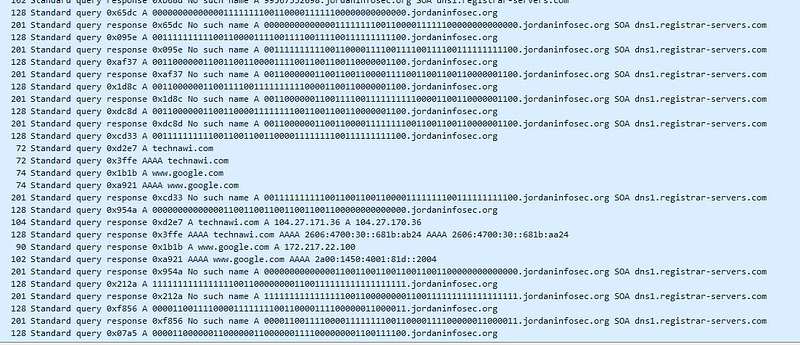 these 1’s and 0’s seems interesting so I extracted them manually ( that’s why it’s boring for me ) so here is the binary my friends :D
these 1’s and 0’s seems interesting so I extracted them manually ( that’s why it’s boring for me ) so here is the binary my friends :D
00000000000000111111110011000011111100000000000000
00111111111100110000111100111100111100111111111100
00110000001100110011000011110011001100110000001100
00110000001100111100111111111100001100110000001100
00110000001100110000111111110011001100110000001100
00111111111100110011001100001111111100111111111100
00000000000000110011001100110011001100000000000000
11111111111111110011000000001100111111111111111111
00001100111100001111111100110000111100000011000011
00001100000011000000110000001111000000001100111100
11001111111100001111110000001111000011110000110011
00110011000011001100001111001100000011000011110011
11001111000000001111001111111100000000110011001111
11110000000011000011111111000000110000000000111111
00110000111100000011110011111100000000111111110011
11001100001111110000000000111100111111001100110000
00000000001100110000001100001100000000000000110000
11111111111111110011001100110000001111110000110000
00000000000000110011000000111111001100110011001100
00111111111100111100110011110011001111110011001100
00110000001100111111111111111111000000000011110000
00110000001100110000000011000011111111111100110011
00110000001100111111111111000011110011000000111100
00111111111100110011111100001111110000110011001100
00000000000000110000000011001100111100001111111100so I tried to decode them to ASCII but nothing useful as well so that disappointed me a little bit. but after reading file name (“mysquare”)hmmmmm ( what if it’s a binary to image )
so yea let’s try we are not losing anything.
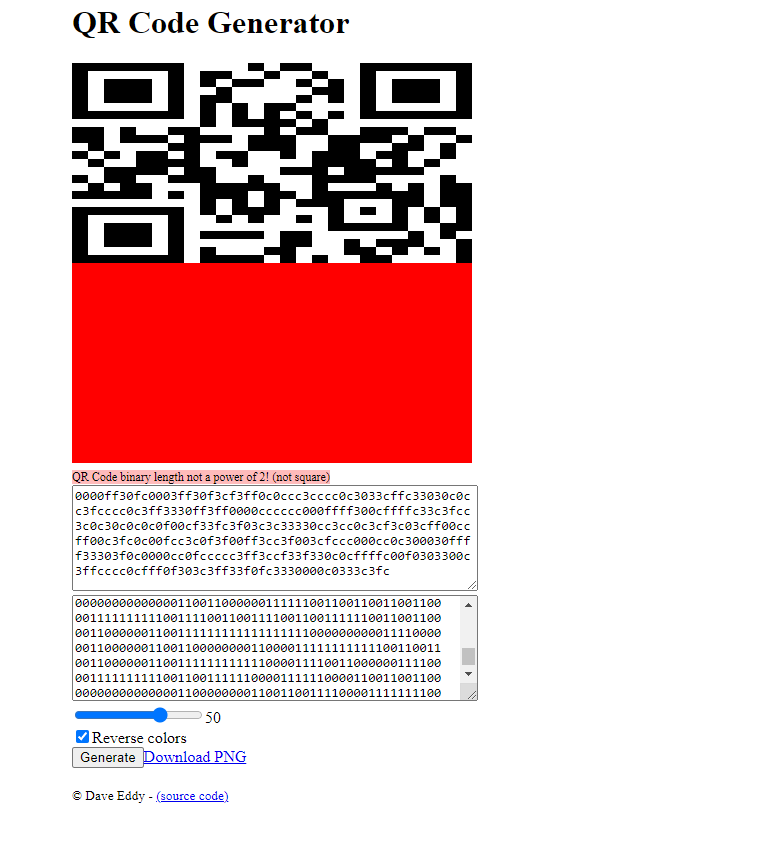 Oh yeaaah. we got a qr so let’s try to decode it.
