Published
- 1 min read
Hac-Sec 2021 Reprisal Writeup

| Details | |
|---|---|
| Points | 300 |
| Category | Digital Forensics |
Hac-Sec 2021 Reprisal Writeup
Okay first I download the file and it was pcap file, so I opened it and went through tcp streams till I found stream 4 include zip file
header and file name called = “da_op_files.zip”
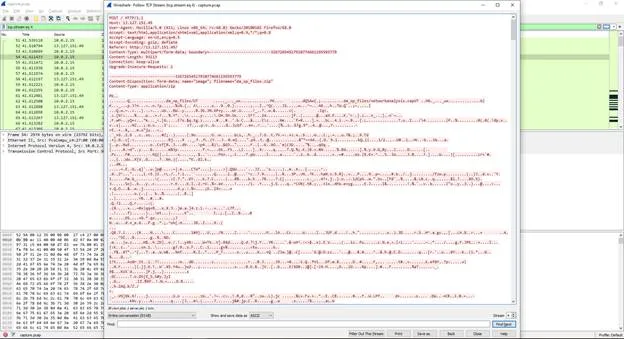 So I extracted this file by using network miner
So I extracted this file by using network miner
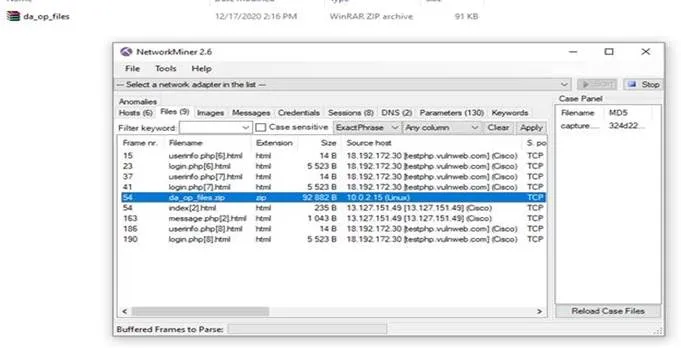 I tried to extract it but it had password so I tried
to use john on it but nothing so I back to tcp streams again and I found the password on
the 5th stream and it was “lls4f3s3cur1ty”
I tried to extract it but it had password so I tried
to use john on it but nothing so I back to tcp streams again and I found the password on
the 5th stream and it was “lls4f3s3cur1ty”
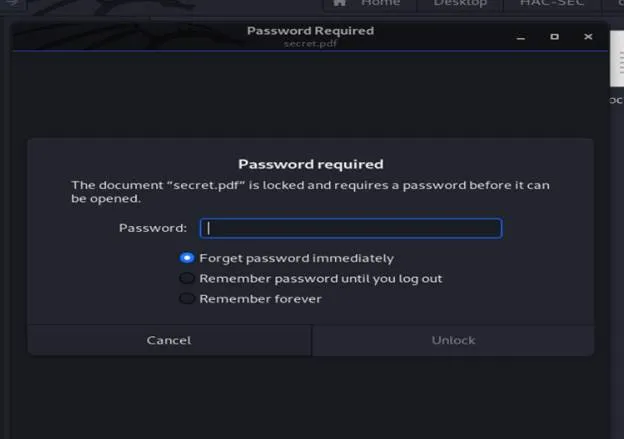
 So I extracted data and I got 1 pdf and 1 file so I checked the pcap file but nothing
interesting in it so I tried if there is any tool to crack pdf password
So I extracted data and I got 1 pdf and 1 file so I checked the pcap file but nothing
interesting in it so I tried if there is any tool to crack pdf password
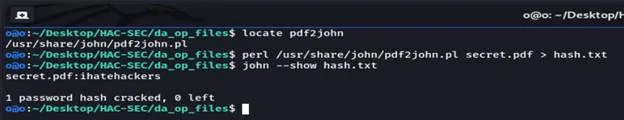
 I found that there is pdf2john.pl
So I tried it and I got the password = ihatehackers
I found that there is pdf2john.pl
So I tried it and I got the password = ihatehackers
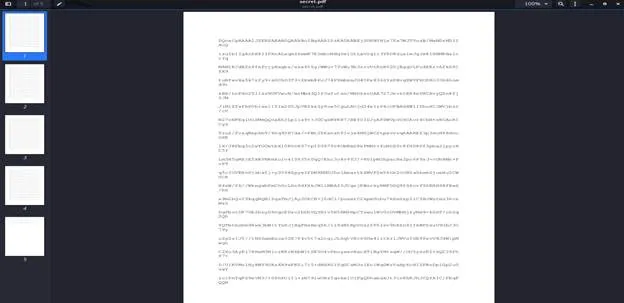
 So it’s looks like base64
So it’s looks like base64
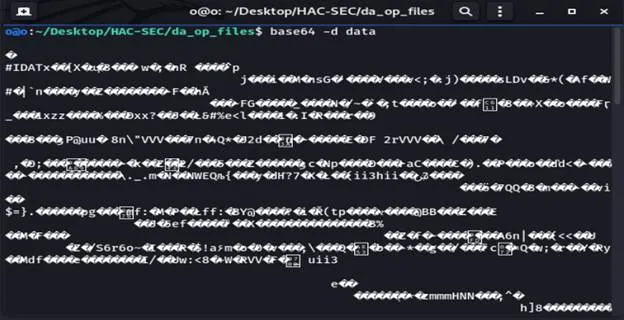
 So, I can see that it’s png from the header and footer
So, I can see that it’s png from the header and footer
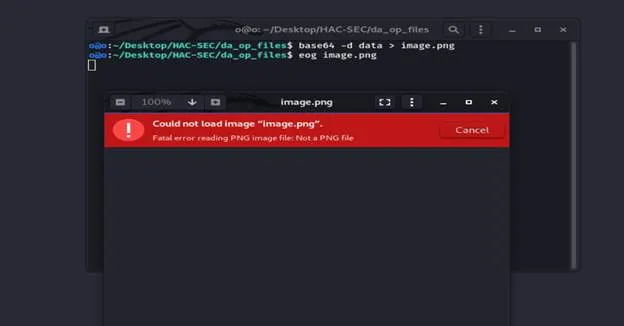
 So, after I used it wow it’s corrupted!!!
So, after I used it wow it’s corrupted!!!
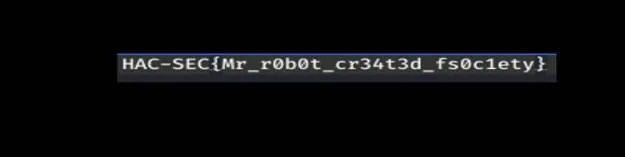
 So I started to fix it and boom the flag:
So I started to fix it and boom the flag: