CyberTelents New year CTF - Digital Forensics challenge - Mess ME
| Details | |
|---|---|
| Points | 200 |
| Level | hard |
| Category | Digital Forensics |
Mess Me
-
Mess me is a Digital Forensics challenge was in New Year CTF which is an encrypted zip file with a password and had 2 files called flag.jpg and oracle.vdi
-
first i used john and alot of tools to crack the password but nothing worked but it was a Plaintext-Based Attack
What is Plaintext-Based Attacks?
- it’s an attack model for cryptanalysis where the attacker has access to both the plaintext, and its encrypted version.
Attacking the zip file
*i used bkcrack tool to start this attack but the attack requires at least 12 bytes of known plaintext. At least 8 of them must be contiguous. The larger the contiguous known plaintext, the faster attack.
so we have flag.jpg and oracle.vdi and we should get a known plaintext for them
btw we can get a plaintext for the .vdi file using another vdi file so i already had a file called andro.vdi and i tried to read it
we got the first 20 bytes of “andro.vdi”
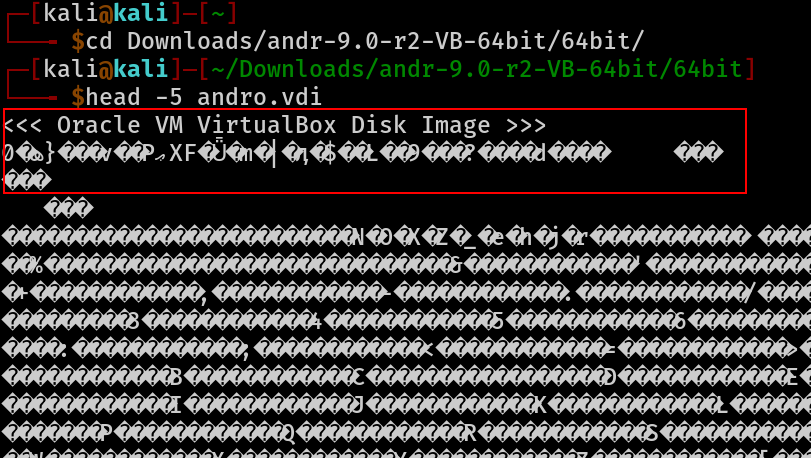
- note : 12-byte encryption header in prepended to the data in the archive. The last byte of the encryption header is the most significant byte of the file’s CRC.
and we can get the CRC using this command
unzip -Z -v Challange.zip oracle.vdi | grep CRC
and the result was “f63e7666”
- now putting them together
echo -n -e "\xf6<<< Oracle VM VirtualBox Disk Image >>>" > plain.txtand now let’s run the attack
./bkcrack -C Challange.zip -c oracle.vdi -p plain.txt -o -1after the tool finished i got this
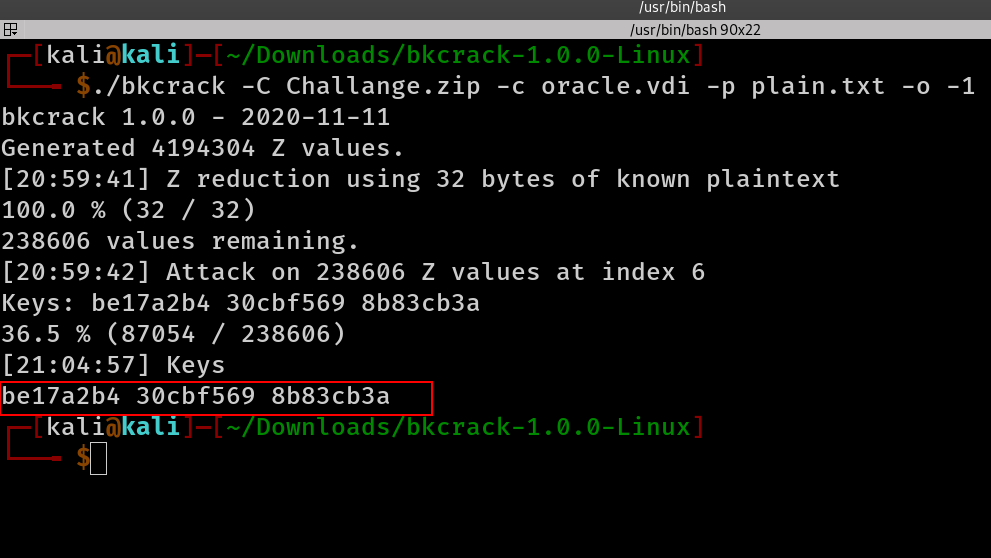
now we have the keys, we can decipher the files
./bkcrack -C Challange.zip -c oracle.vdi -k be17a2b4 30cbf569 8b83cb3a -d oracle.vdi

we got the oracle.vdi finally now let’s get the flag.jpg
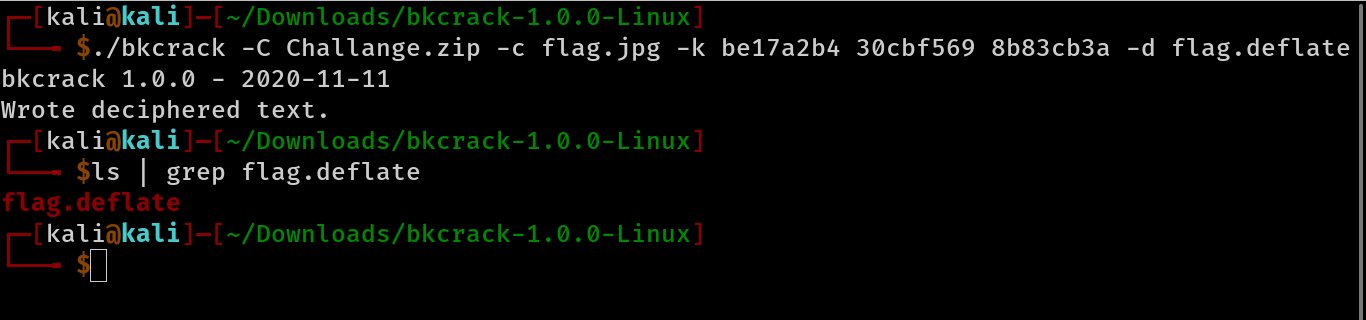
- The file flag.jpg was compressed with the deflate algorithm in the zip file, so we now have to uncompressed it and we can use inflate.py that comes with bkcrack
python3 tools/inflate.py < flag.deflate > flag.png
and we got the flag :)
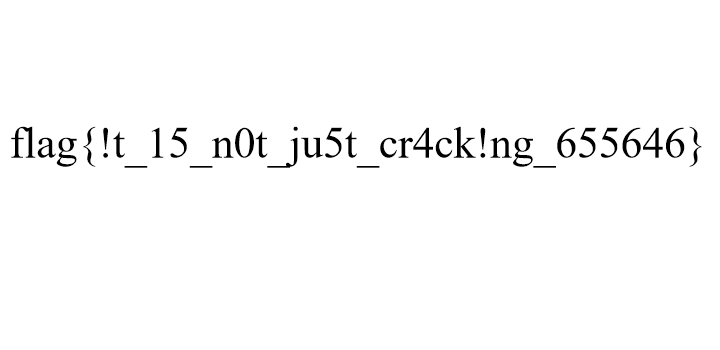
- cheers!