Oh yeaaah. we got a qr so let’s try to decode it.
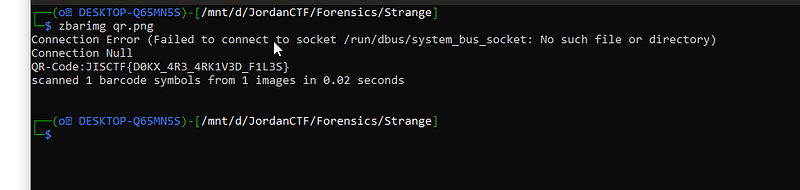 oh hello mr.flag I miss you so much :D
oh hello mr.flag I miss you so much :D
JISCTF{D0KX_4R3_4RK1V3D_F1L3S}* — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange✔️ | Forensics | 100 |
| Filterition-1 | Forensics | 200 |
| Filterition-2 | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — + — — — — — — — -+ — — — — +5-Filterition-1 ( Forensics — 200 Point )
oh 200 point so challenges become more hard right now :D. so in this challenge we got a (“pcapng”) file so let’s do our process open it and go through streams like TCP and UDP. I only notice that it used hex-converter. so let’s put this on my hint list maybe we need it for later.
so I found some streams in “ICMP” Protocol
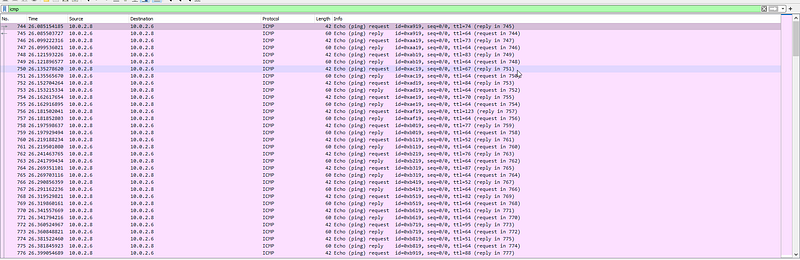 so I read more about it and I know now that ICMP means ping protocol. so let’s go through data. and I found something interesting really interesting.
so I read more about it and I know now that ICMP means ping protocol. so let’s go through data. and I found something interesting really interesting.
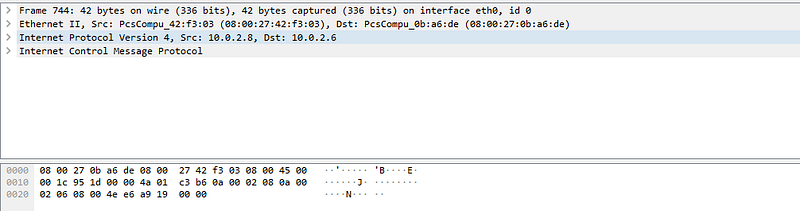 look ! we found “J” so let’s go to through others
look ! we found “J” so let’s go to through others
 and yes we got the flag but now we need to filter out these streams. we need only source sender (“10.0.2.8”). so I know that there are types of ICMP
and yes we got the flag but now we need to filter out these streams. we need only source sender (“10.0.2.8”). so I know that there are types of ICMP
 so let’s filter in wireshark and see.
so let’s filter in wireshark and see.
icmp && icmp.type == 8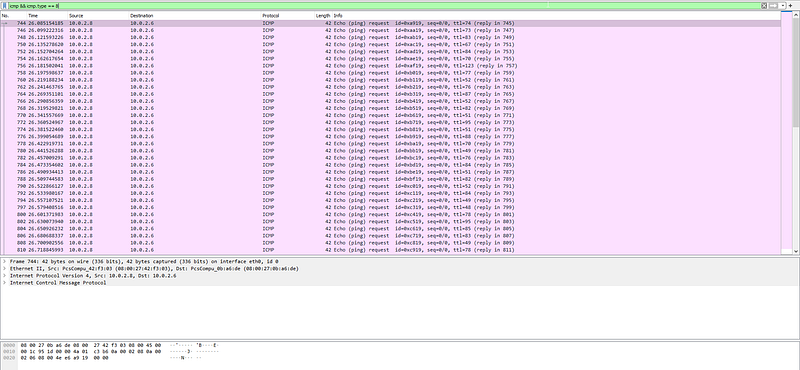 and yes we got the flag after get every character in the streams
and yes we got the flag after get every character in the streams
JISCTF{M4LW4R3_3XF1LT3R4T10N_US1NG_1CMP_TTL}* — — — — — — — — -+ — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — -+ — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange✔️ | Forensics | 100 |
| Filterition-1✔️ | Forensics | 200 |
| Filterition-2 | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — -+ — — — — — — — -+ — — — — +6-Filterition-2 ( Forensics — 200 Point )
Hello again ladies and gentlemen. we are back to another (“pcapng”) file so let’s do our simple techniques and see if we get something interesting.
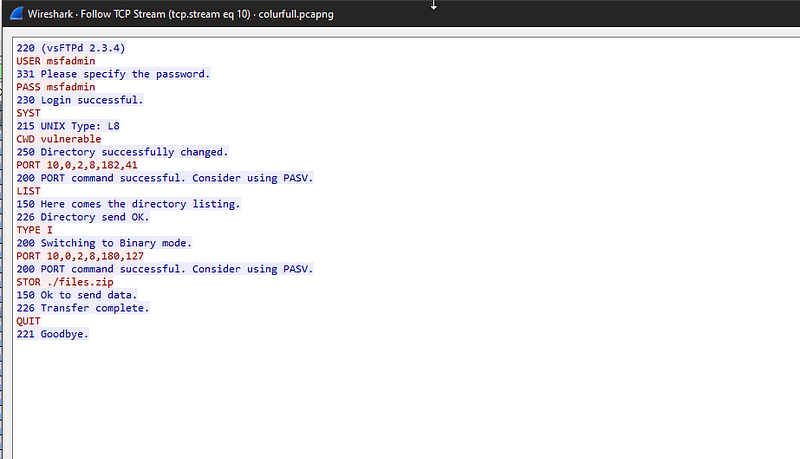 and this time we got something in TCP 10 “STOR ./files.zip” seems interesting so let’s continue to get the file.
and this time we got something in TCP 10 “STOR ./files.zip” seems interesting so let’s continue to get the file.
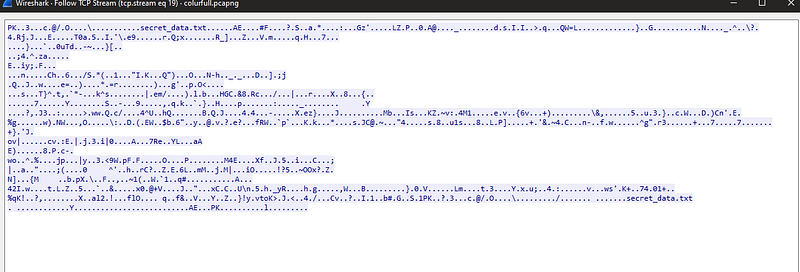 well here is the header of the file so I extracted it. to know what is the “secrect_data.txt”.
well here is the header of the file so I extracted it. to know what is the “secrect_data.txt”.
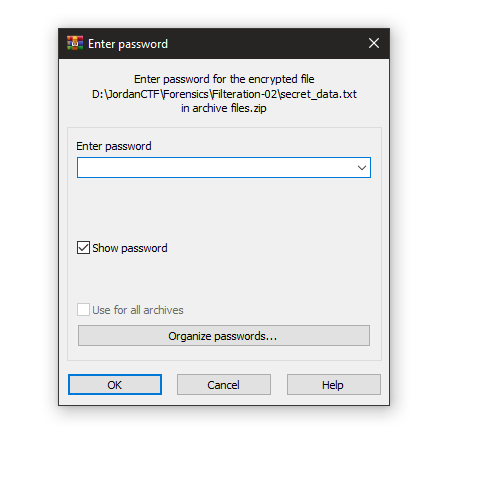 Okay now we need a password so we have 2 thoughts
Okay now we need a password so we have 2 thoughts
1st one is the password inside the pcapng file
2nd one brute force :V
so I’ll bruteforce first and see if we will get the password.
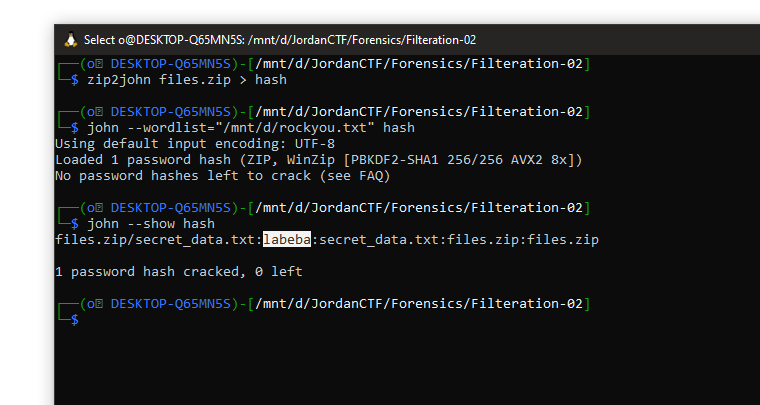 and yes we got the password my friends yaaaaay. now I can see the secret_data.txt
and yes we got the password my friends yaaaaay. now I can see the secret_data.txt
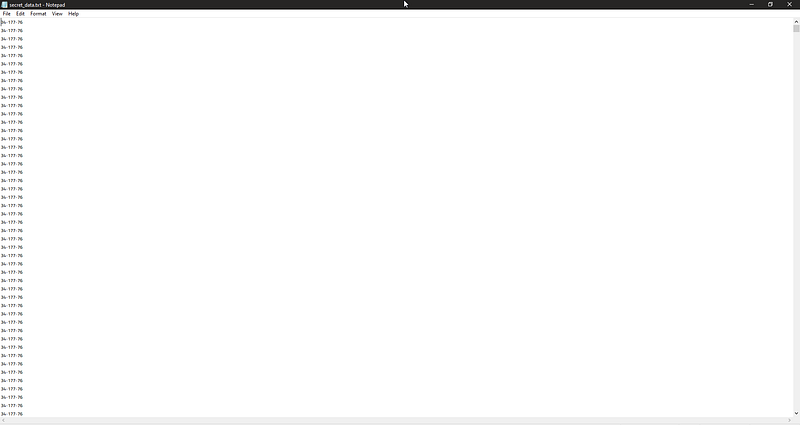 well I wish I didn’t see :’).
well I wish I didn’t see :’).
 okay okay after notice the file name is (“colorful”) hmmm maybe it’s RGB values ! so we I got an old script that will solve it for me :V
okay okay after notice the file name is (“colorful”) hmmm maybe it’s RGB values ! so we I got an old script that will solve it for me :V
from PIL import Image
*import pytesseract
pytesseract.pytesseract.tesseract_cmd = r’C:\\Program Files\\Tesseract-OCR\\tesseract.exe’
with open(“secret_data.txt”, “r”) as f:
d = f.read().split(“\\n”)
d.pop()
d = \[int(x) for y in d for x in y.split(“-”)\]
for x in range(280,300):
width = x
height = 200
c = d.copy()
for x in range(len(d), width\*height\*3):
c.append(0)
im = Image.frombytes(“RGB”, (width, height), bytes(c))
txt = pytesseract.image_to_string(im)
if len(txt) > 3:
print(width)
im.resize((1000,1000)).save(“img_{}.png”.format(width))and hi mr.image gimme my flaaaag
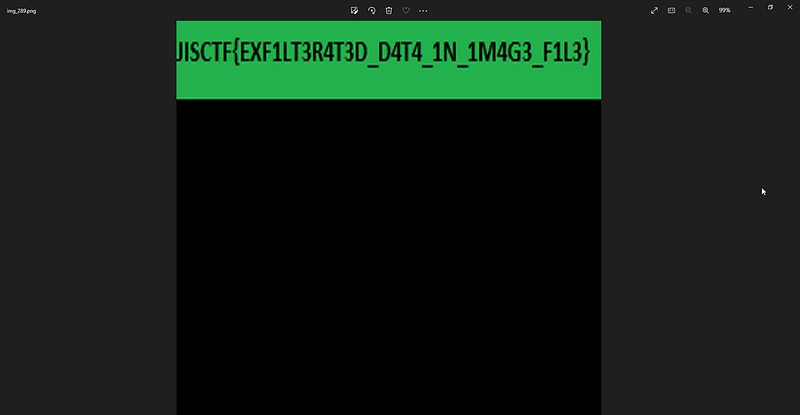
JISCTF{EXF1LT3R4T3D_D4T4_1N_1M4G3_F1L3}* — — — — — — — — -+ — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — -+ — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange✔️ | Forensics | 100 |
| Filterition-1✔️ | Forensics | 200 |
| Filterition-2✔️ | Forensics | 200 |
| WH4T-TH3-H1LL | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — -+ — — — — — — — -+ — — — — +7- WH4T-TH3-H1LL ( Forensics — 300 Point )
300 Point!!! okay baby you are mine. in this challenge we got a memory dump so it’s time guys yes it’s time to use our favorite tool “ volaility “ so let’s check the profile of this dump
python vol.py -f memdump.raw imageinfo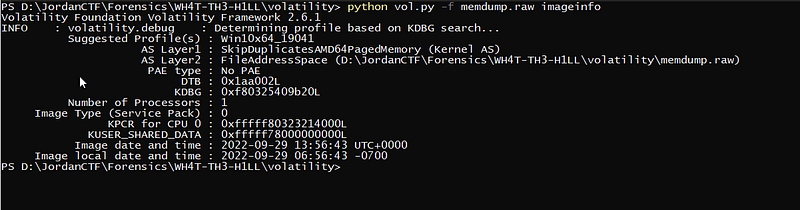 well it’s “Win10x64_19041” so let’s continue our job. and see the process list
well it’s “Win10x64_19041” so let’s continue our job. and see the process list
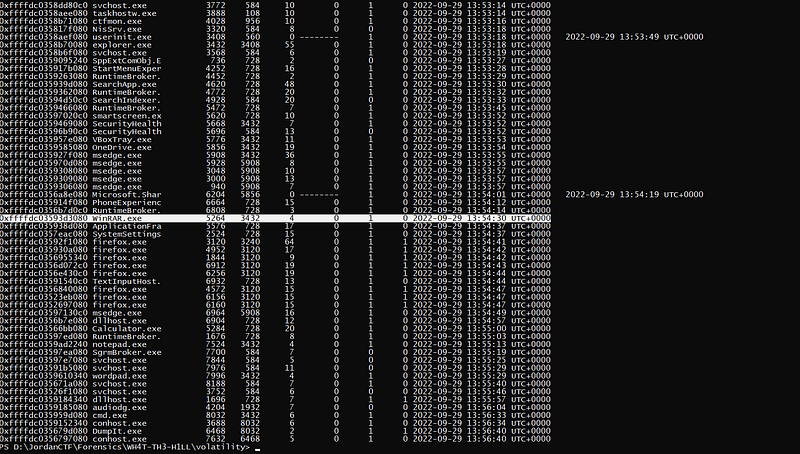 okay there are many process but I’ll focus on the “Winrar.exe” so let’s scan files and see if there are any zip or rar files we can dump.
okay there are many process but I’ll focus on the “Winrar.exe” so let’s scan files and see if there are any zip or rar files we can dump.
python vol.py -f memdump.raw — profile=Win10x64_19041 filescan > files.txt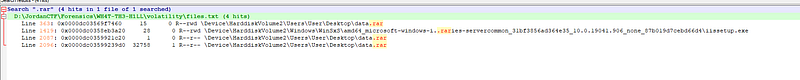 ohhh this is interesting. I found “Data.rar” so I’ll try to dump files on these files and see what will I get.
ohhh this is interesting. I found “Data.rar” so I’ll try to dump files on these files and see what will I get.
python vol.py -f memdump.raw — profile=Win10x64_19041 dumpfiles -Q \[offsets\] -D.but sadly we couldn’t dump these files nothing appear in the directory. so we have to go another way. I tried mftparser and trying to find “data.rar”
python vol.py -f memdump.raw — profile=Win10x64_19041 mftparser > mft.txt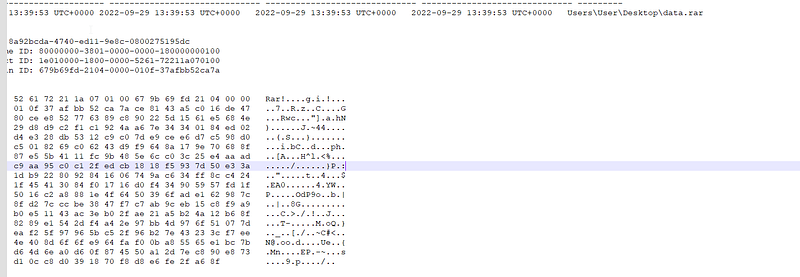 well well well for now we are good. we got our file :DD
well well well for now we are good. we got our file :DD
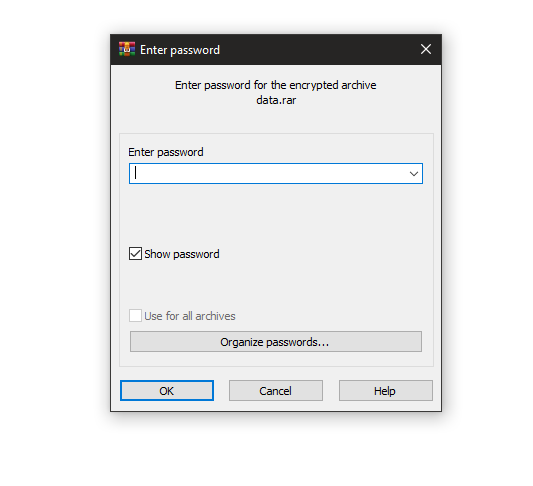 really :’) another password. so we have 2 thoughts.
really :’) another password. so we have 2 thoughts.
1st one password inside the dump
2nd one brute force
I’ve tried bruteforce but it will take long long long time so I know now we must go into the memory again to find that PASSWORD. so let’s see where can I find the password. maybe in cmd ? not there :/ maybe in history of browsers? nah not there too hmmmmm I asked the admin and he said where do u save the password. first I thought maybe it’s inside the broswer settings. but hmmm registry !!! how I forget that ! let’s check registry. using hivelist
python vol.py -f memdump.raw — profile=Win10x64_19041 hivelist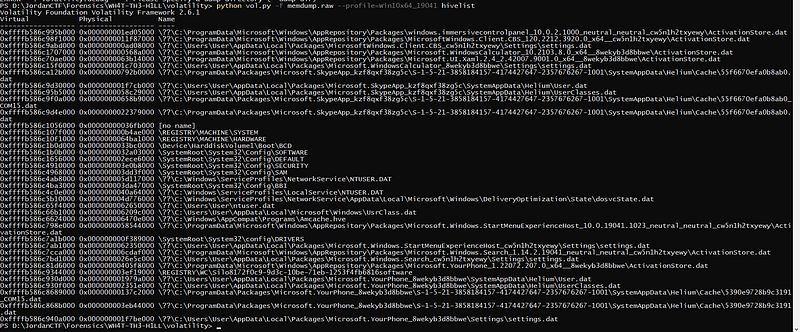 well well well we found the registries so as usual we google for where password are saved in registry
well well well we found the registries so as usual we google for where password are saved in registry
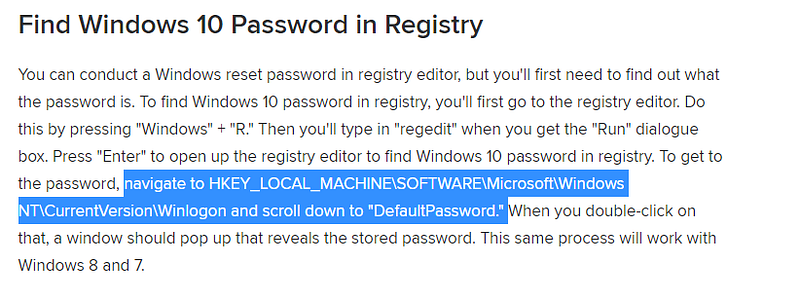 and now I know it’s in SOFTWARE so let’s dump that little one :DDD
and now I know it’s in SOFTWARE so let’s dump that little one :DDD
python vol.py -f memdump.raw — profile=Win10x64_19041 dumpregistry -o 0xffffb586c1b0b000 -D. so let’s open it in any registry viewer and see if we will find the password or not.
so let’s open it in any registry viewer and see if we will find the password or not.
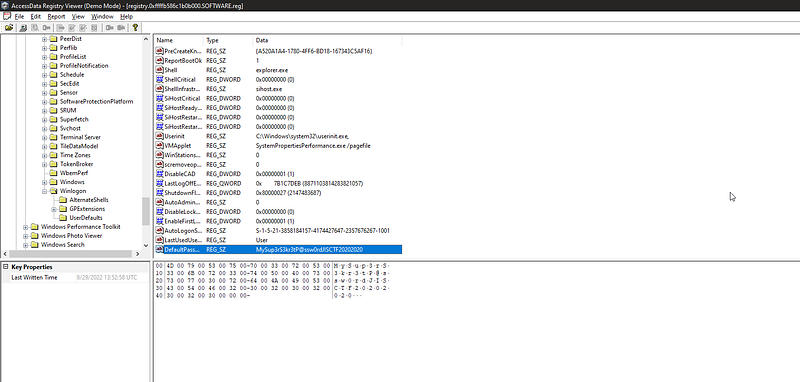 HELLO MY LITTLE FRIEEEEEEEND FINALLY WE GOT YOU.
HELLO MY LITTLE FRIEEEEEEEND FINALLY WE GOT YOU.
Password : **MySup3rS3kr3tP@ssw0rdJISCTF20202020**let’s extract and get the flag now :D
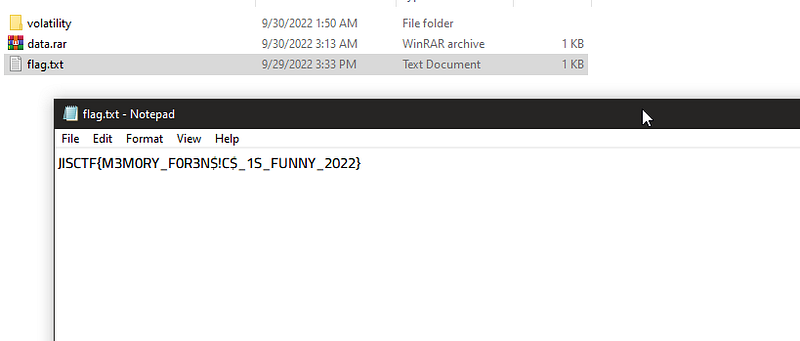
JISCTF{M3M0RY_F0R3N$!C$_1S_FUNNY_2022}* — — — — — — — — -+ — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — -+ — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange✔️ | Forensics | 100 |
| Filterition-1✔️ | Forensics | 200 |
| Filterition-2✔️ | Forensics | 200 |
| WH4T-TH3-H1LL✔️ | Forensics | 300 |
| BL4CK-0R-WH1T3 | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — -+ — — — — — — — -+ — — — — +8- BL4CK-0R-WH1T3 ( Steganography — 100 Point )
after completing the forensics challenges let’s move to steg challenges
in this challenges we got a (“jpg”) image so I tried some tools on it like exiftool,strings,binwalk etc but nothing useful so hmmm it’s time to try crack it using “Stegseek” using rockyou.txt.
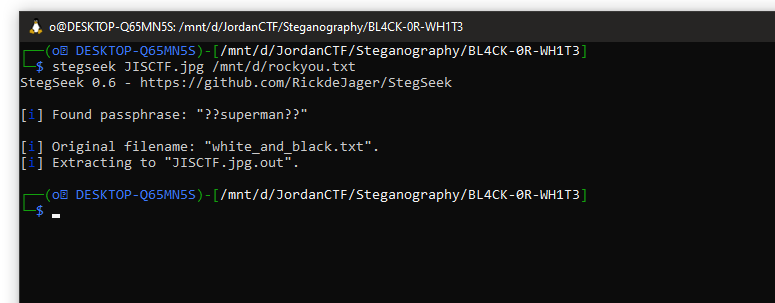 well hello little one :DDD
well hello little one :DDD
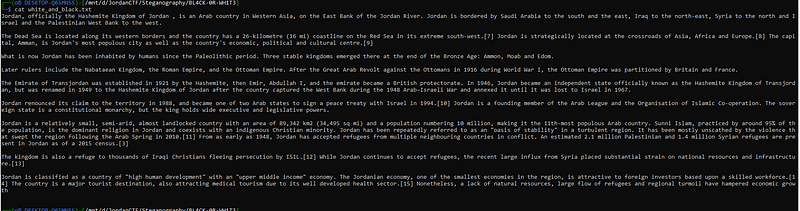 hmmm I don’t see anything useful for the flag but hmm there are a lot of spaces so maybe it’s whitespace language? but no it’s not. so I found “stegsnow” that check if there are any hidden message in the spaces.
hmmm I don’t see anything useful for the flag but hmm there are a lot of spaces so maybe it’s whitespace language? but no it’s not. so I found “stegsnow” that check if there are any hidden message in the spaces.
 oh hellp mr.flag :DDD
oh hellp mr.flag :DDD
JISCTF{Wh1t3_Sp4s3_St3g0_1s_C00l}* — — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange✔️ | Forensics | 100 |
| Filterition-1✔️ | Forensics | 200 |
| Filterition-2✔️ | Forensics | 200 |
| WH4T-TH3-H1LL✔️ | Forensics | 300 |
| BL4CK-0R-WH1T3✔️ | Steganography | 100 |
| C0MM0N 0R N0T | Misc | 100 |
+ — — — — — — — — — + — — — — — — — -+ — — — — +9- C0MM0N 0R N0T ( Misc — 100 Point )
last one :D in this challenge we got 2 (“.txt”) files so hmmmm from the title of the challenge we can notice that there are different characters between the two files. so I wrote this script to solve it
with open("file2.txt",'rb') as f:
data = f.read()
with open("file3.txt",'rb') as x:
data2 = x.read()
flag =''
for i in range(len(data)):
if data\[i\] == data2\[i\]:
pass
else:
flag += chr(data2\[i\])
print(flag\[::-1\])JISCTF{s0m3_c0mm0n_dt4_b3t33n_tw0_f1l3s_jisctf_2019}* — — — — — — — — — + — — — — — — — -+ — — — — +
| Challenge | Category | Points |
+ — — — — — — — — — + — — — — — — — -+ — — — — +
| Easy101✔️ | Forensics | 50 |
| M4LD0C✔️ | Forensics | 50 |
| FitShing✔️ | Forensics | 100 |
| Strange✔️ | Forensics | 100 |
| Filterition-1✔️ | Forensics | 200 |
| Filterition-2✔️ | Forensics | 200 |
| WH4T-TH3-H1LL✔️ | Forensics | 300 |
| BL4CK-0R-WH1T3✔️ | Steganography | 100 |
| C0MM0N 0R N0T✔️ | Misc | 100 |
+ — — — — — — — — — + — — — — — — — -+ — — — — +And this is the end and I hope you are really enjoyed my writeups ❤ #تحياتي